PUADlManager Threat detection
PUADlManager is a threat detection moniker assigned by Windows Defender to classify threats with similar features and patterns. The threat name refers to computer items that have been discovered to aid the download and installation of PUAs on the system.
PUA, or Potentially Unwanted Application, is a rogue program that is installed on a computer without the user’s permission. They are frequently not what a user needs, therefore they are classified as unwanted, and these programs are eventually deleted sooner or later. The malicious software known as PUADlManager is the one that manages the download and installation of these apps.
Antivirus threat detection in general
Antivirus software uses large-scale databases that contain a vast number of known signatures and patterns for all known virus types, malware, ransomware, trojans, adware, and other dangerous software that malware hunters and researchers worldwide may have found in the wild.
Antivirus software typically uses these datasets. To detect and remove malware from a computer, they must first scan it and compare it to a database of unique signatures or identifiers for malicious software.
When an antivirus finds a file or application on a user’s computer whose signature matches one in the database, it destroys the malicious file. Similarly, an antivirus program may protect a computer in real time by scanning the system every few minutes for threat signatures contained in its database.
In this case, PUADlManager is considered a sub-category inside these databases since it is not a single threat that an antivirus may detect, but rather a collection of various threats that share the same name. Cybercriminals utilize the said malware to spread potentially unwanted applications, and with thousands of PUAs in circulation, the number of threats under PUADlManager grows.
Behavior of the threat
PUADlManager works by downloading and installing possibly undesired apps onto the computers it infects. Once within the system, it connects to a C2 server from which these programs are fetched. Often, these apps will be installed in the background of the computer system to avoid interruptions by the user. This is why undesirable apps frequently appear out of nowhere, with no indication of installation.
In other circumstances, the PUADlManager threat can be detected in third-party installers that include bundled programs in addition to the original installation materials. These are instances for executable installers that include optional sponsored apps, and many users mistakenly proceed without reading the fine print that they are also installing additional software on their computer.
PUADlManager malware threats
Windows Defender employs the heuristic threat detection term PUADlManager, also known as Potentially Unwanted Application Download Manager. As a result, the built-in Windows protection system will be the one detecting the majority of these threats.
Here are some of the most prevalent PUADlManager malware threats:
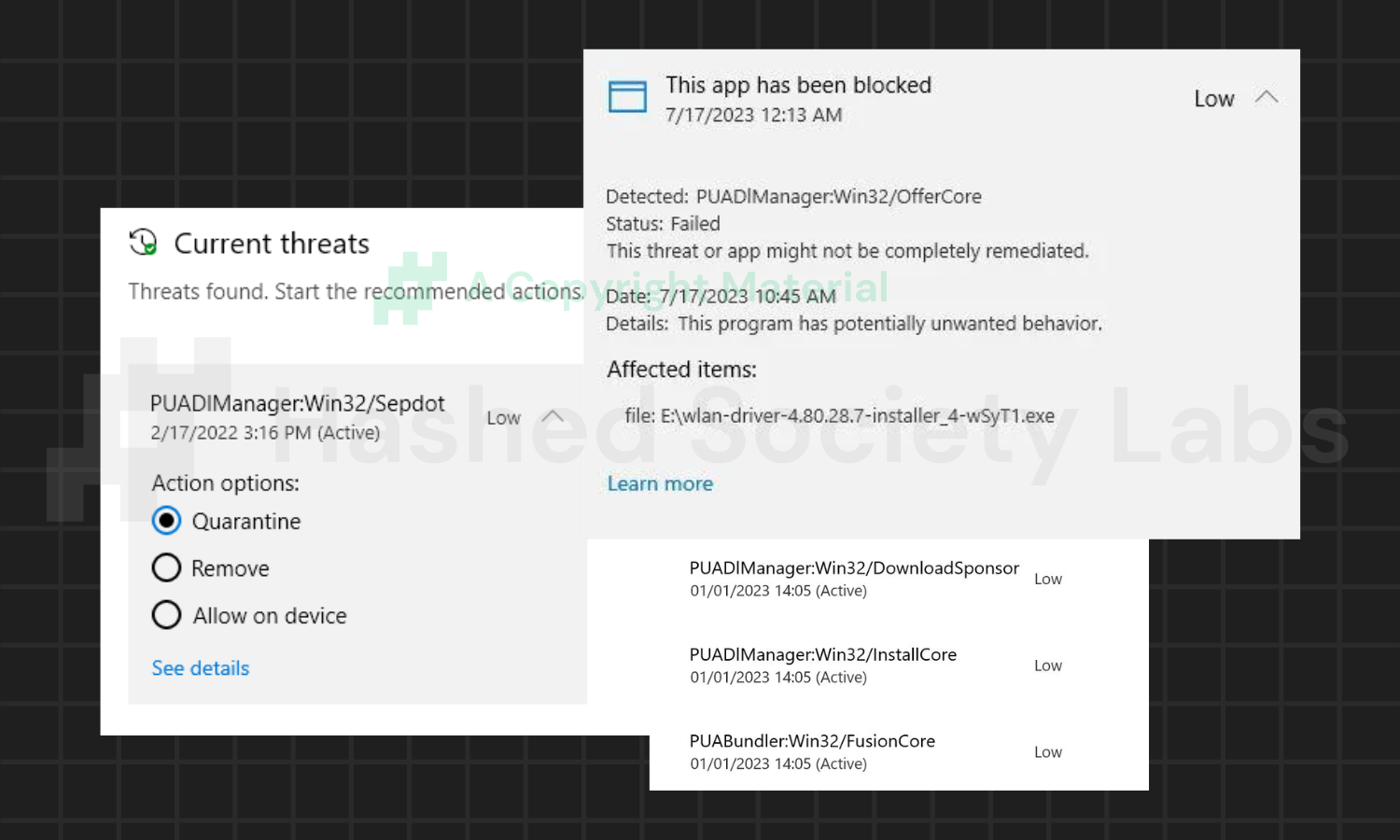
PUADlManager:Win32/Sepdot
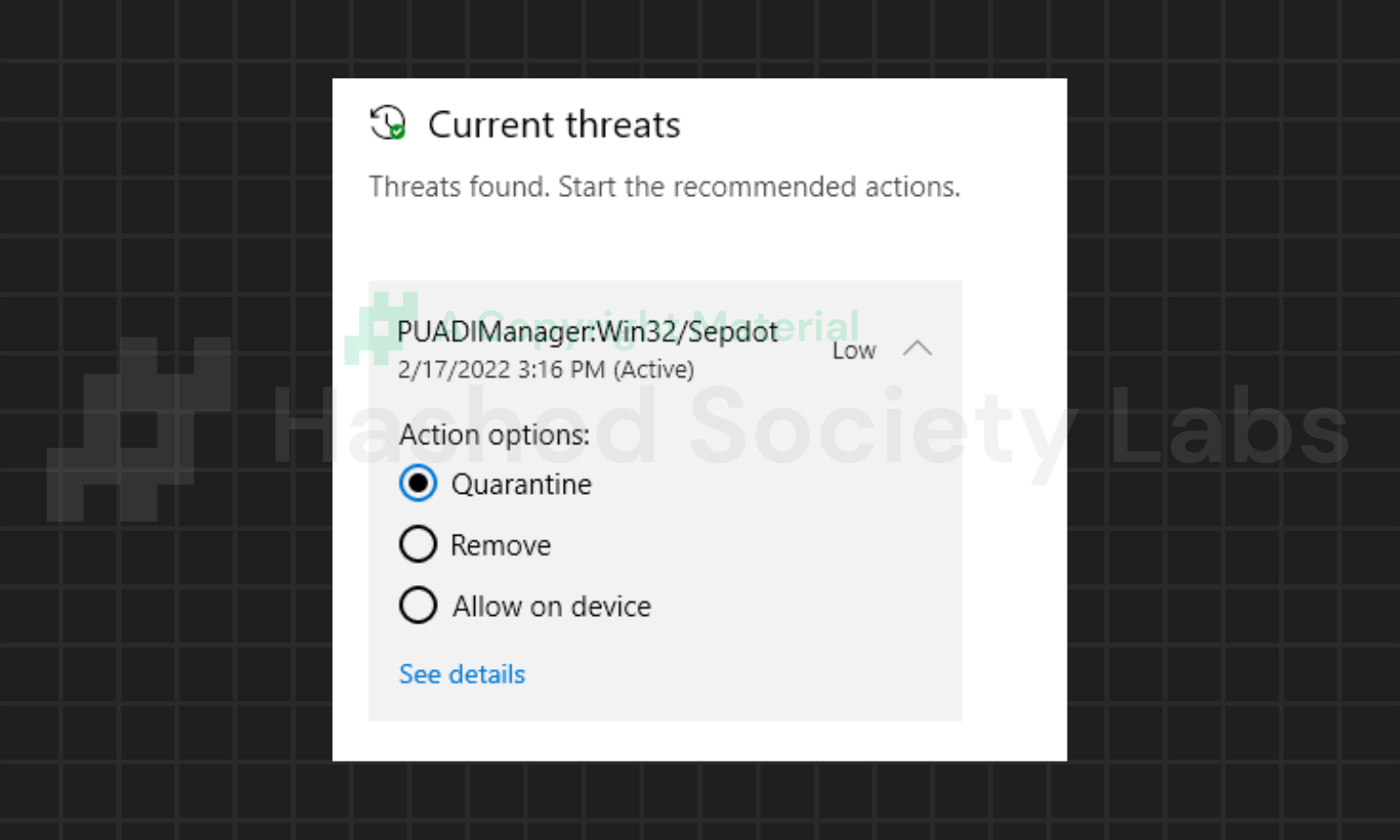
This threat suggests that it found a Trojan installer for the potentially unwanted software “Sepdot”. This means that Windows Defender may have detected a package installer, MSI file, or executable containing the aforementioned PUA, which will be installed on the machine when executed.
PUADlManager:Win32/DownloadSponsor
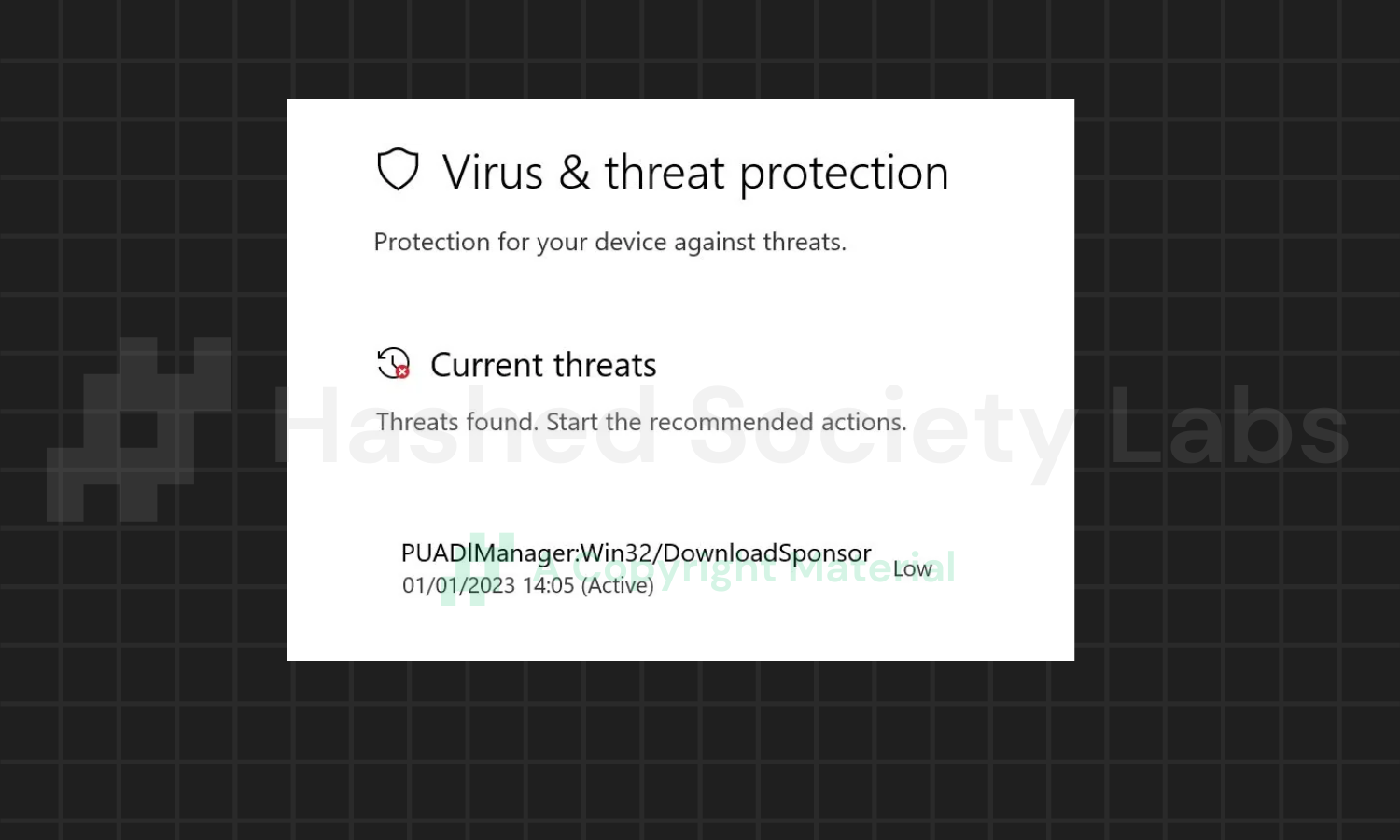
DownloadSponsor is another PUADlManager variant, and Defender flagged it as such since it detected an installer containing a generic application with a low reputation. It was determined that the app could have an impact on the quality of the computing experience, hence it was flagged.
PUADlManager:Win32/OfferCore
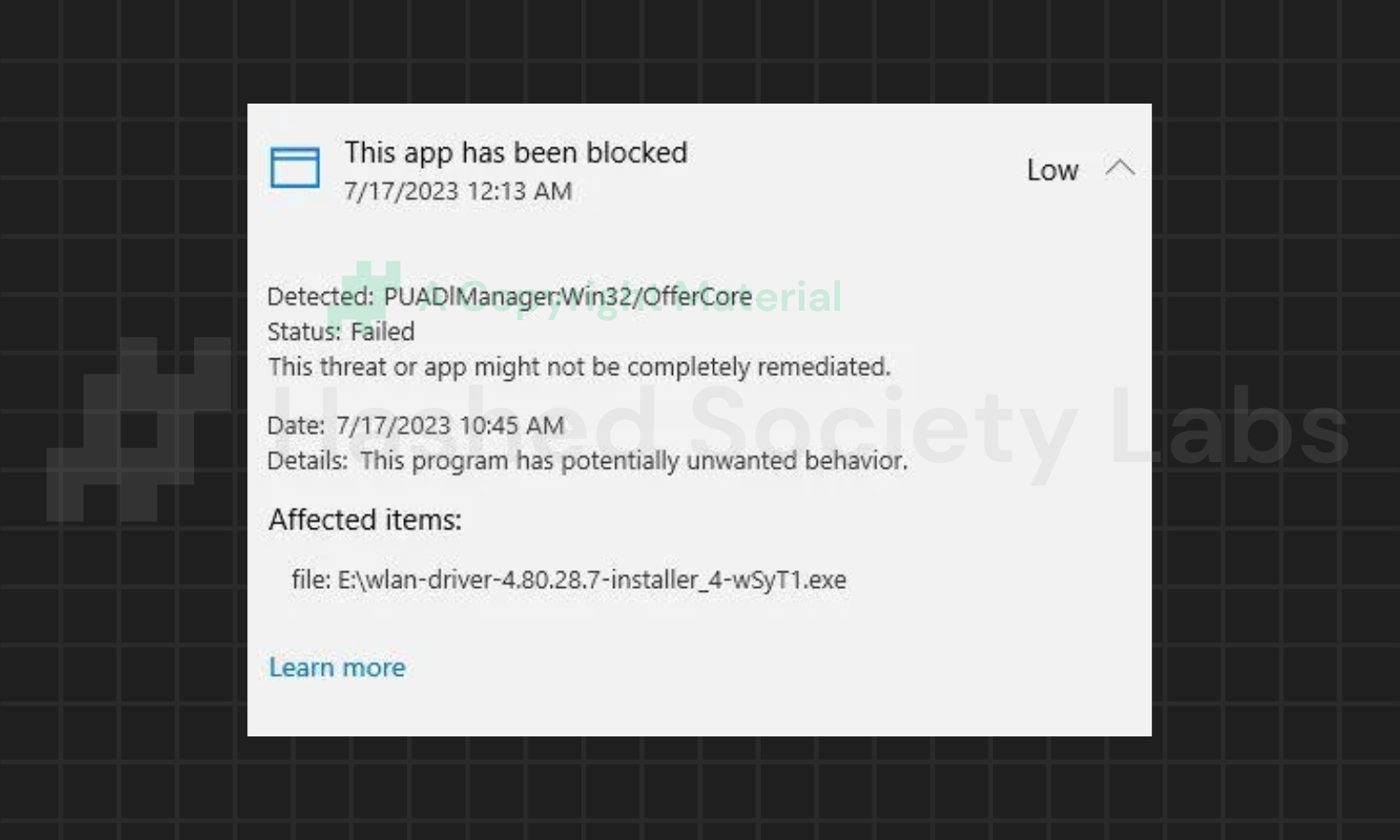
Windows Defender also detects OfferCore as associated with bundled software. It might have detected executable files with behaviors and features that are utilized for creating bundled apps and programs. This can include installing browser extensions, toolbars, adware, and system optimizers.
PUADlManager:Win32/Snackarcin
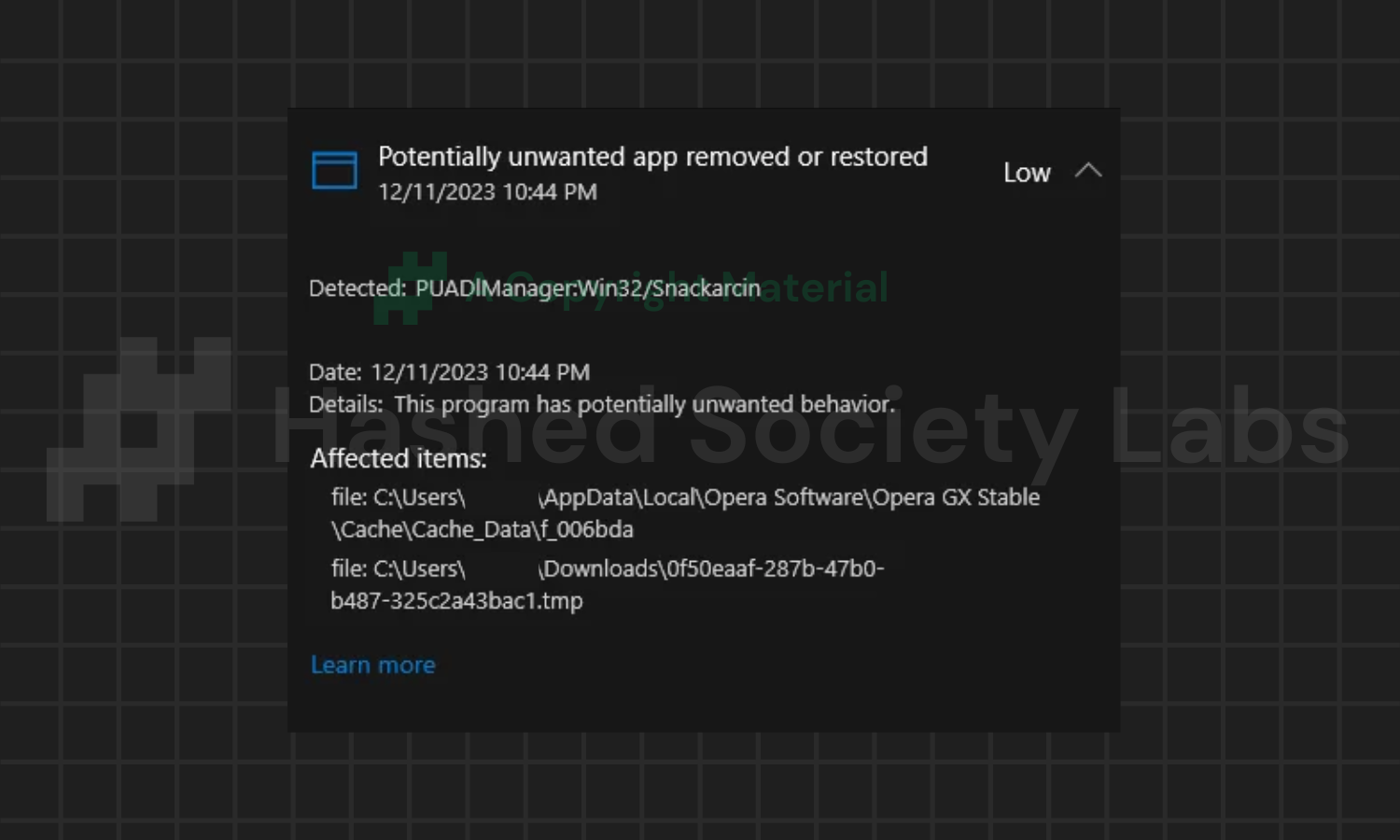
Snackarcin detection is another heuristic threat label that Windows Defender uses to identify executable files that it believes are malicious. In this situation, the majority of Snackarcin detections come from cracked/pirated games and software, which may contain potentially dangerous programs or, worse, malware and trojan viruses.
Distribution method
We noticed that the PUADlManager virus is regularly installed when users download malware-infected cracked torrents and pirated video games. These are the results of running a malware installation obtained from a common fake download webpage, which many people fall for. Furthermore, the aforementioned threat has also been found in genuine installers that includes bundled applications.
Summary of the threat
| Malware name | PUADlManager (PUA Download Manager) |
| Detection engine | Windows Defender |
| Delivery network | Drive-by download, infected torrents, and pirated software downloads |
| Malware behavior | Executes & install potentially unwanted applications to infected machines |
| Damage | Potential malware infection |
More about PUADlManager malware
PUADlManager is not a malicious threat in and of itself, as its primary function is to execute and install potentially undesirable programs on the computer system. However, the issue occurs when the program it installs is a harmful trojan virus and CPU-intensive coin-mining malware.
As a result, if you were infected with the aforementioned threat and Windows Defender was unable to remove it, we recommend that you take advanced action to delete both the PUADlManager virus and any other malware that may have been installed in your computer system. To completely remove malware from your computer, please follow our official malware removal instructions below.
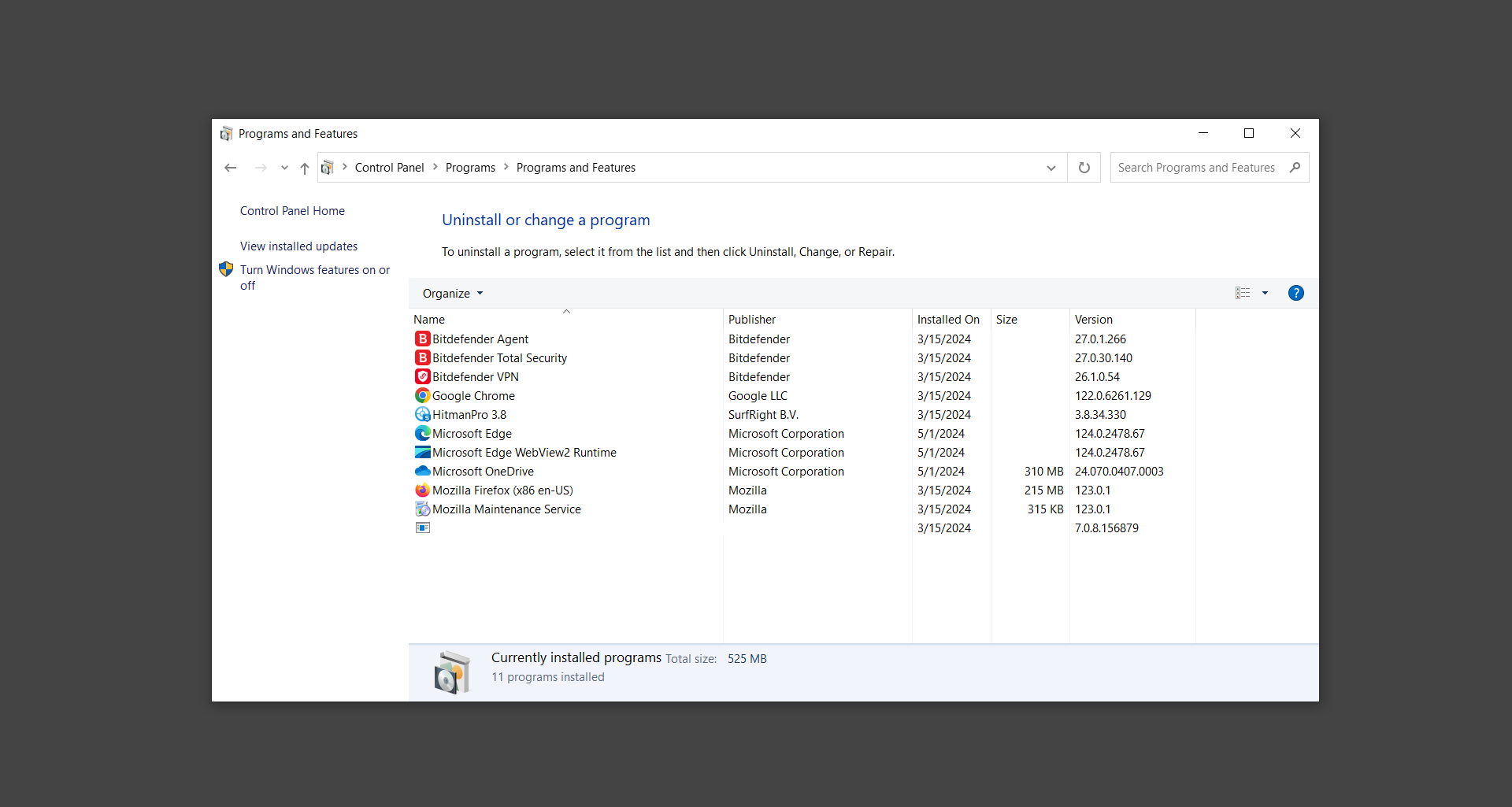
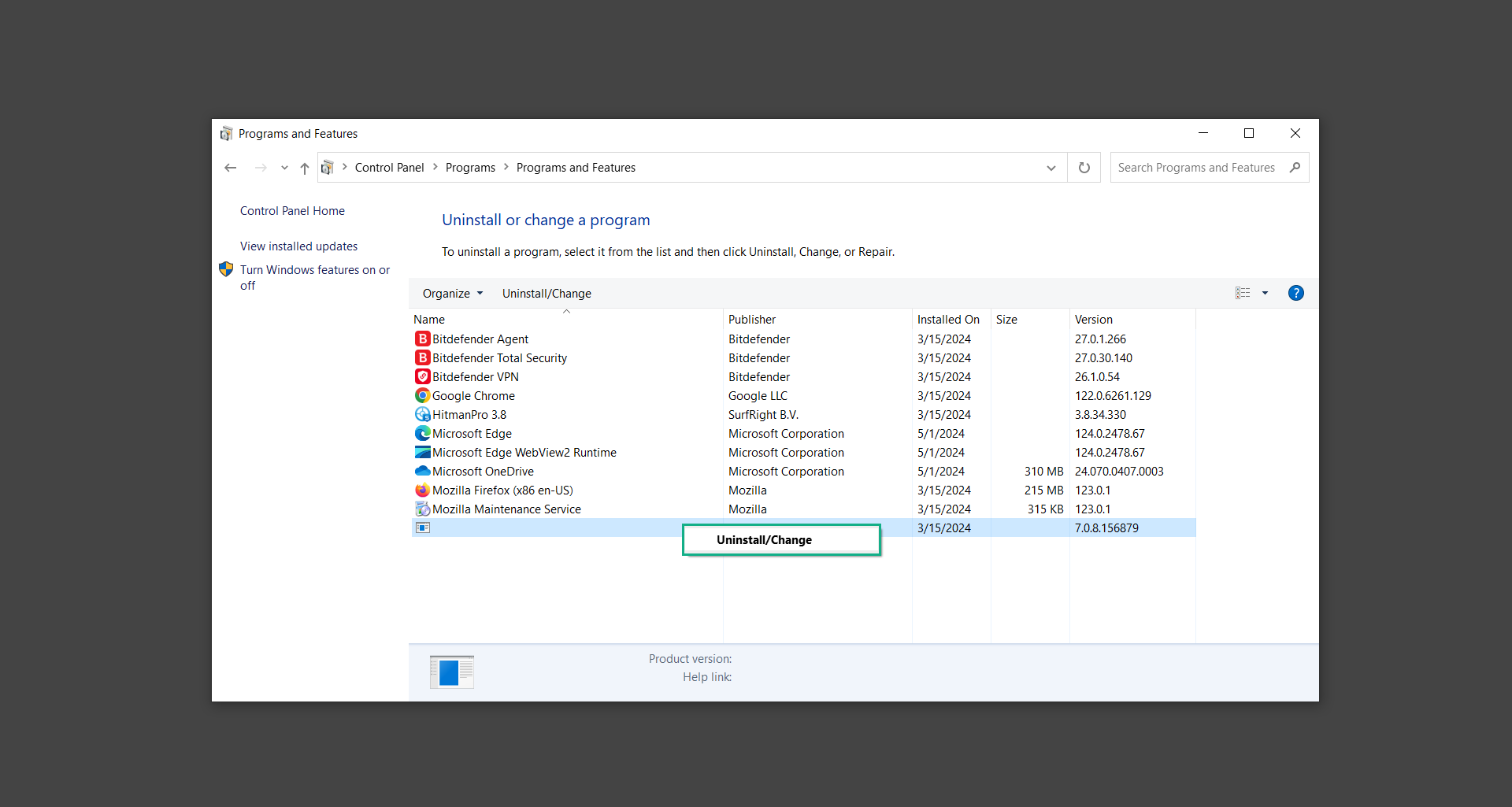
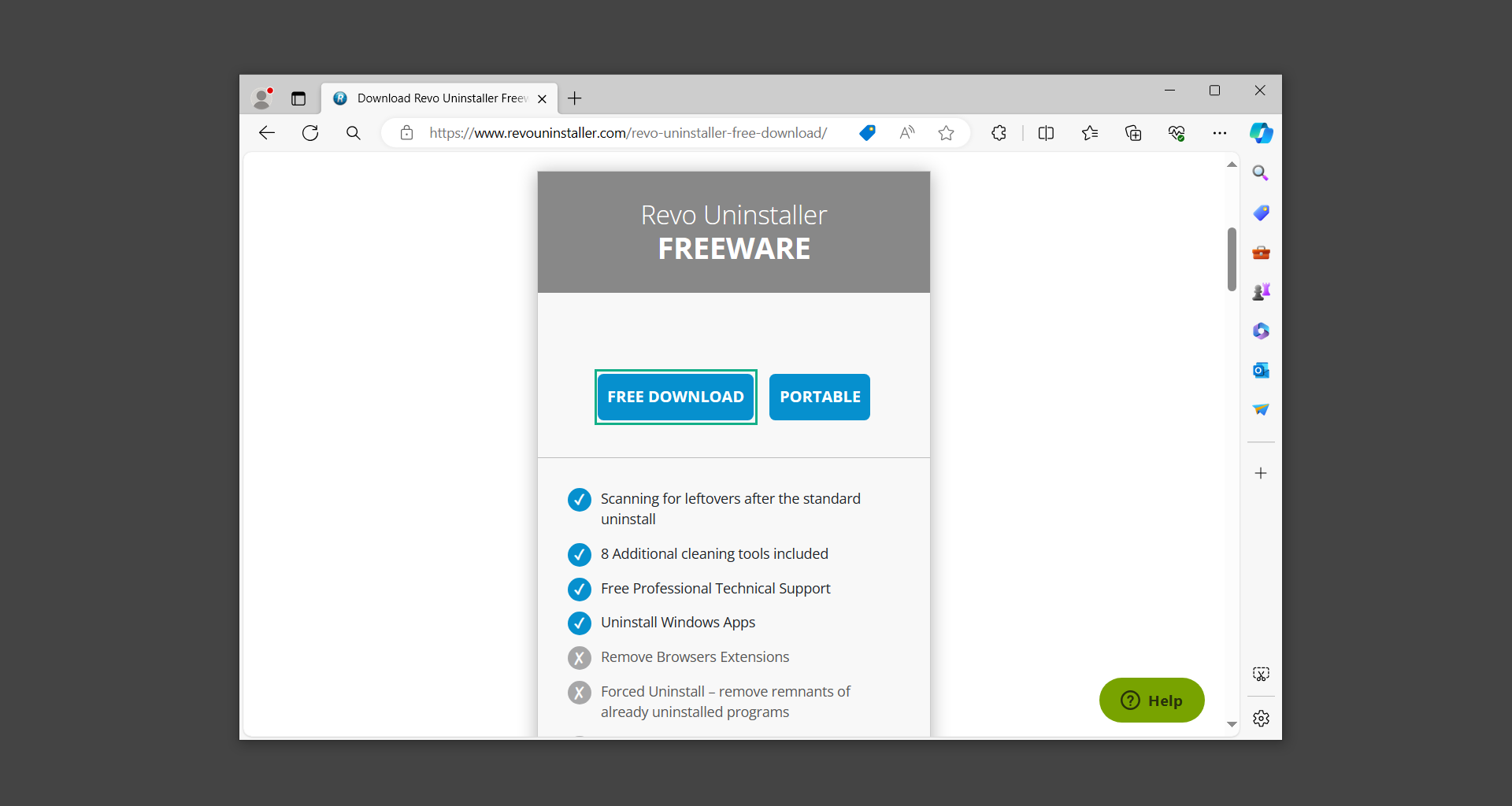
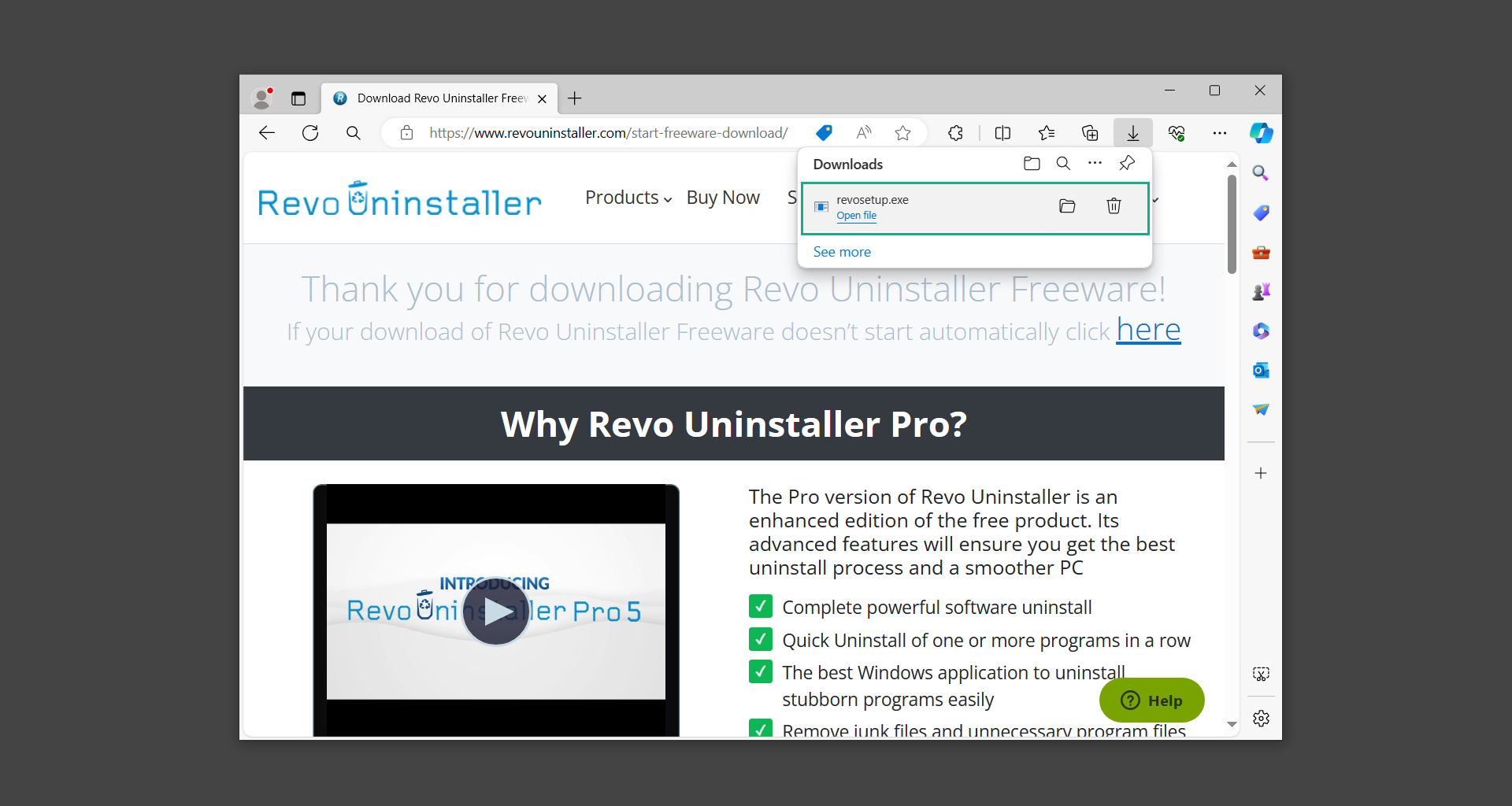
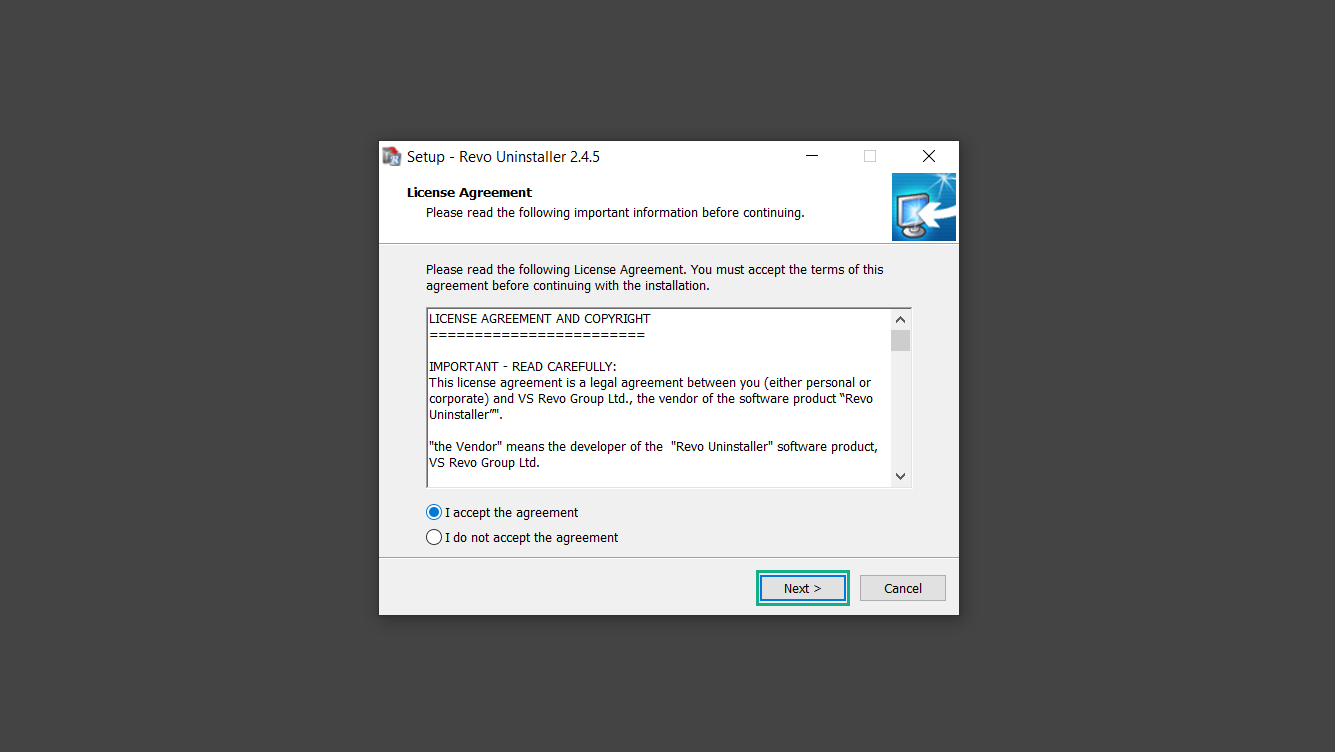
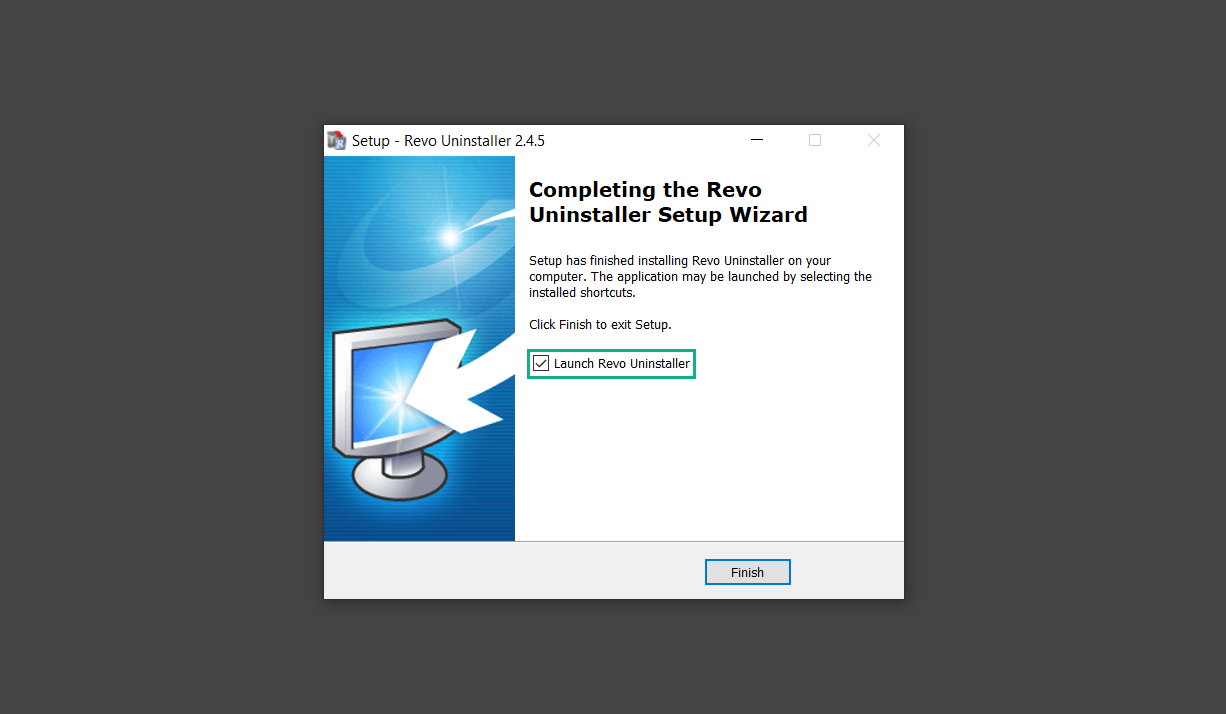
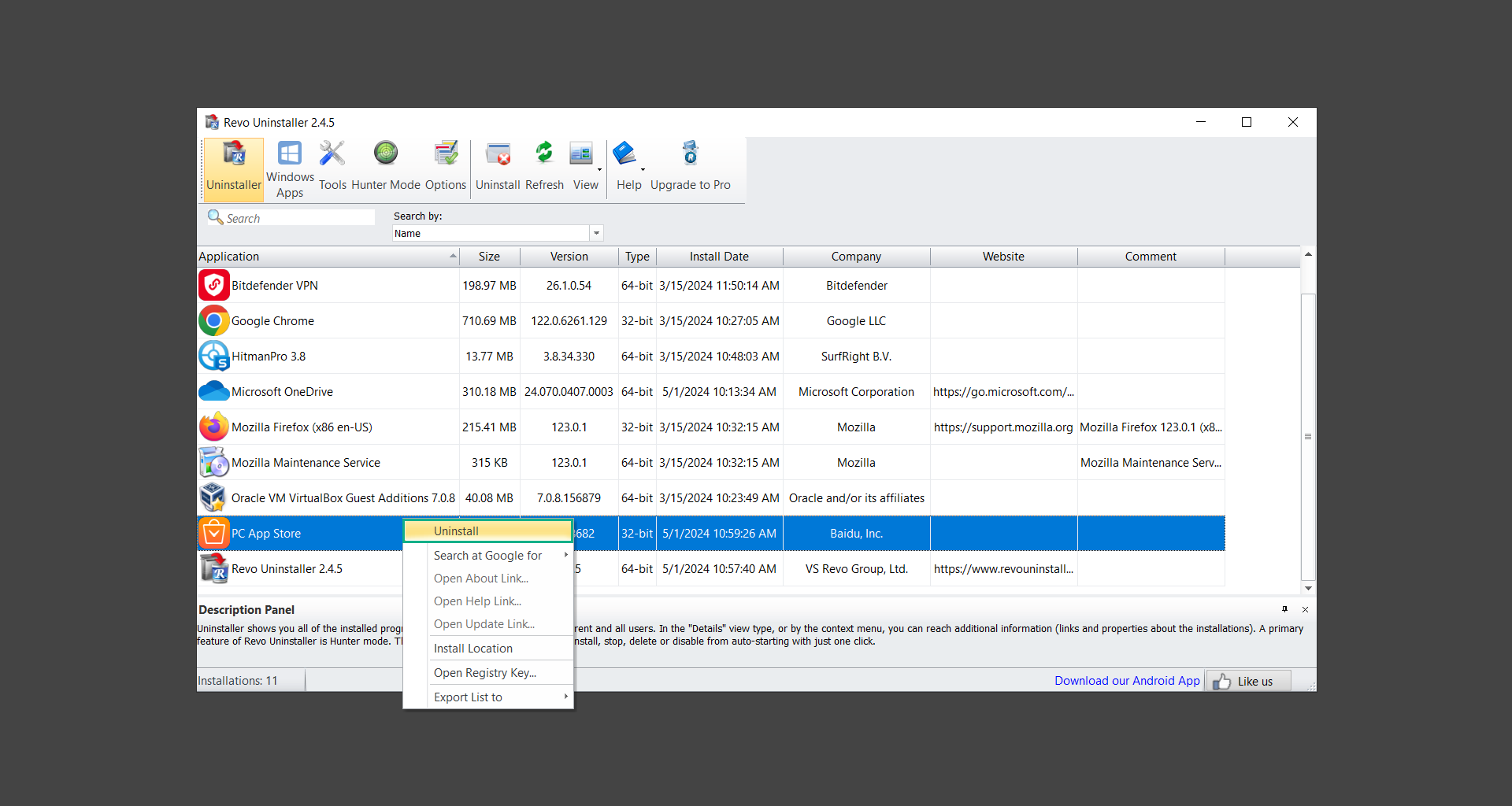
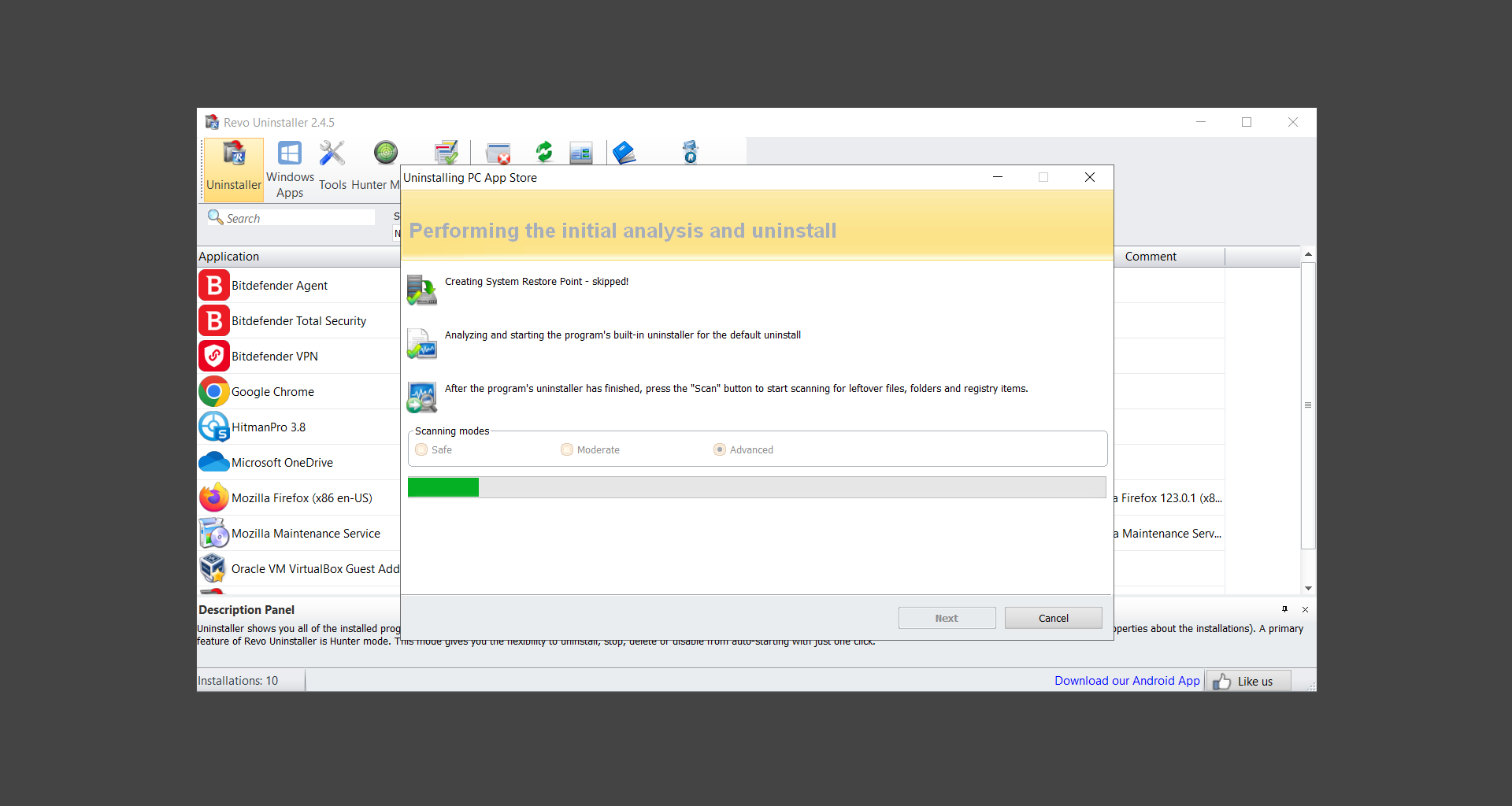
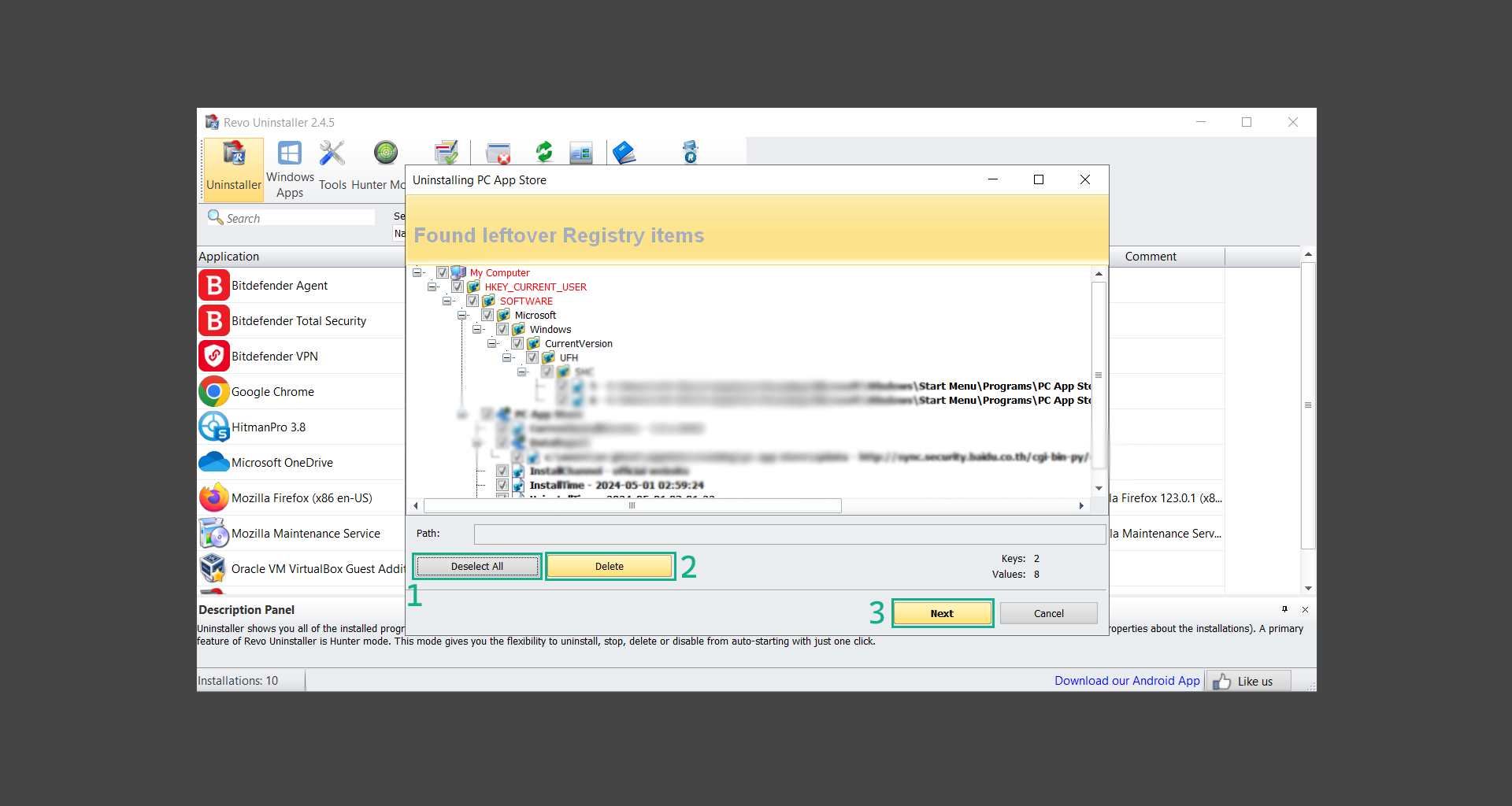
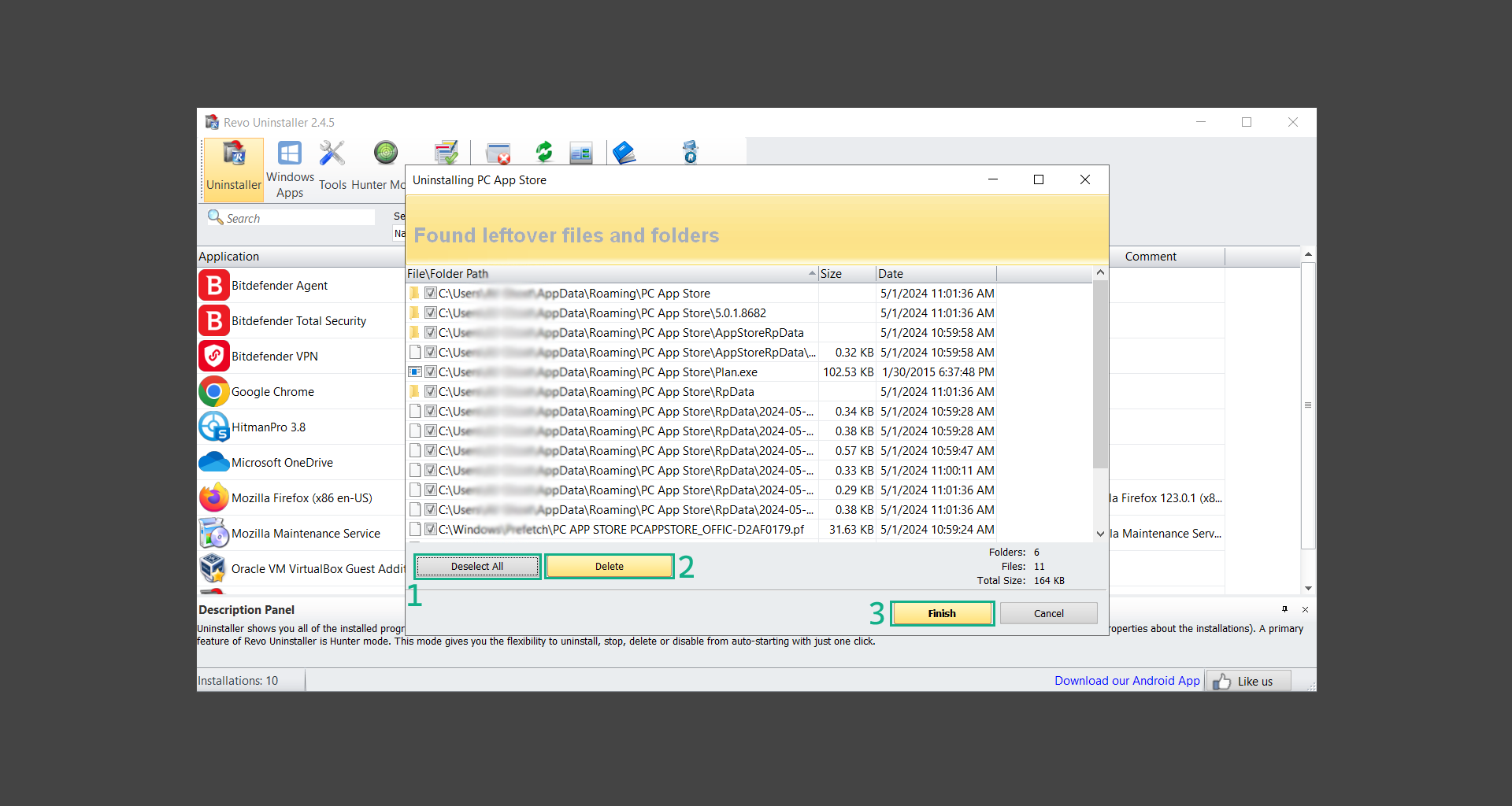
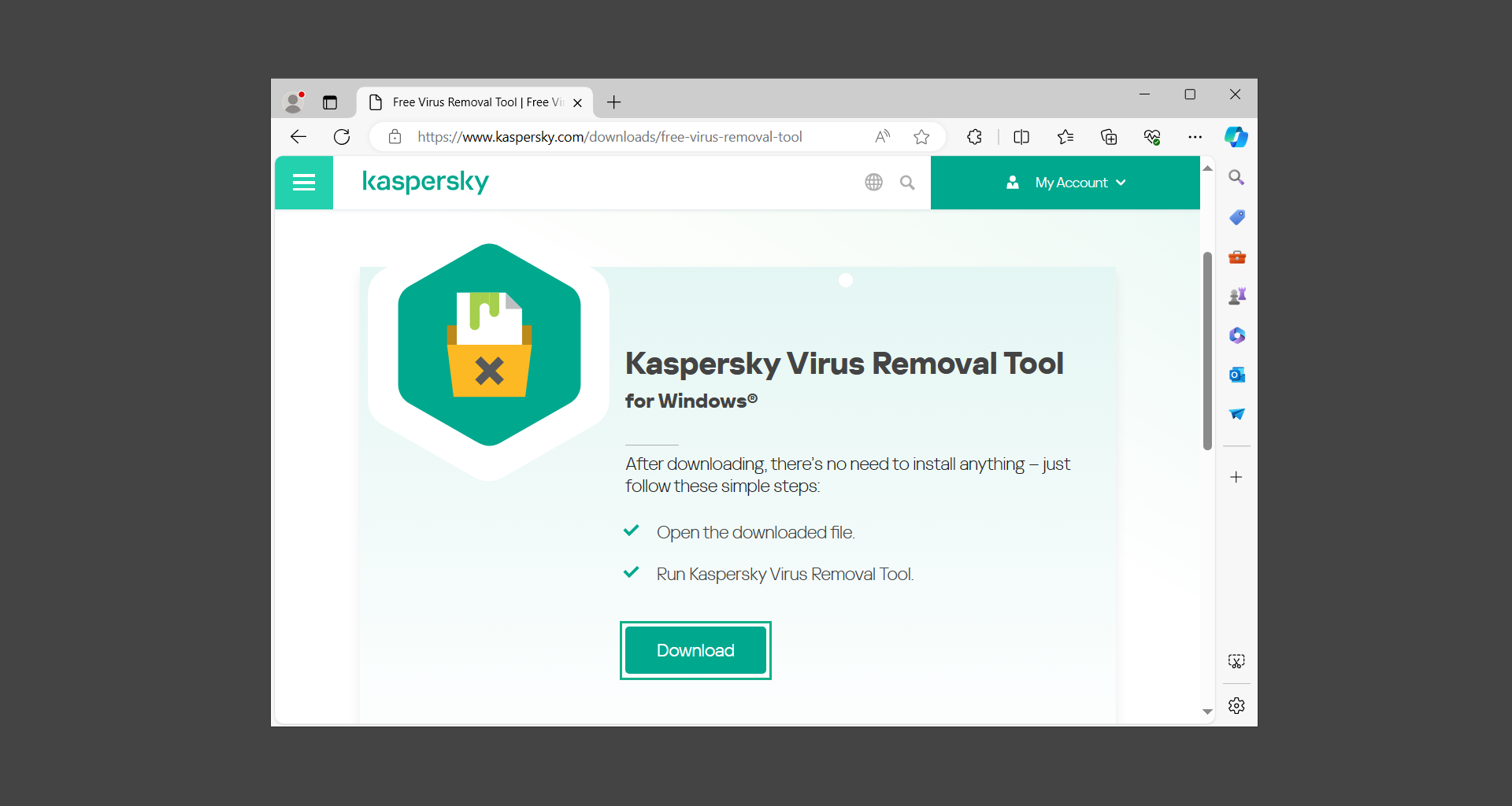
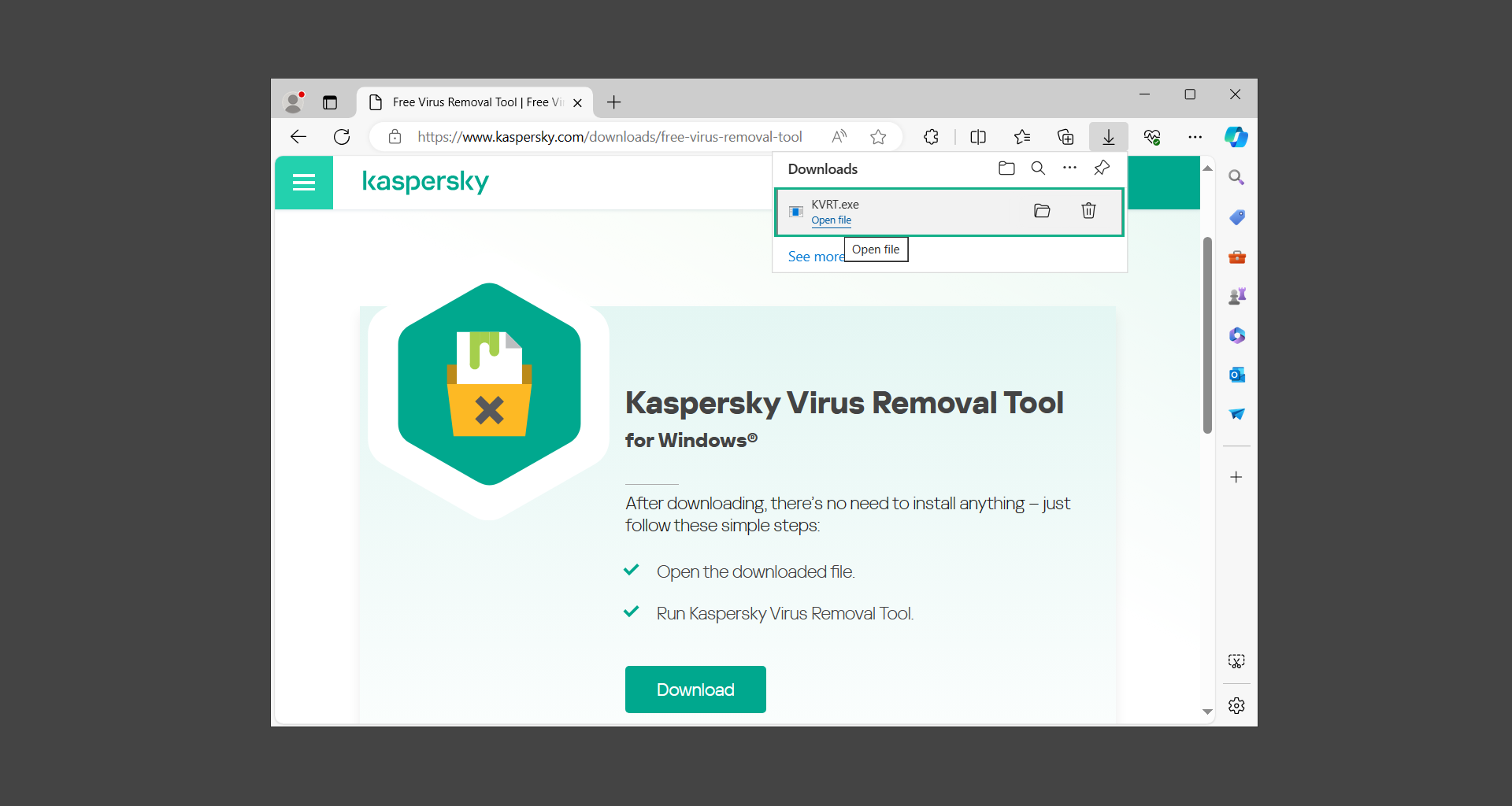
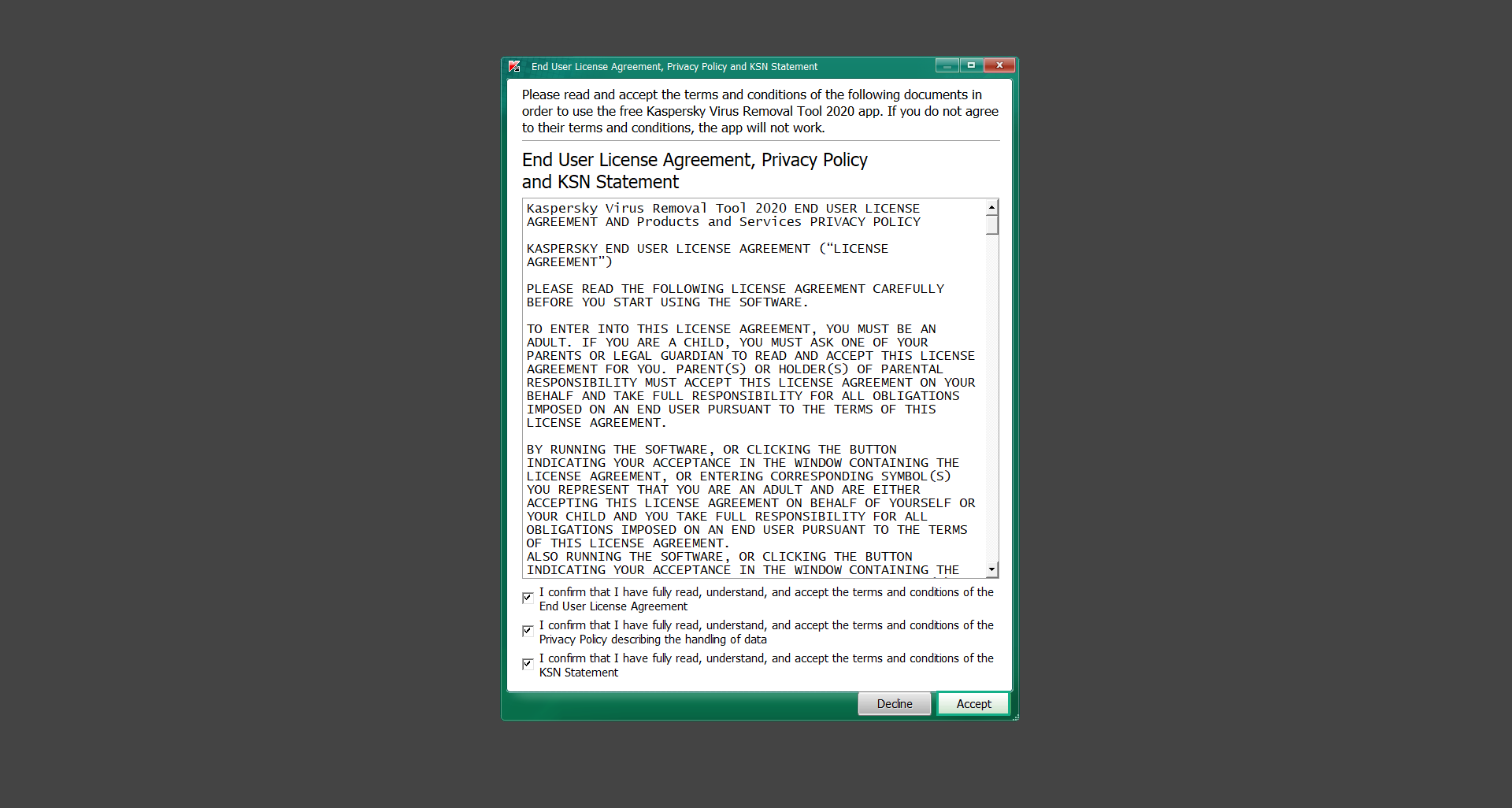
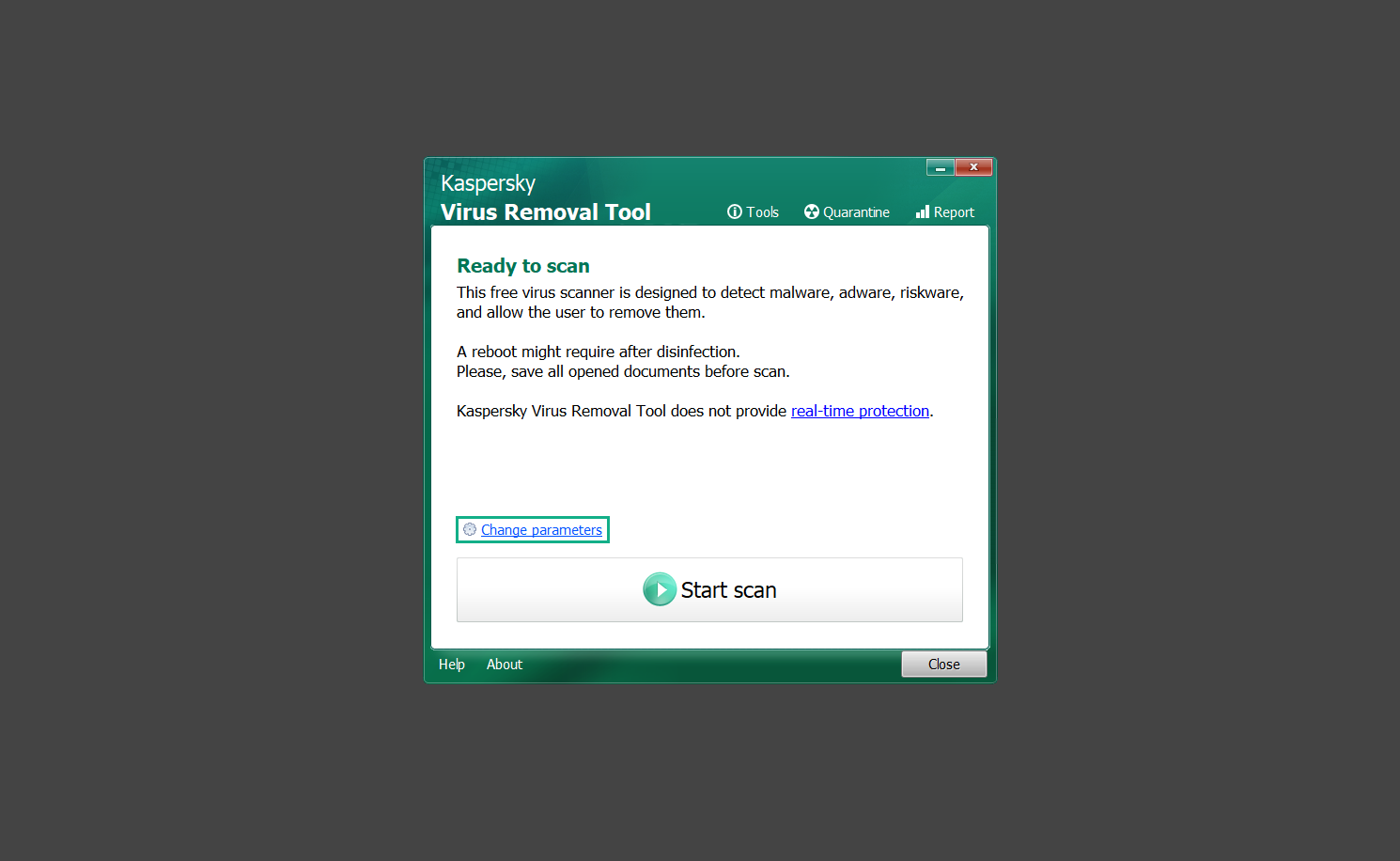
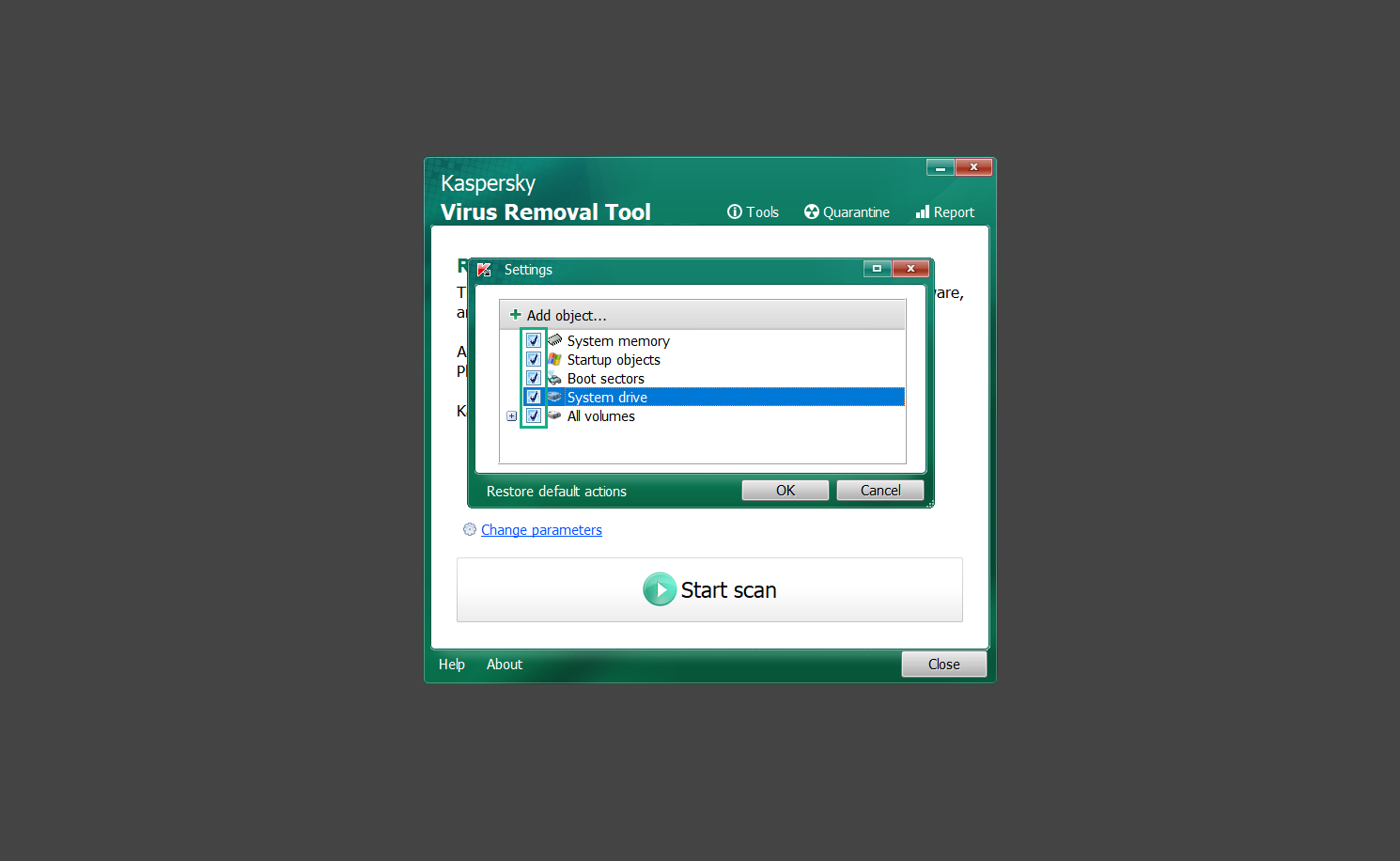
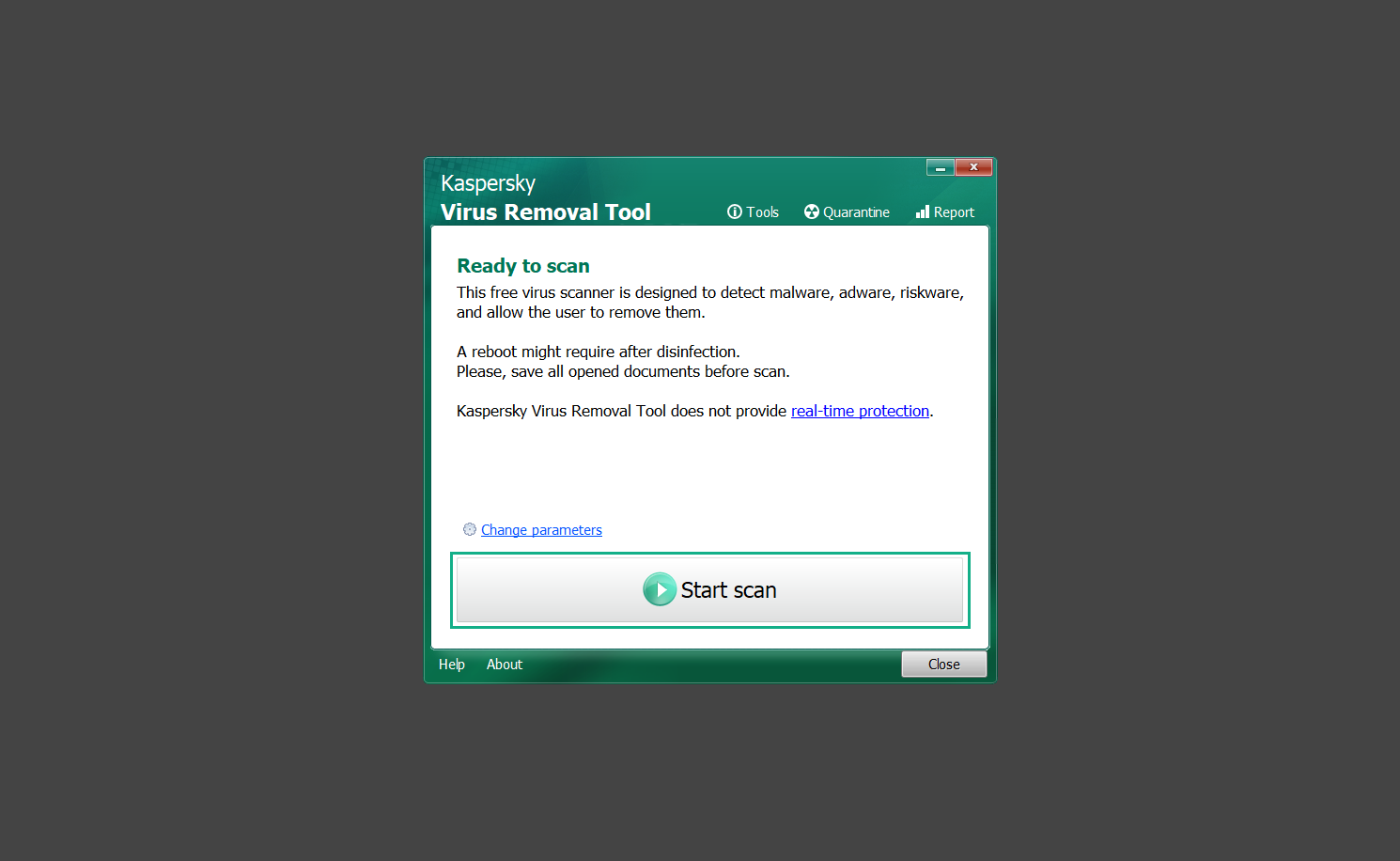
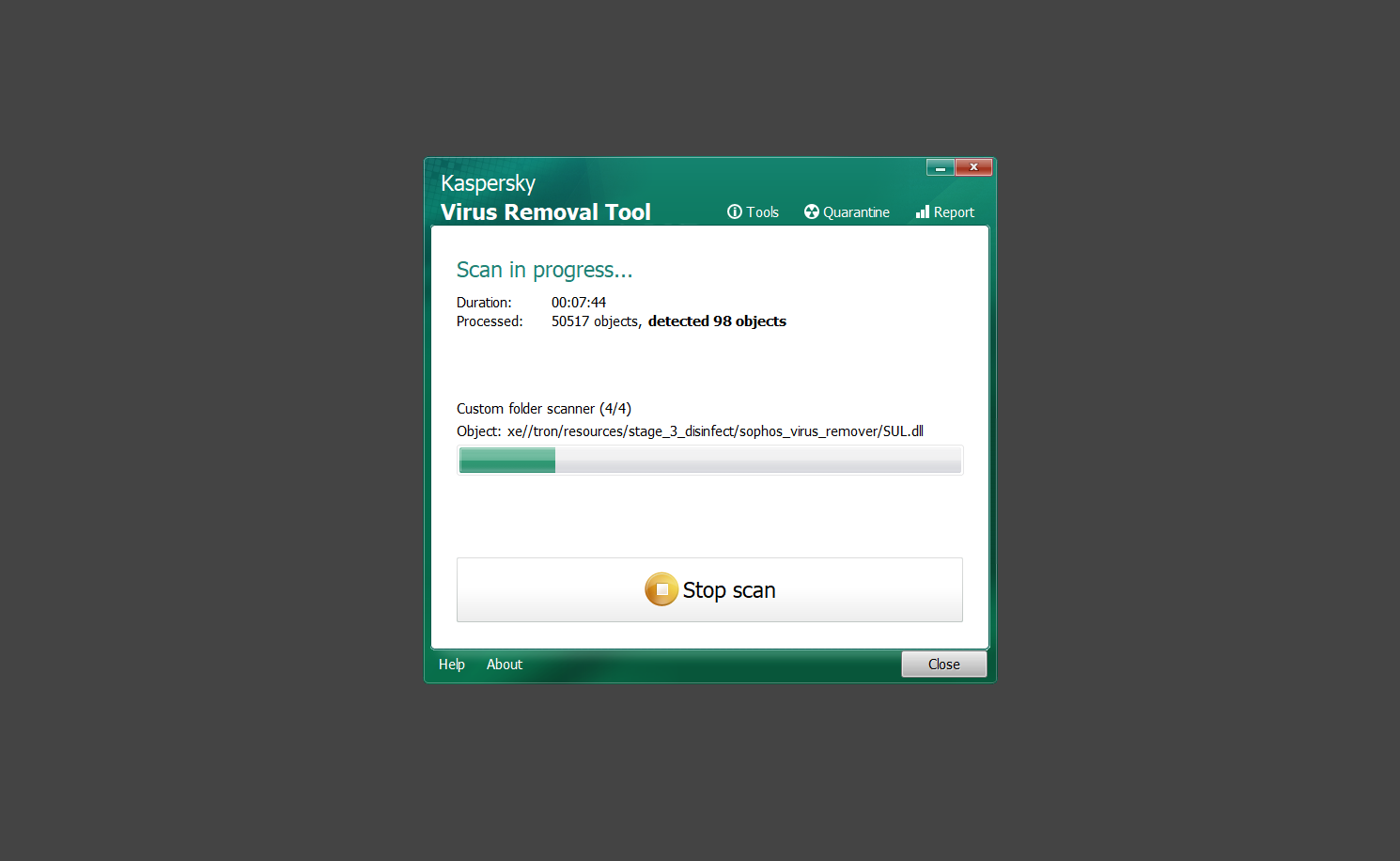
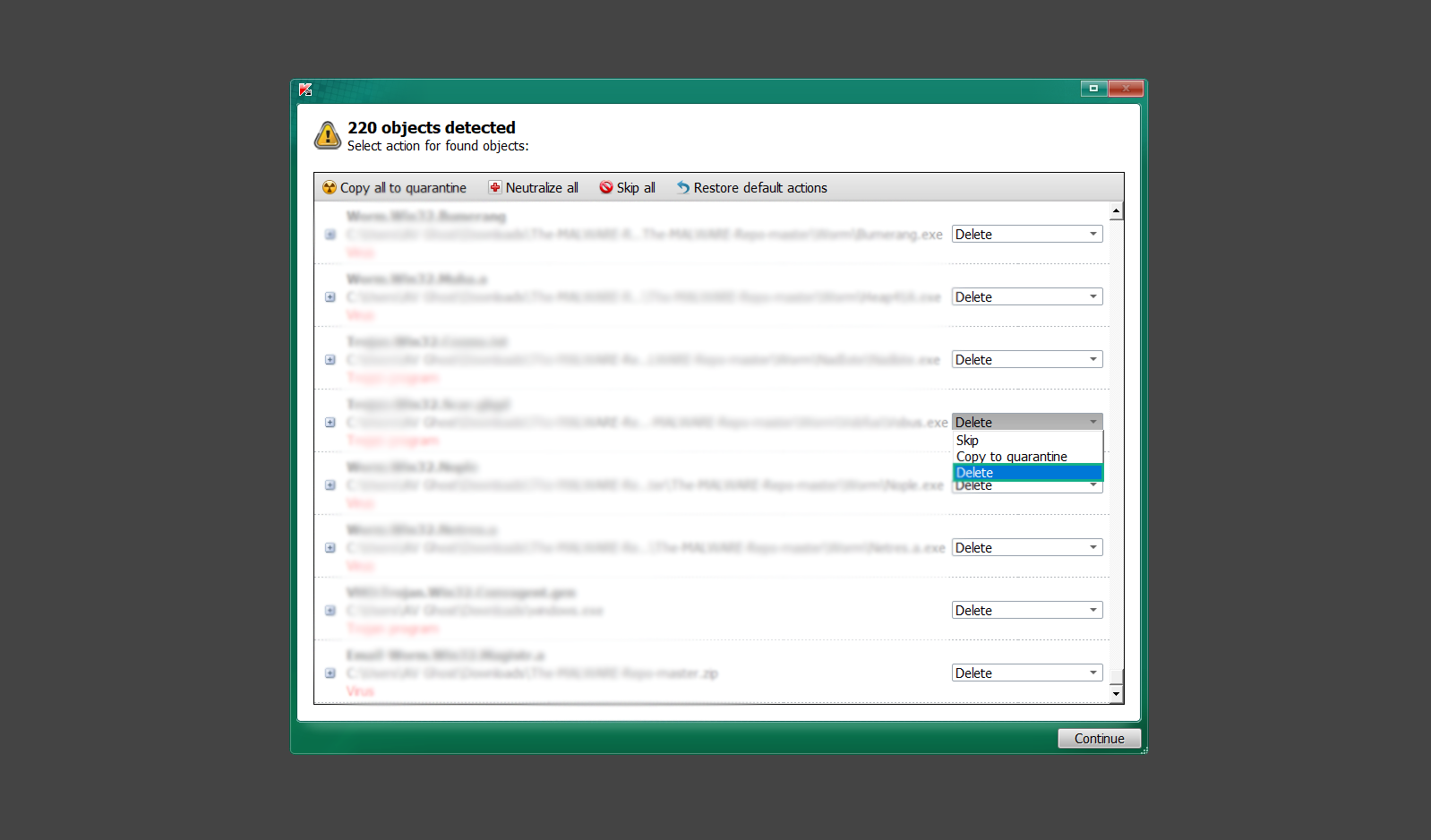
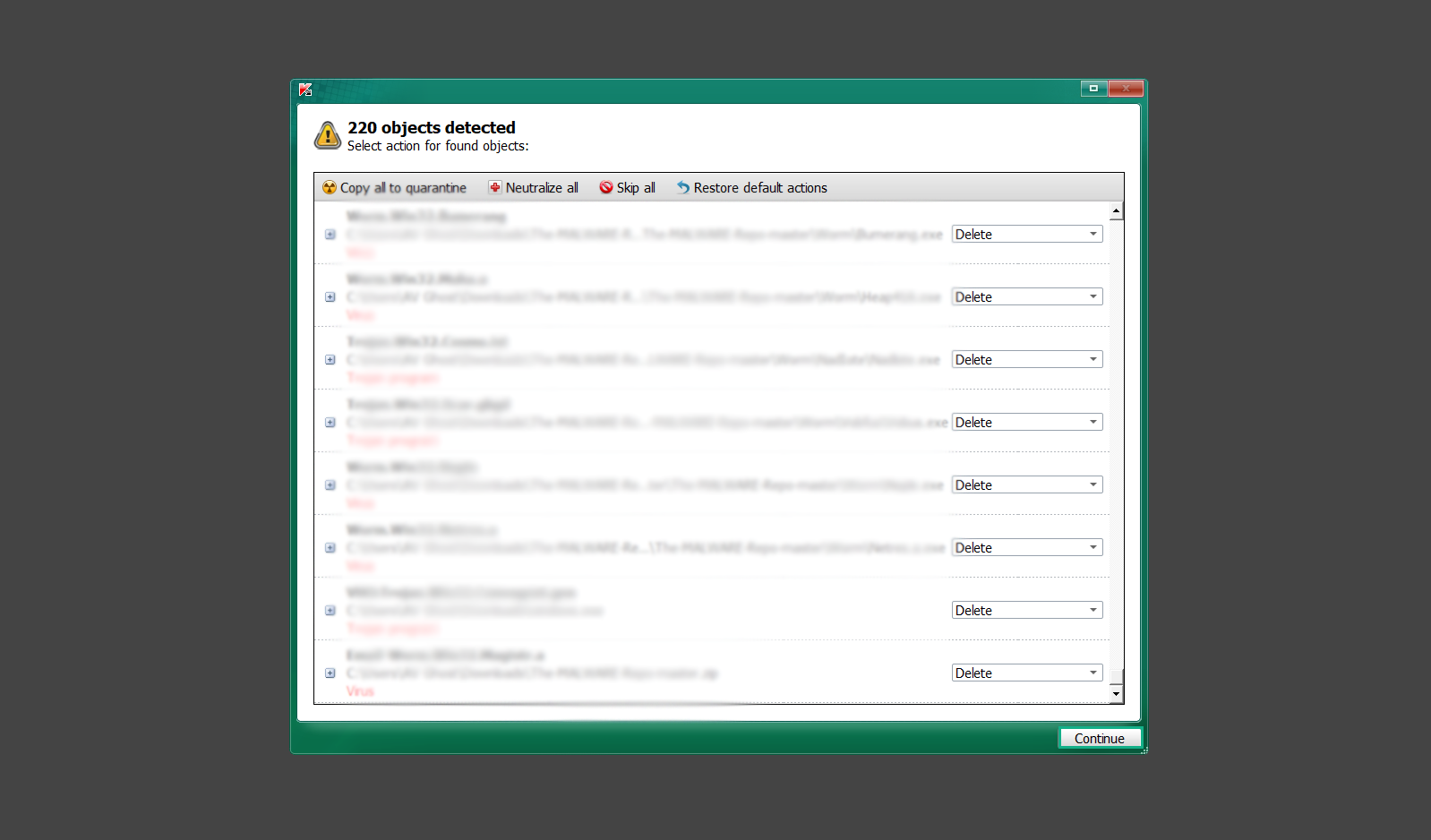
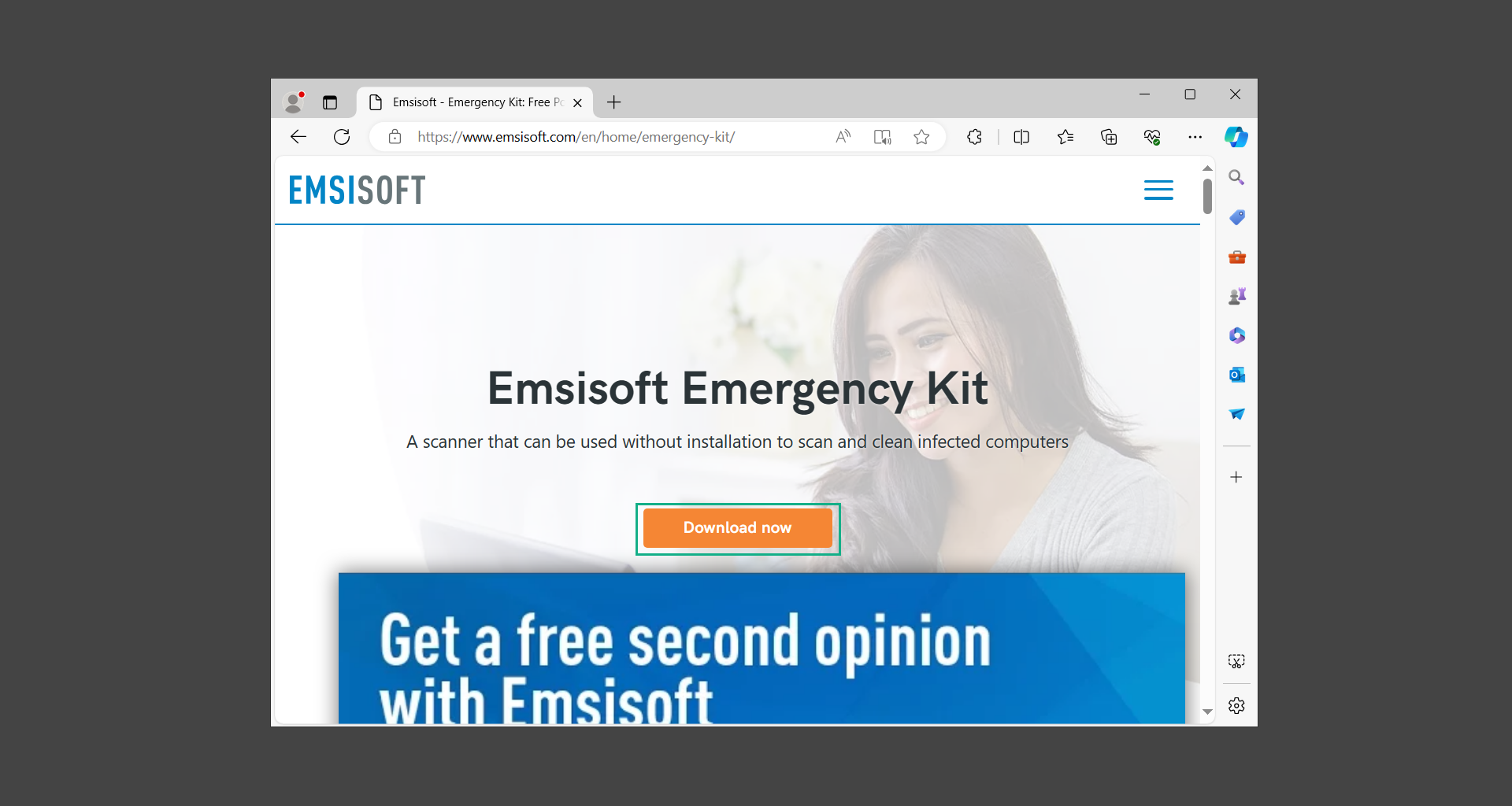
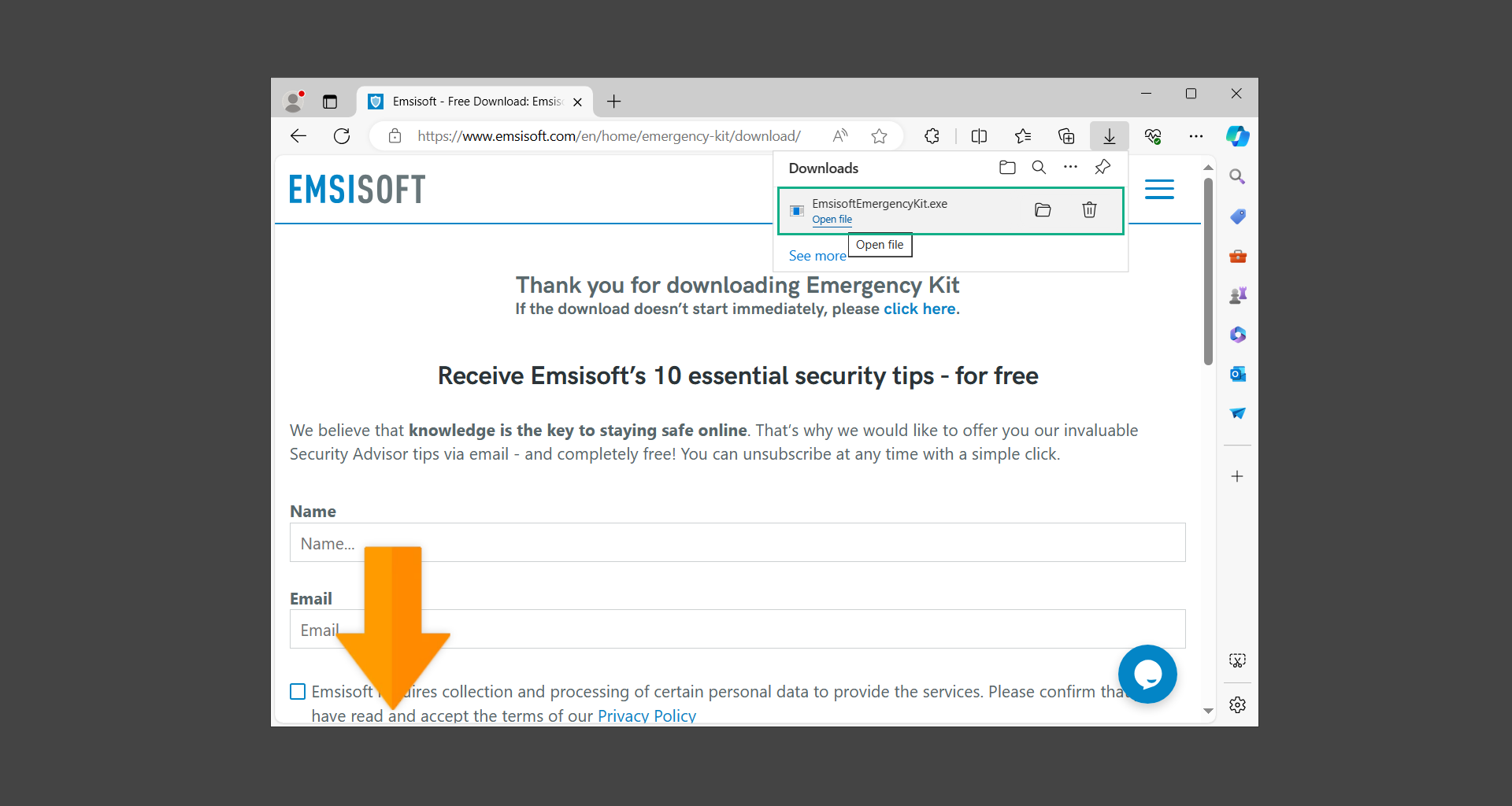
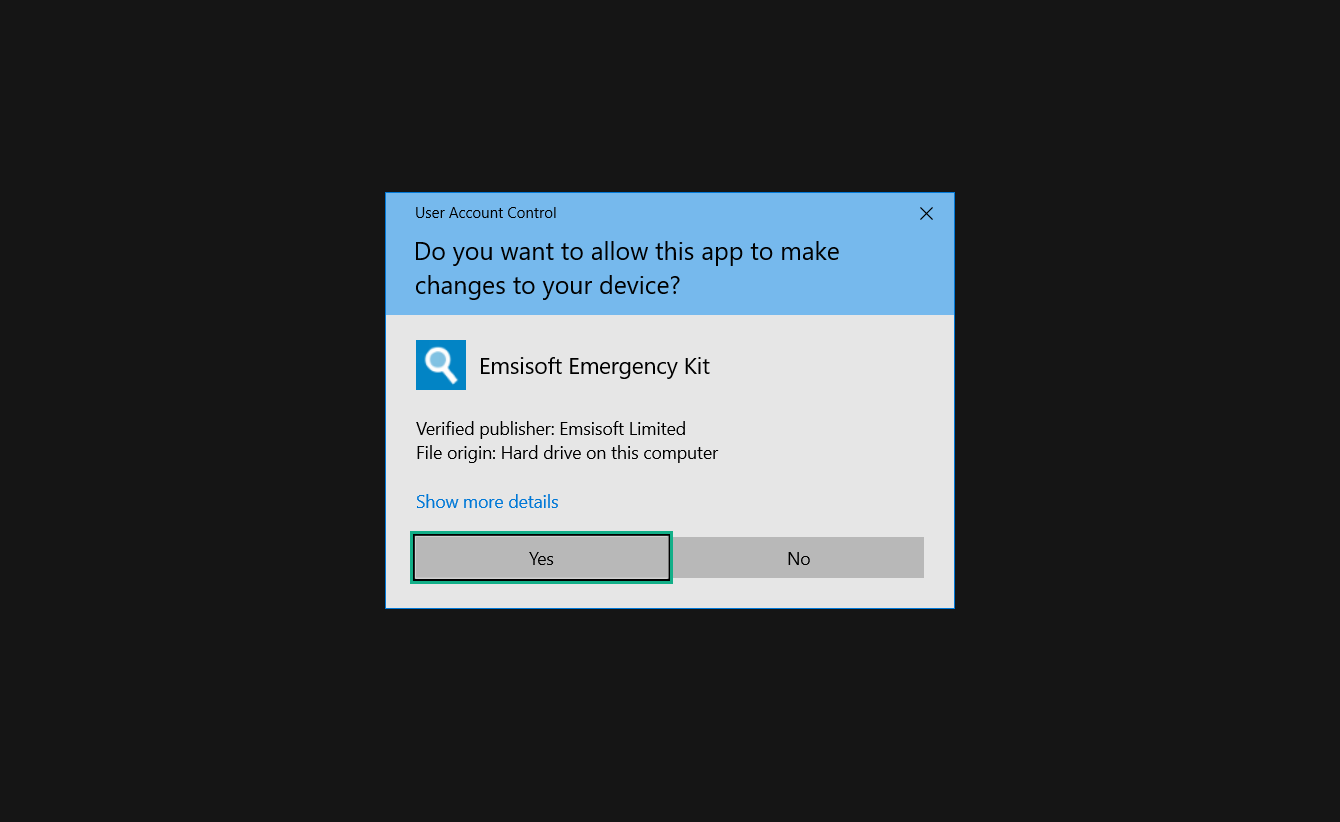
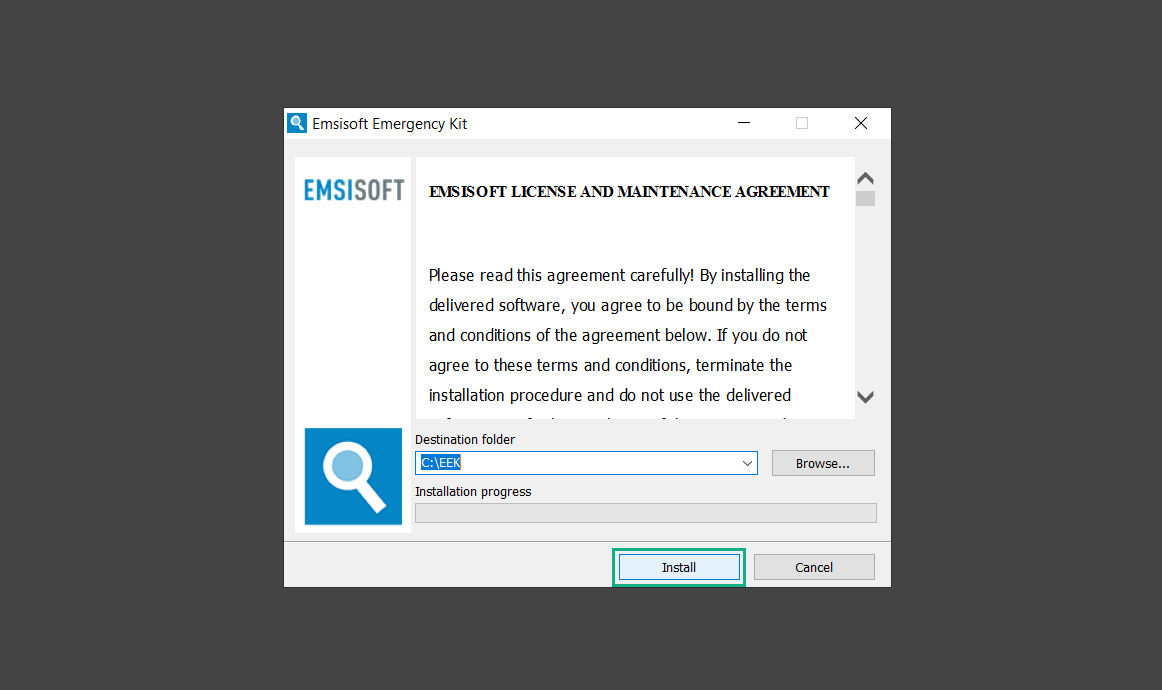
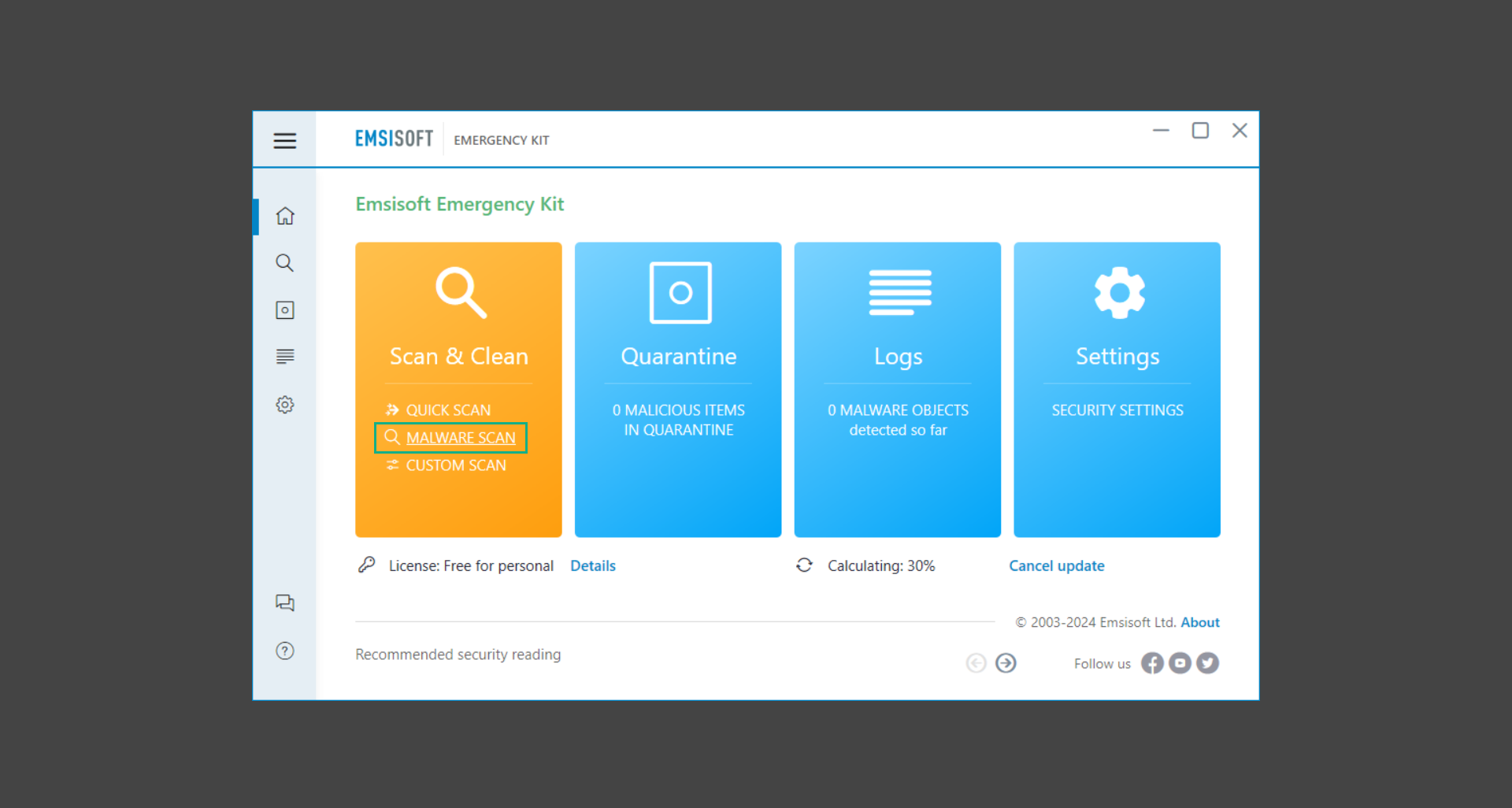
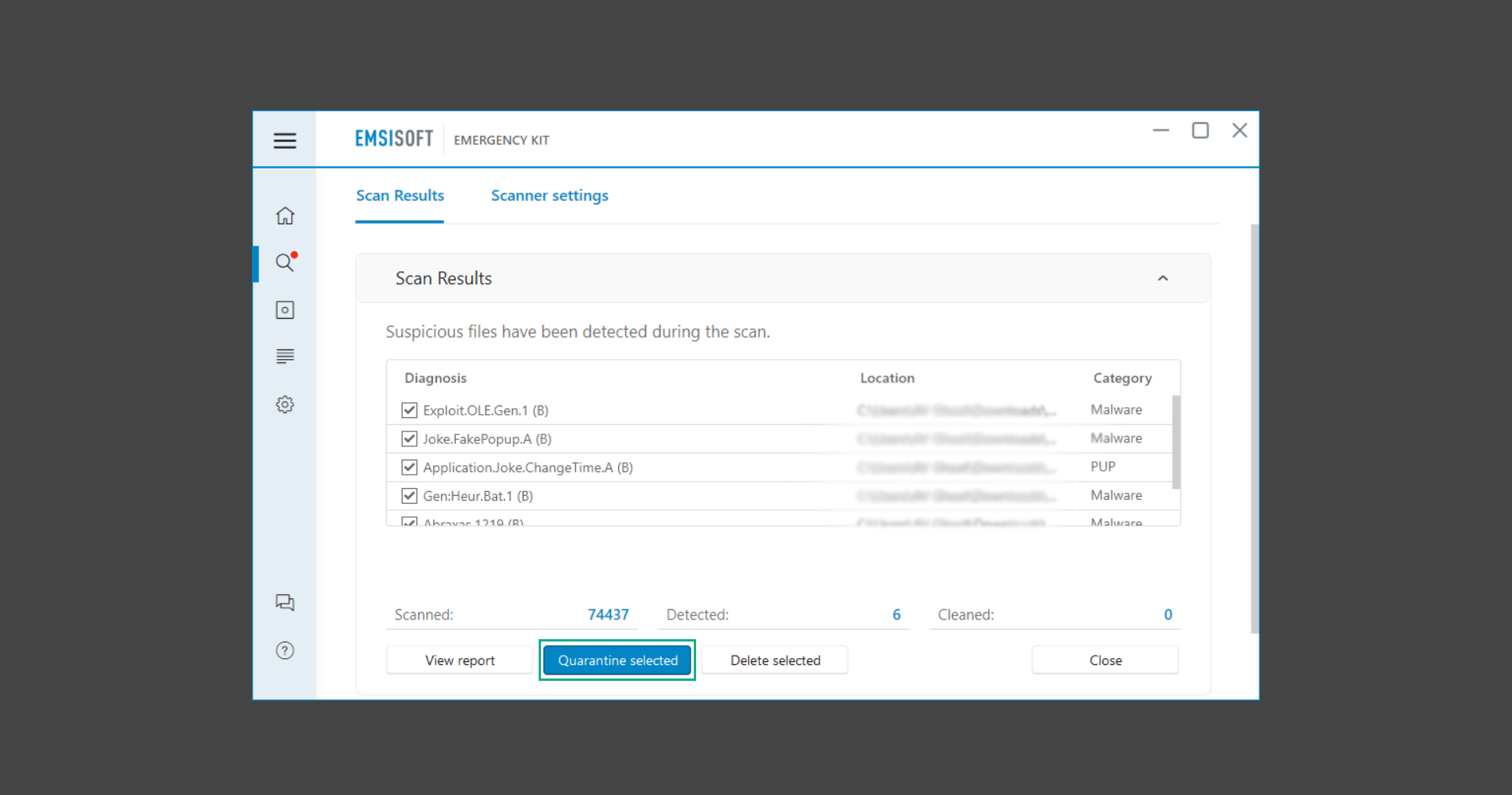
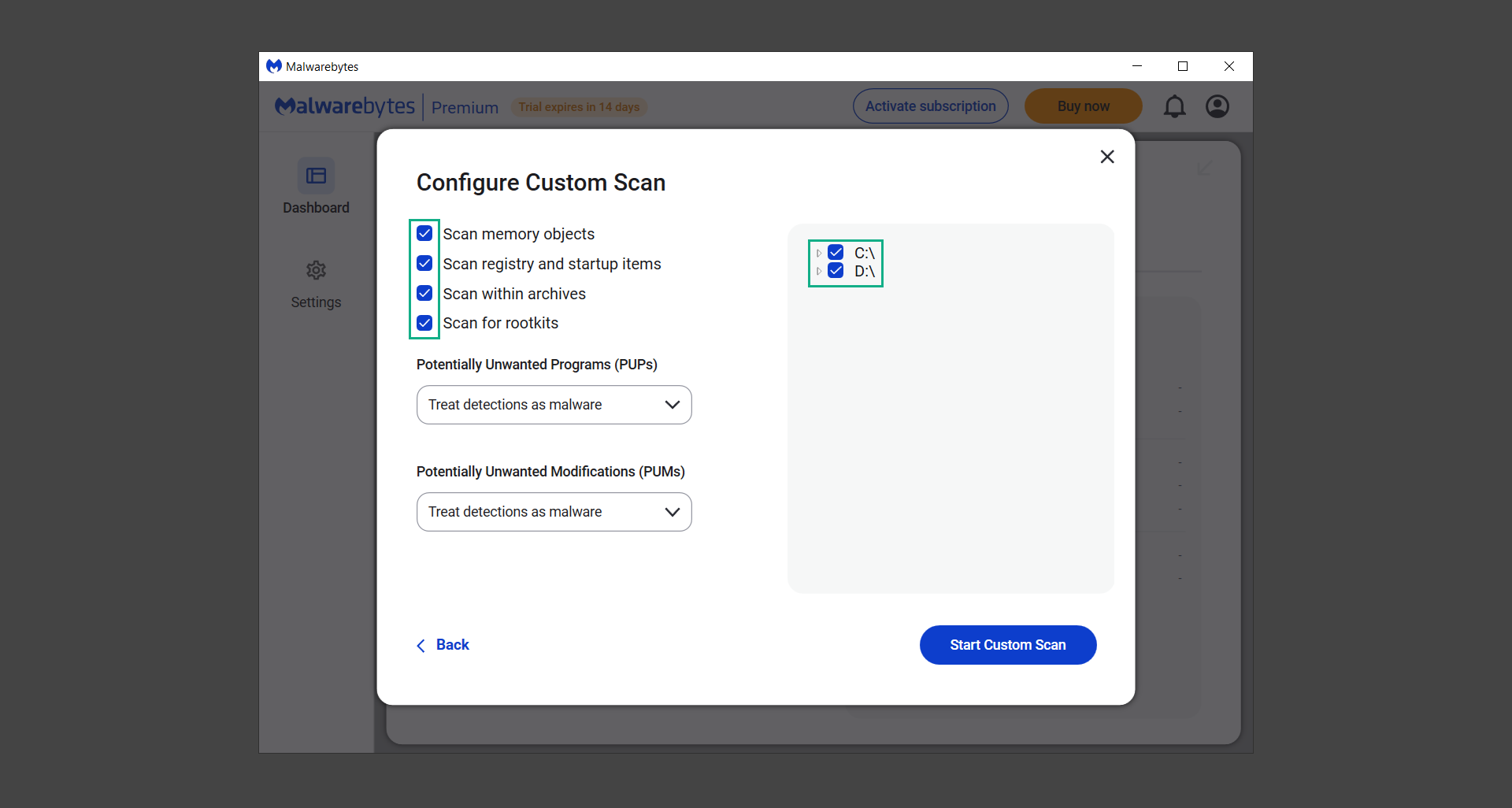
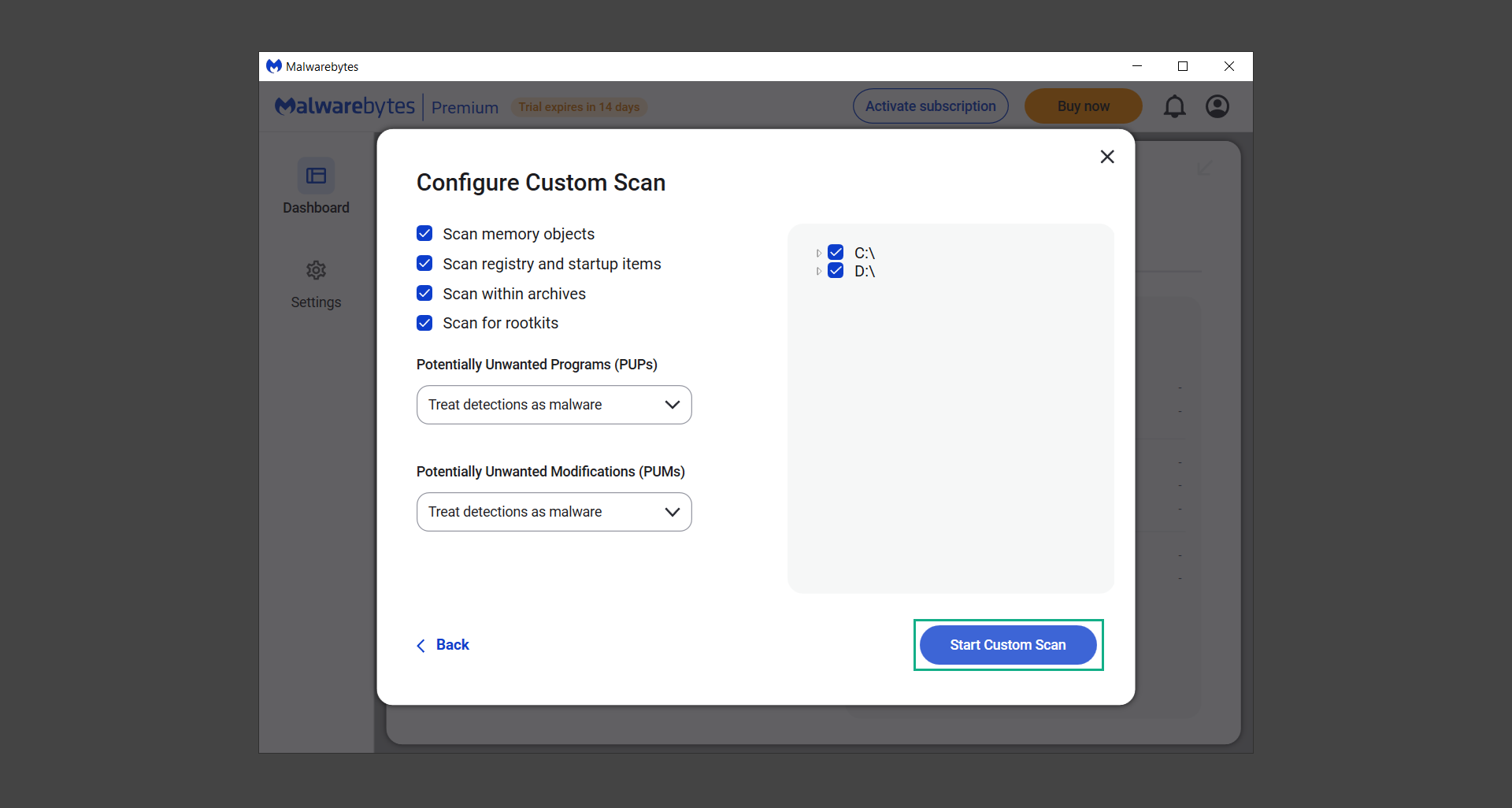
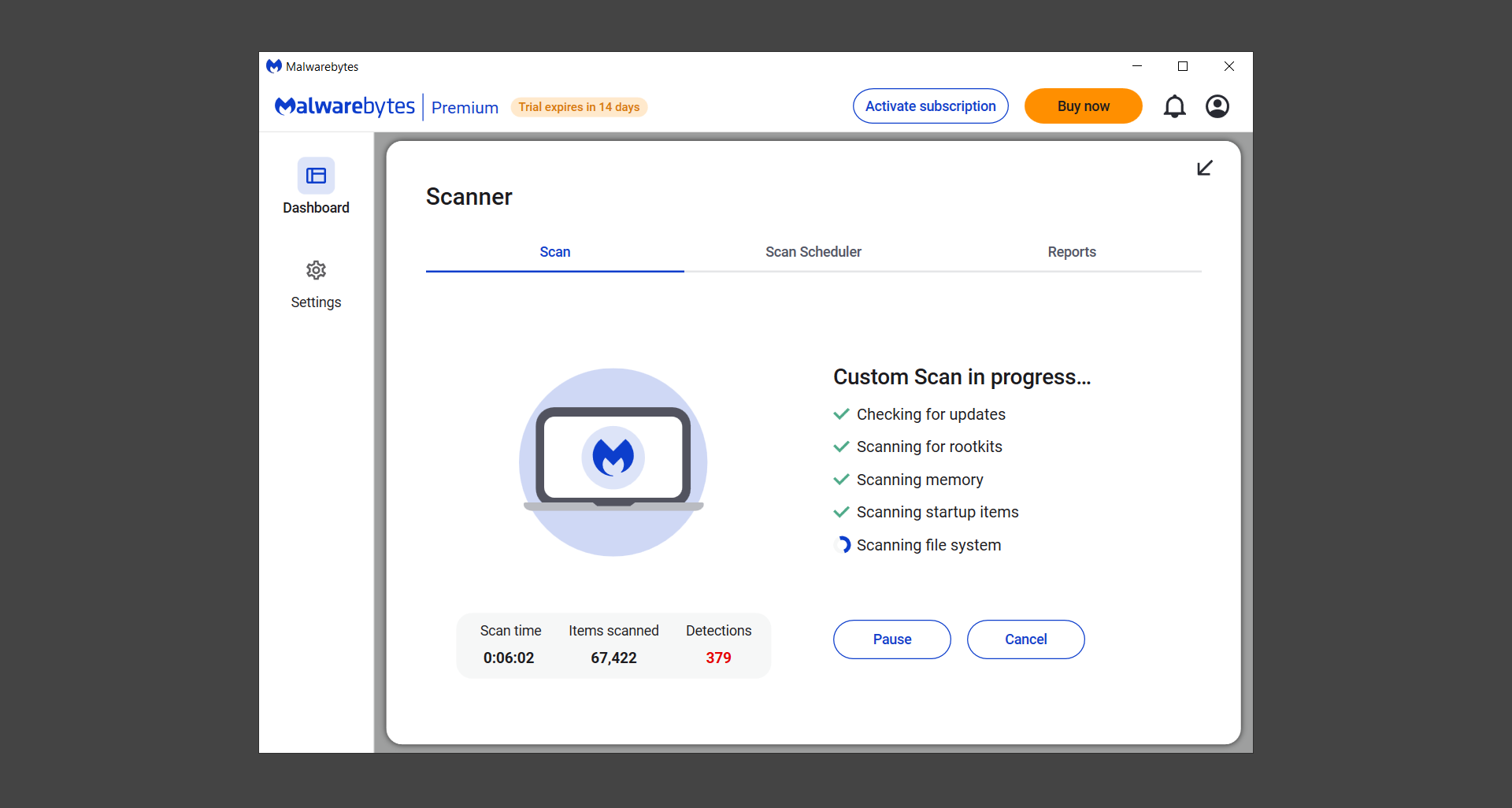
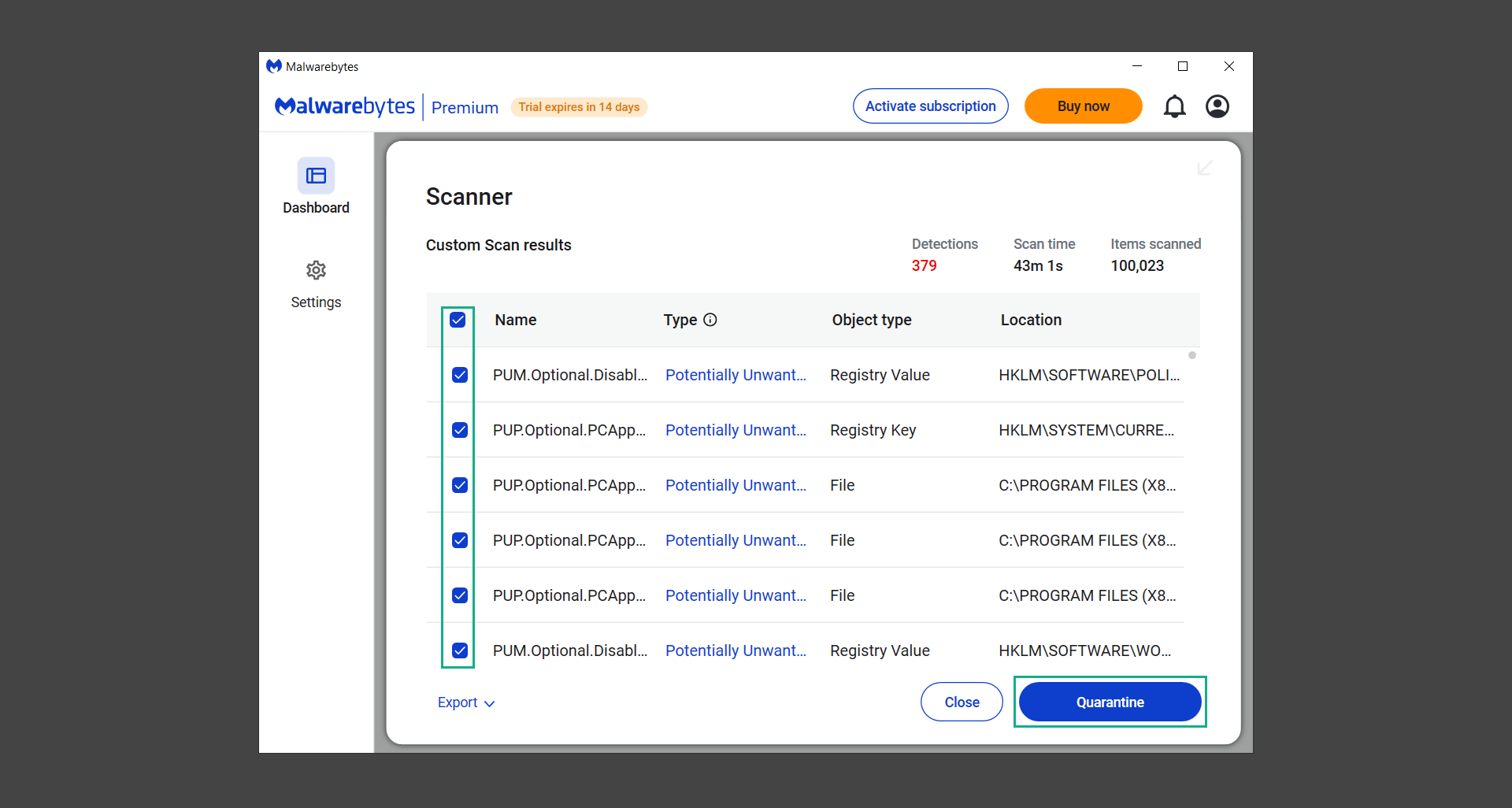
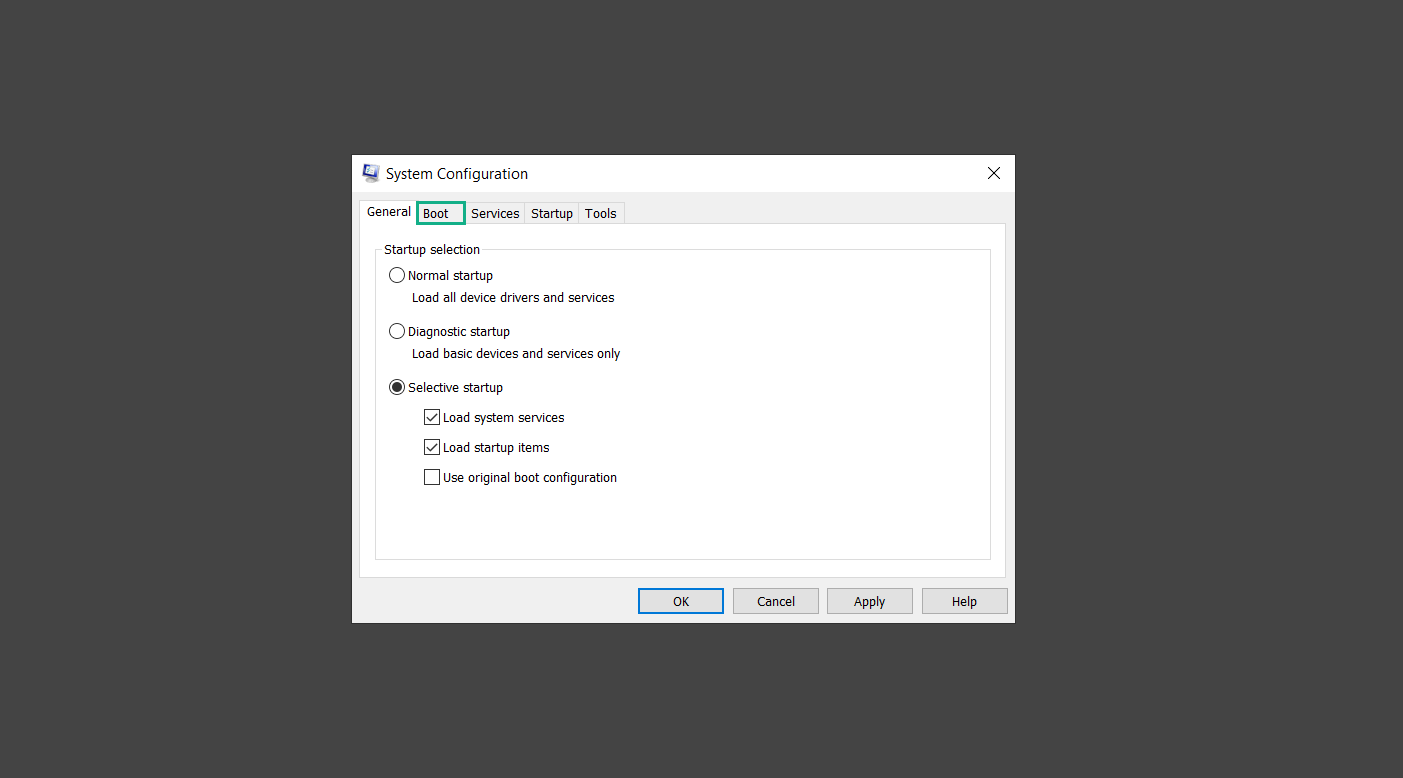
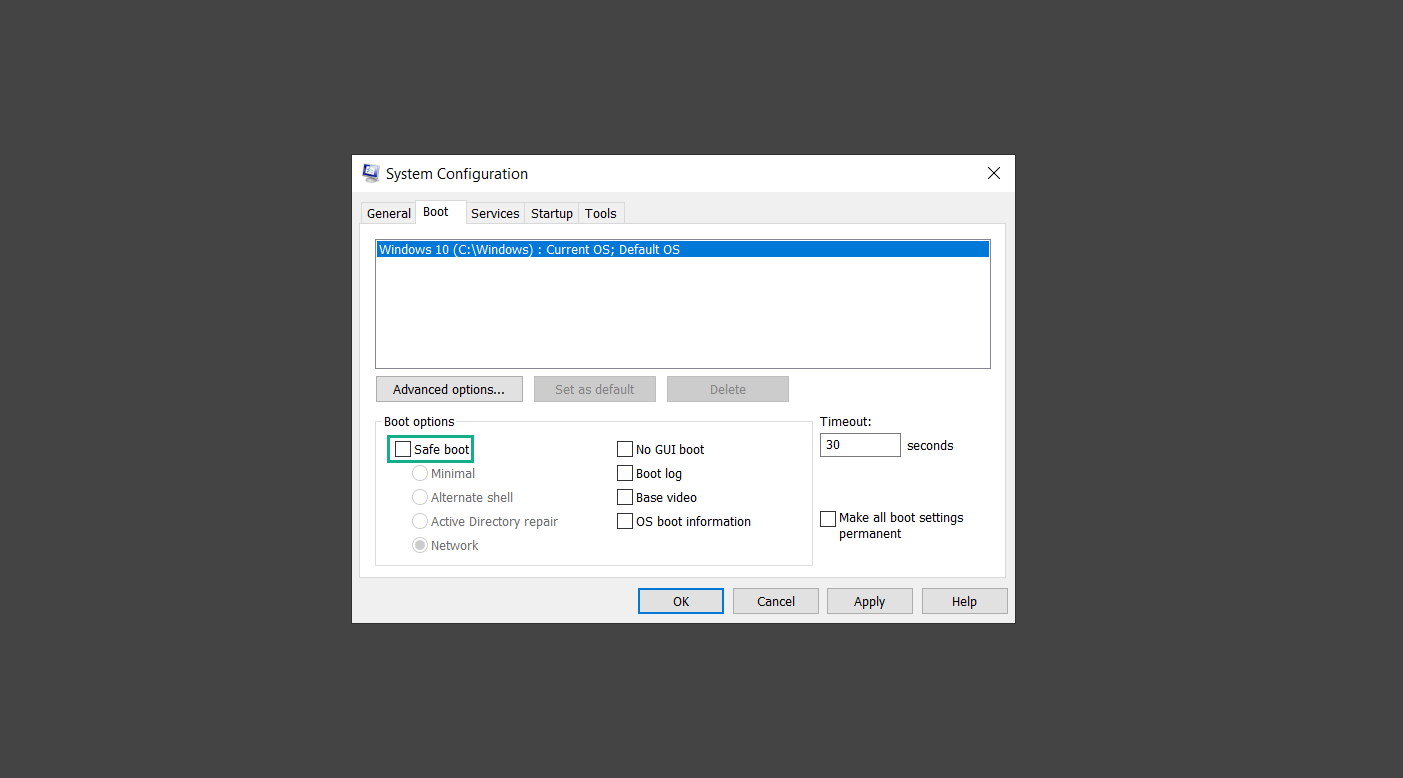
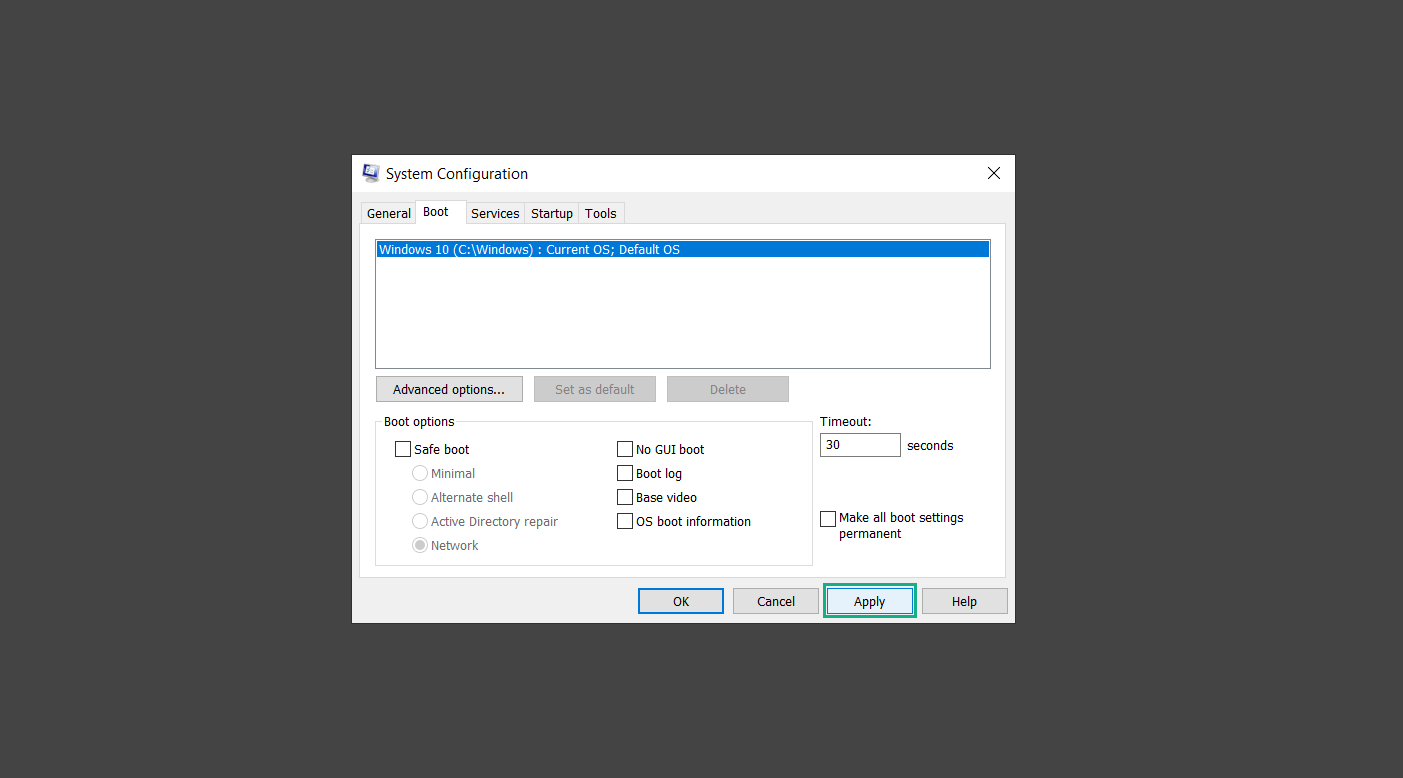
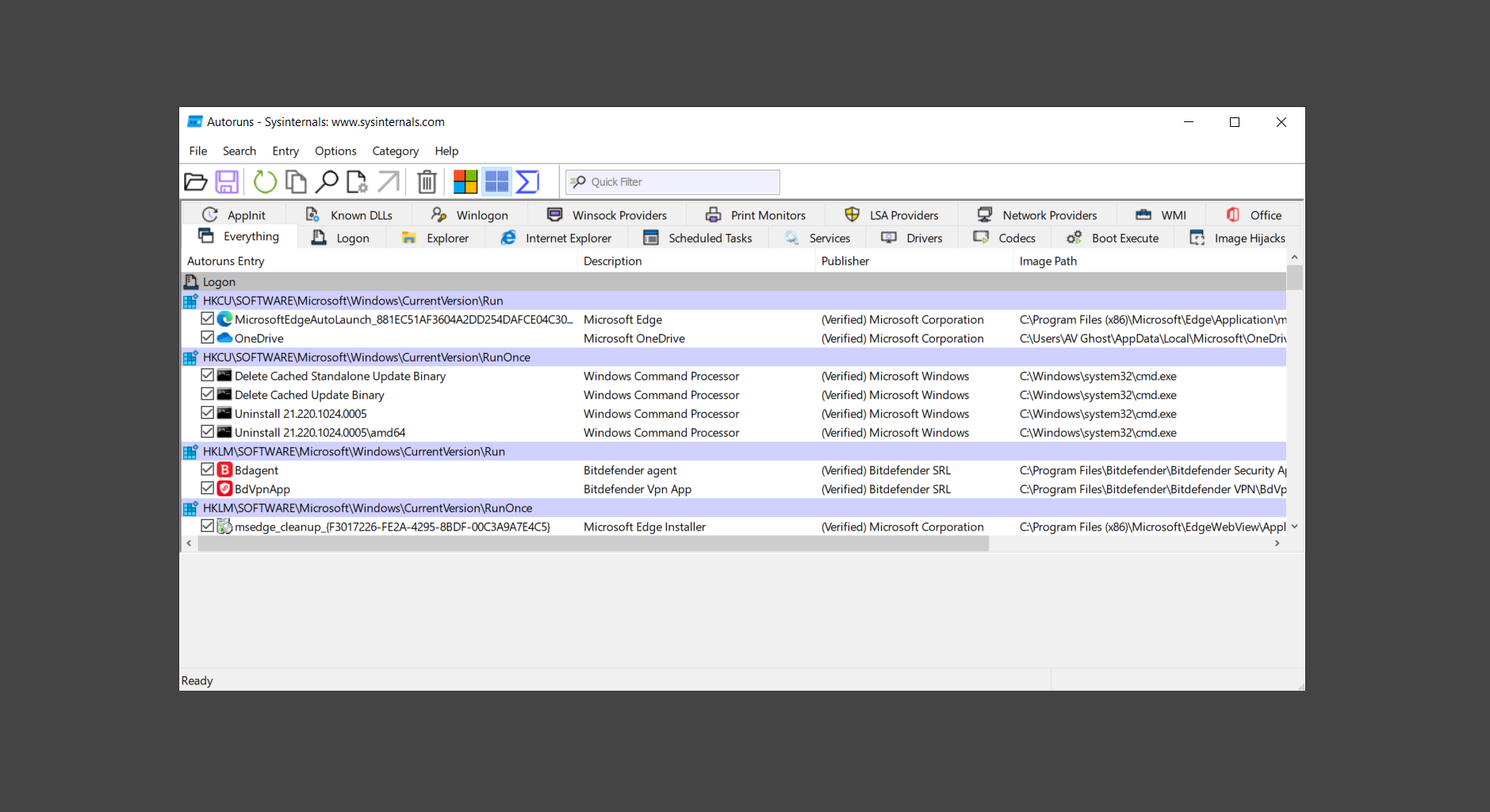
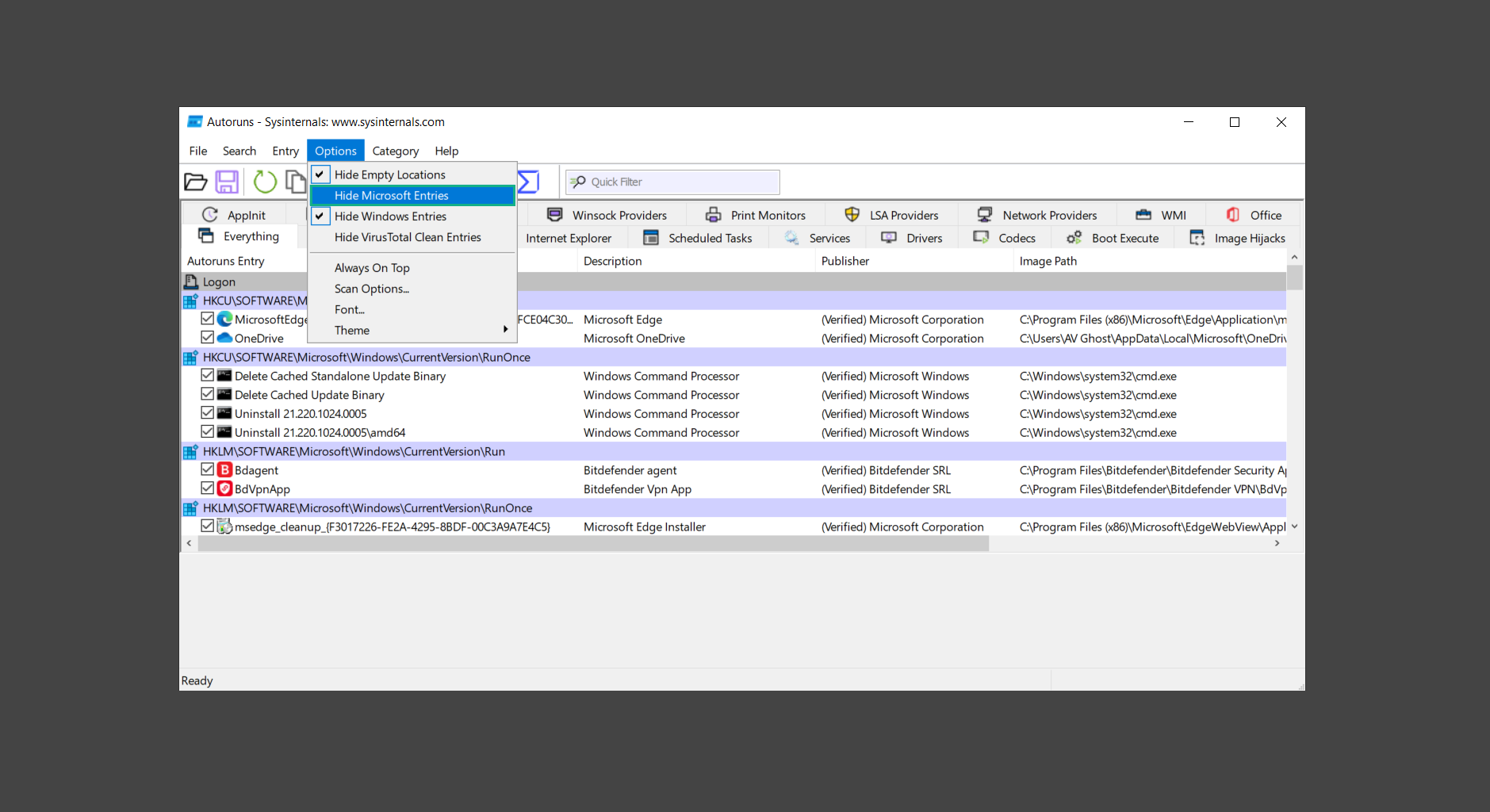
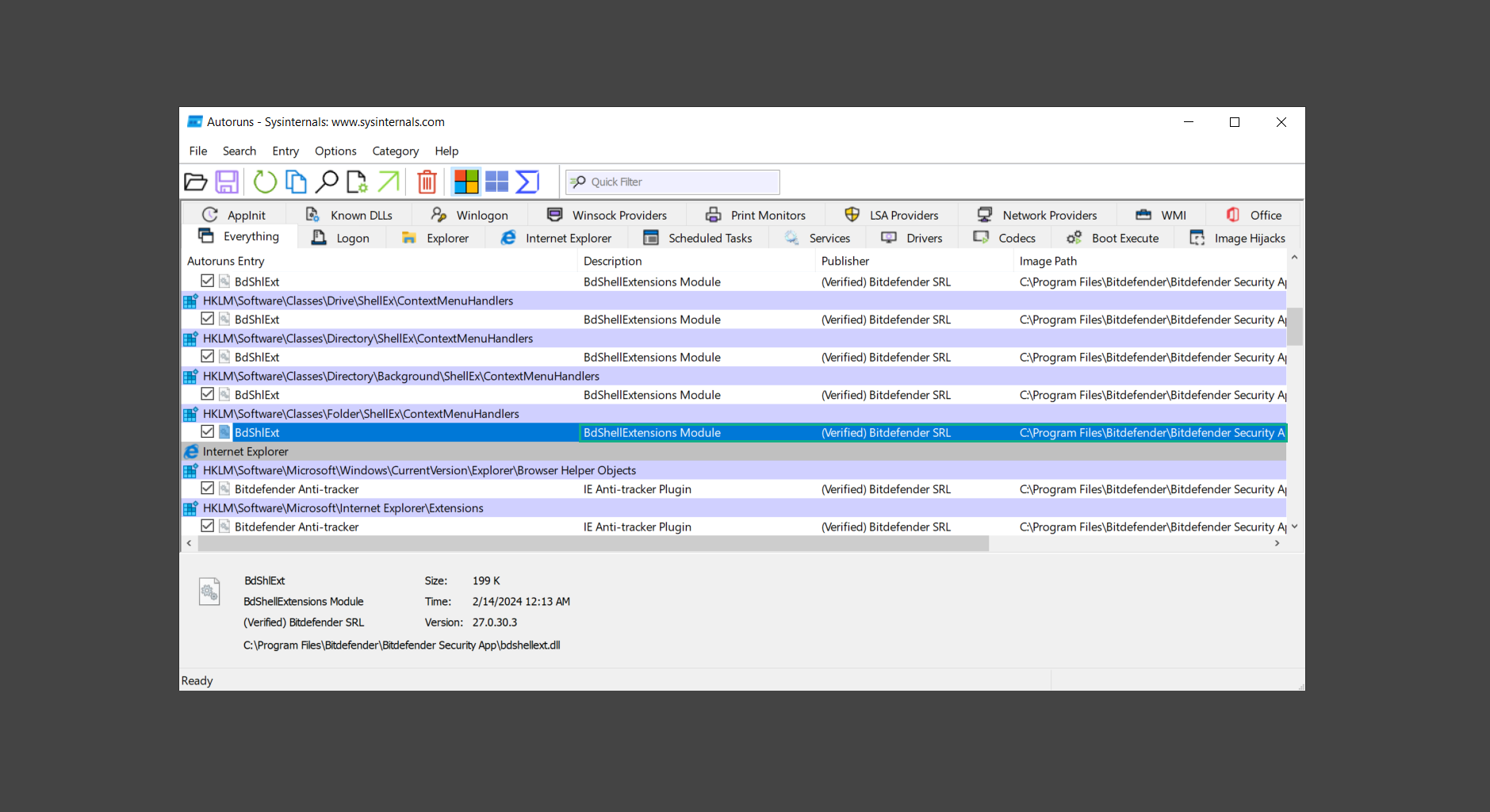
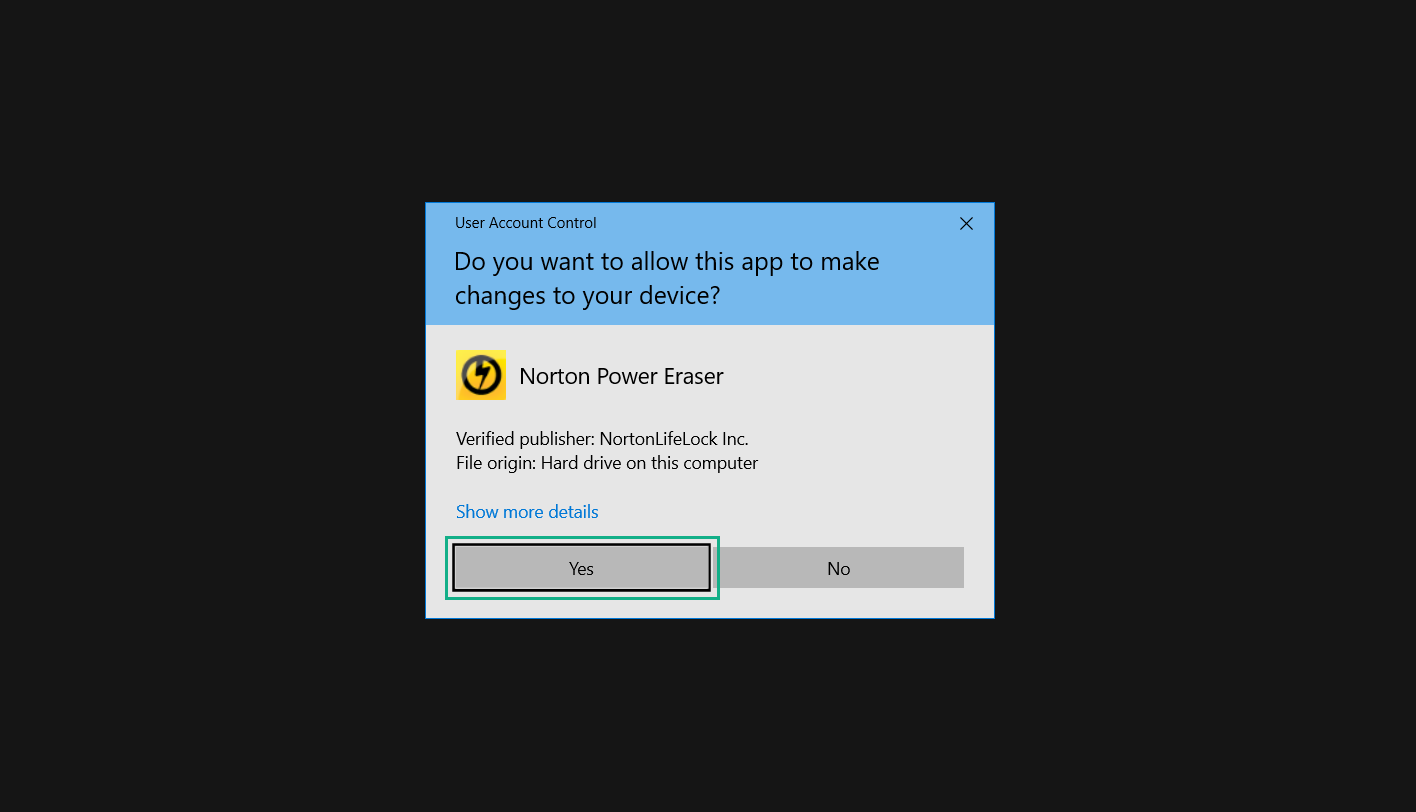
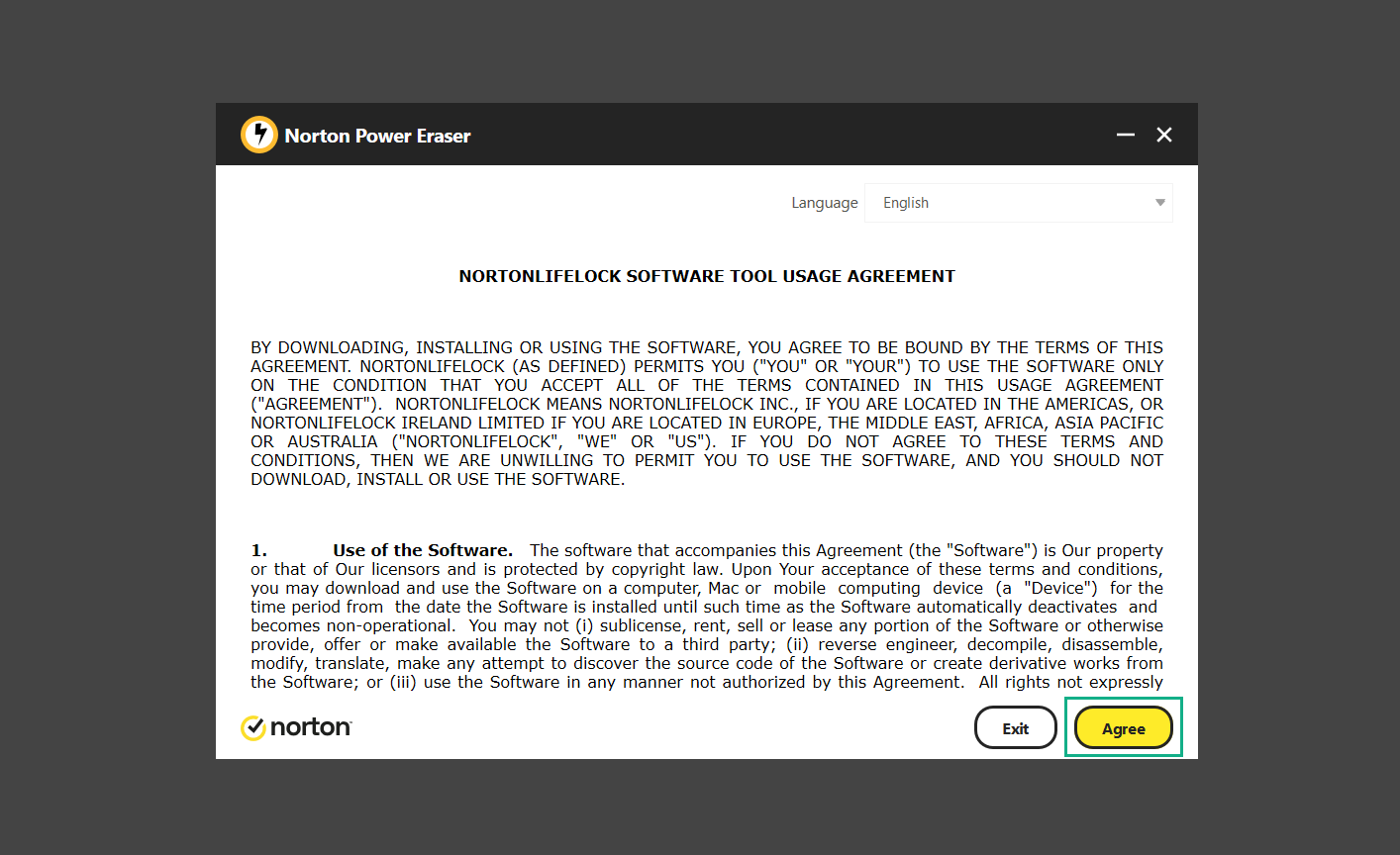
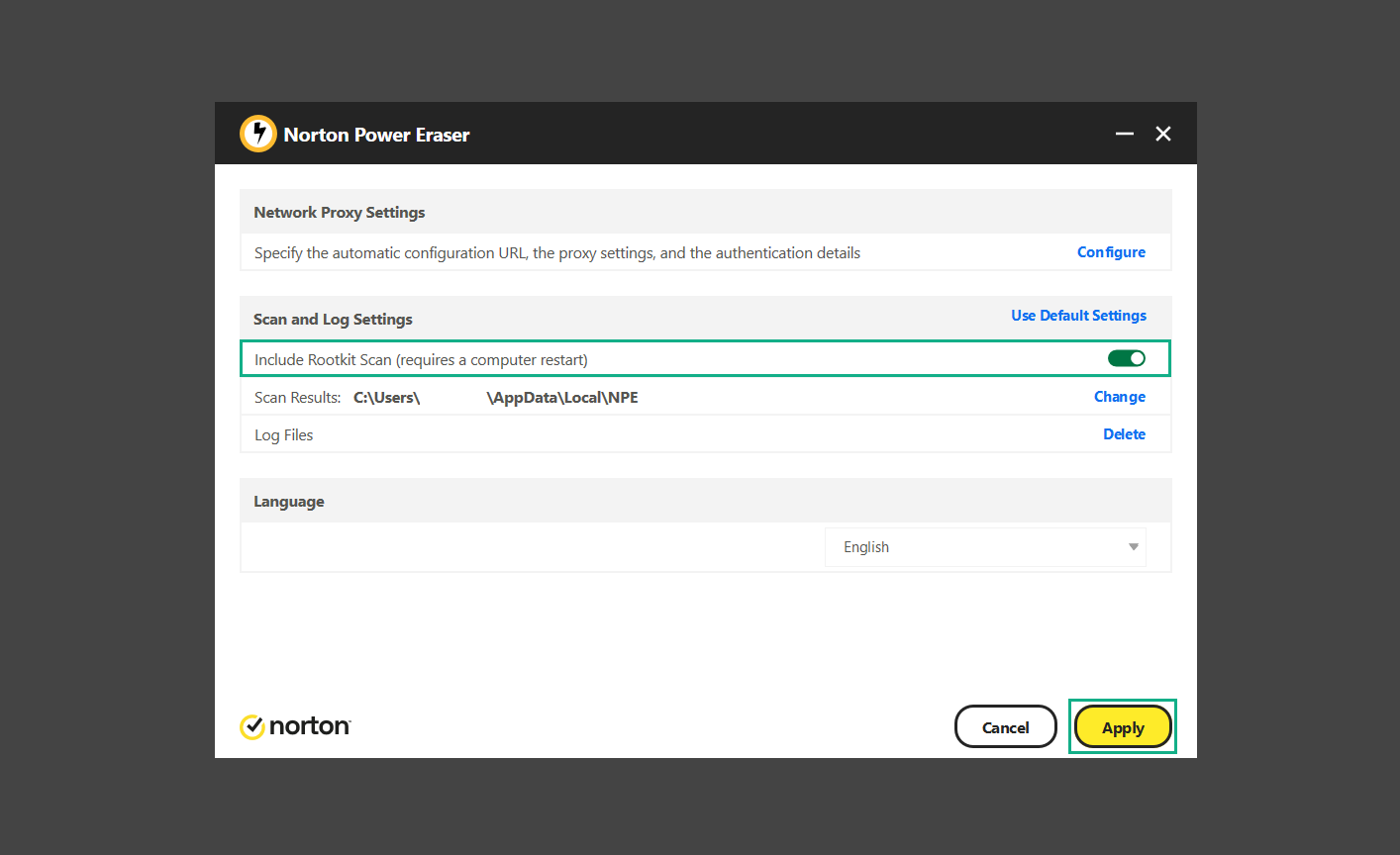
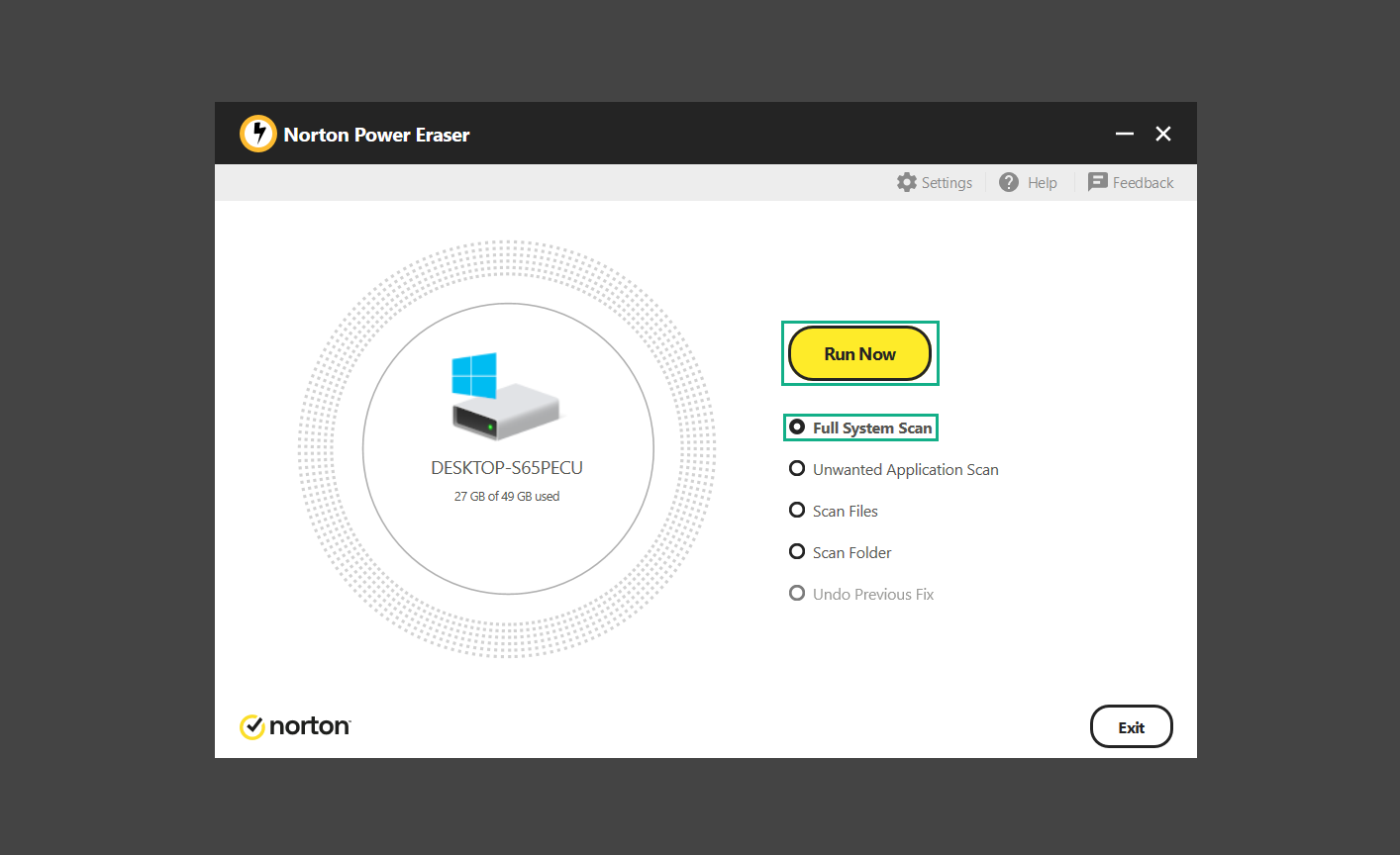
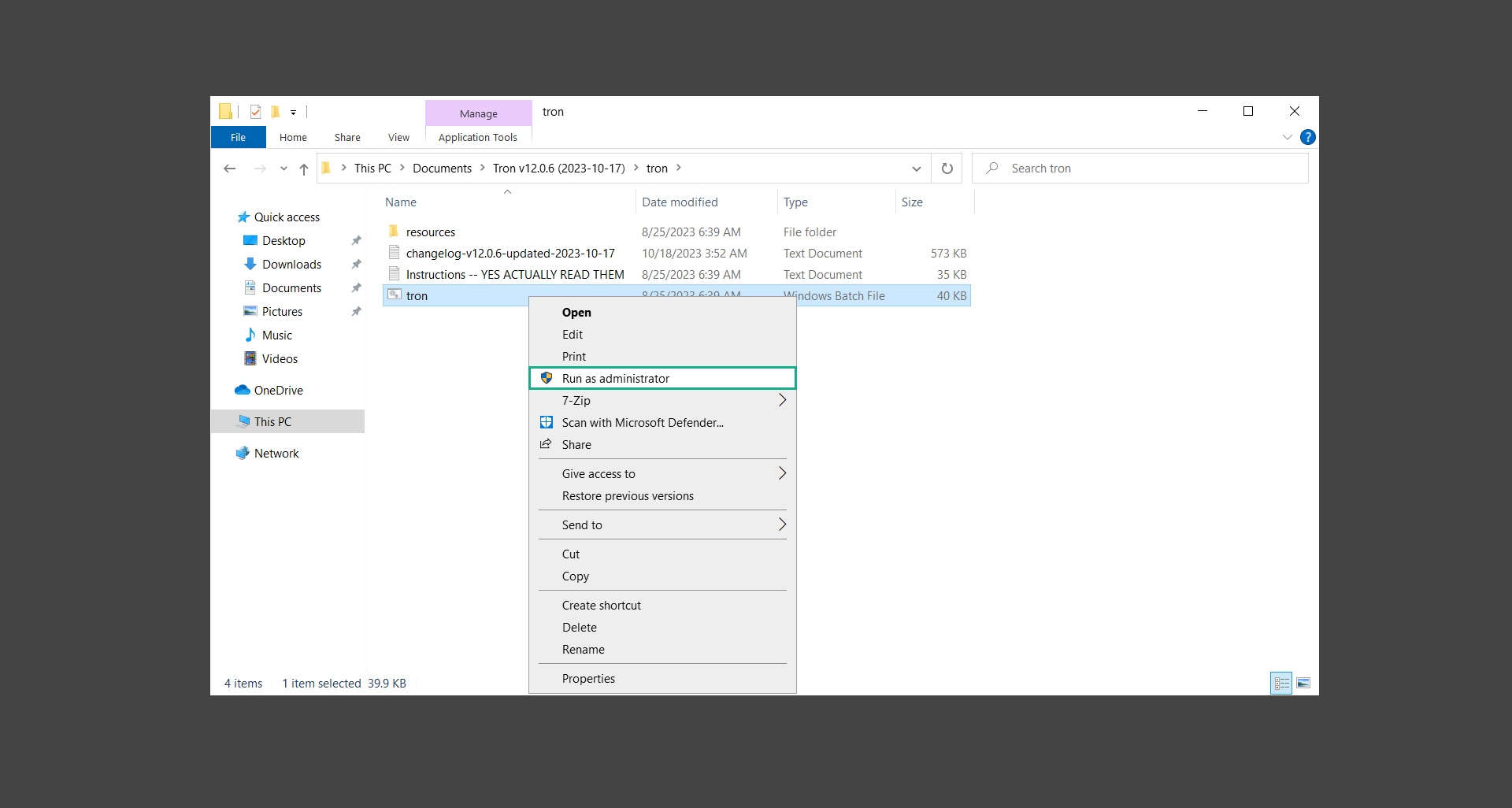
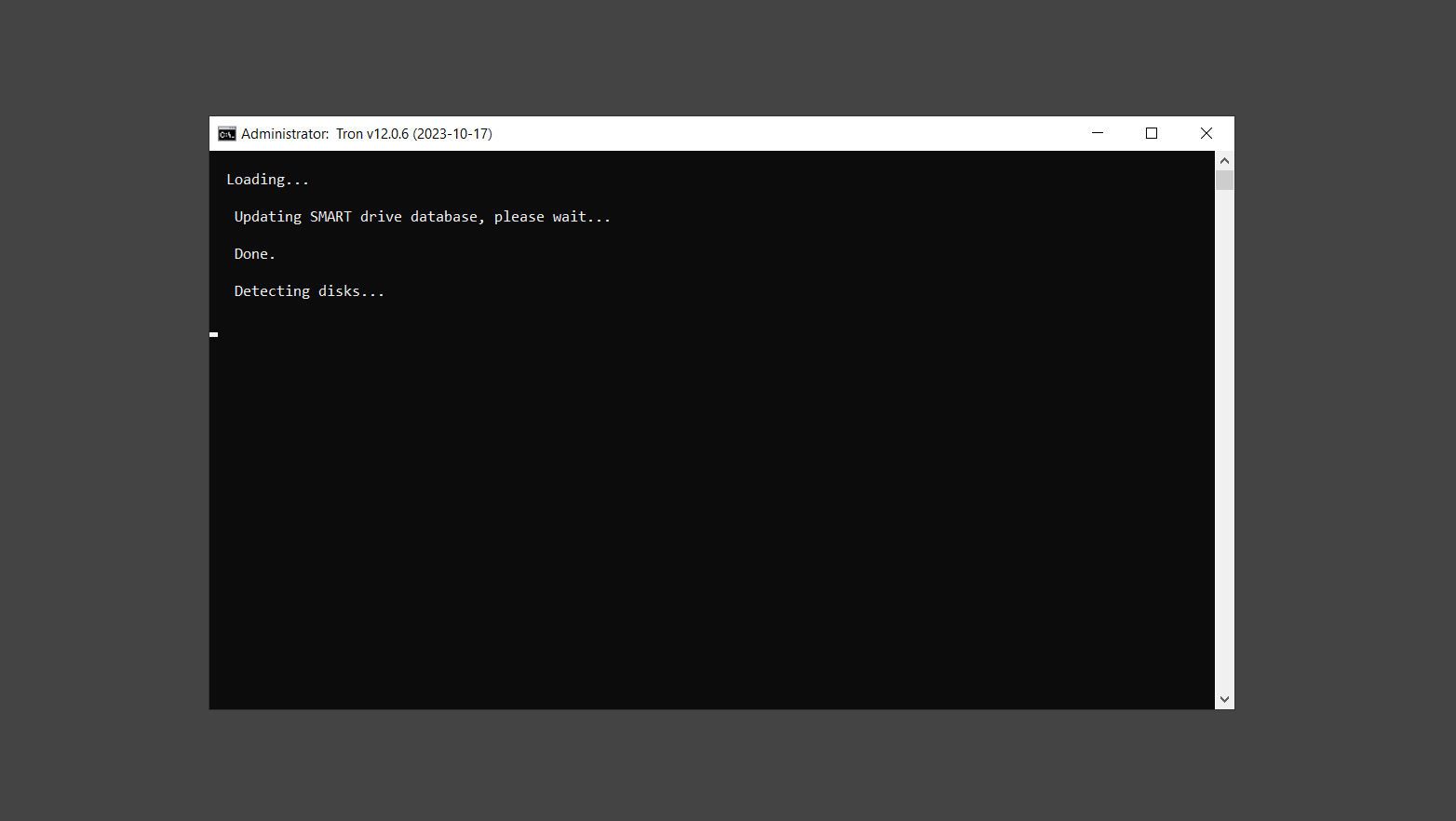
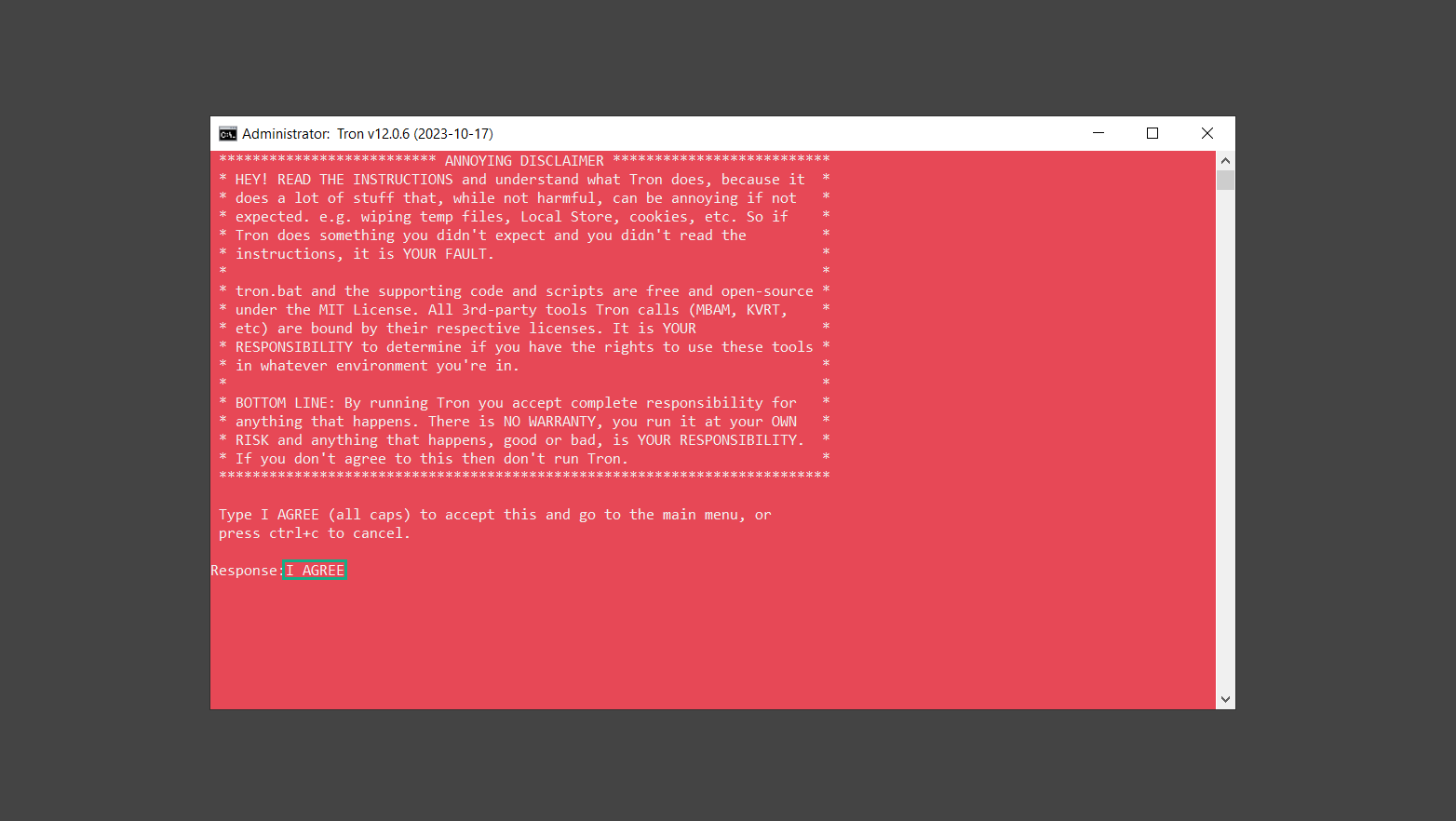
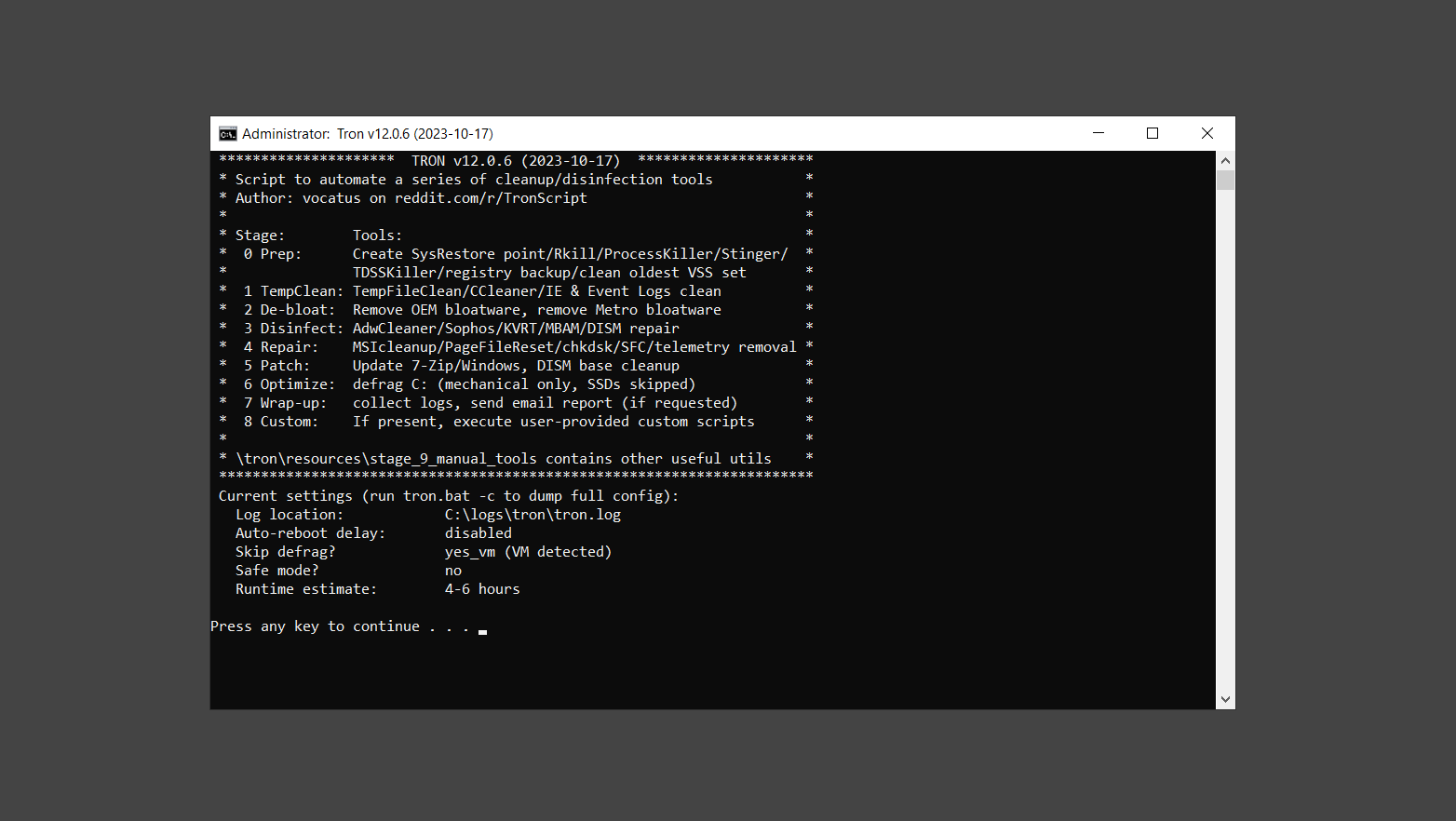
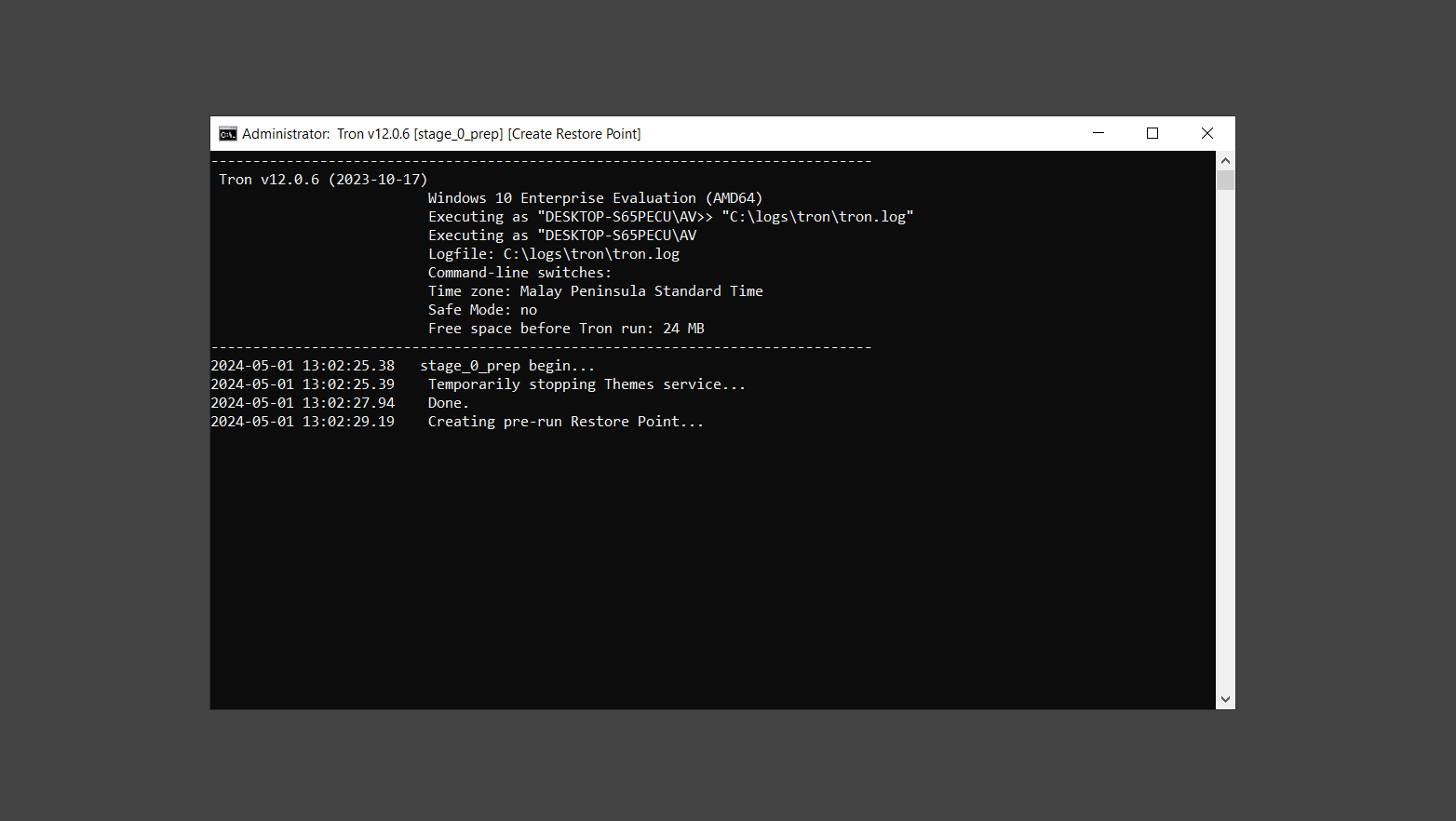
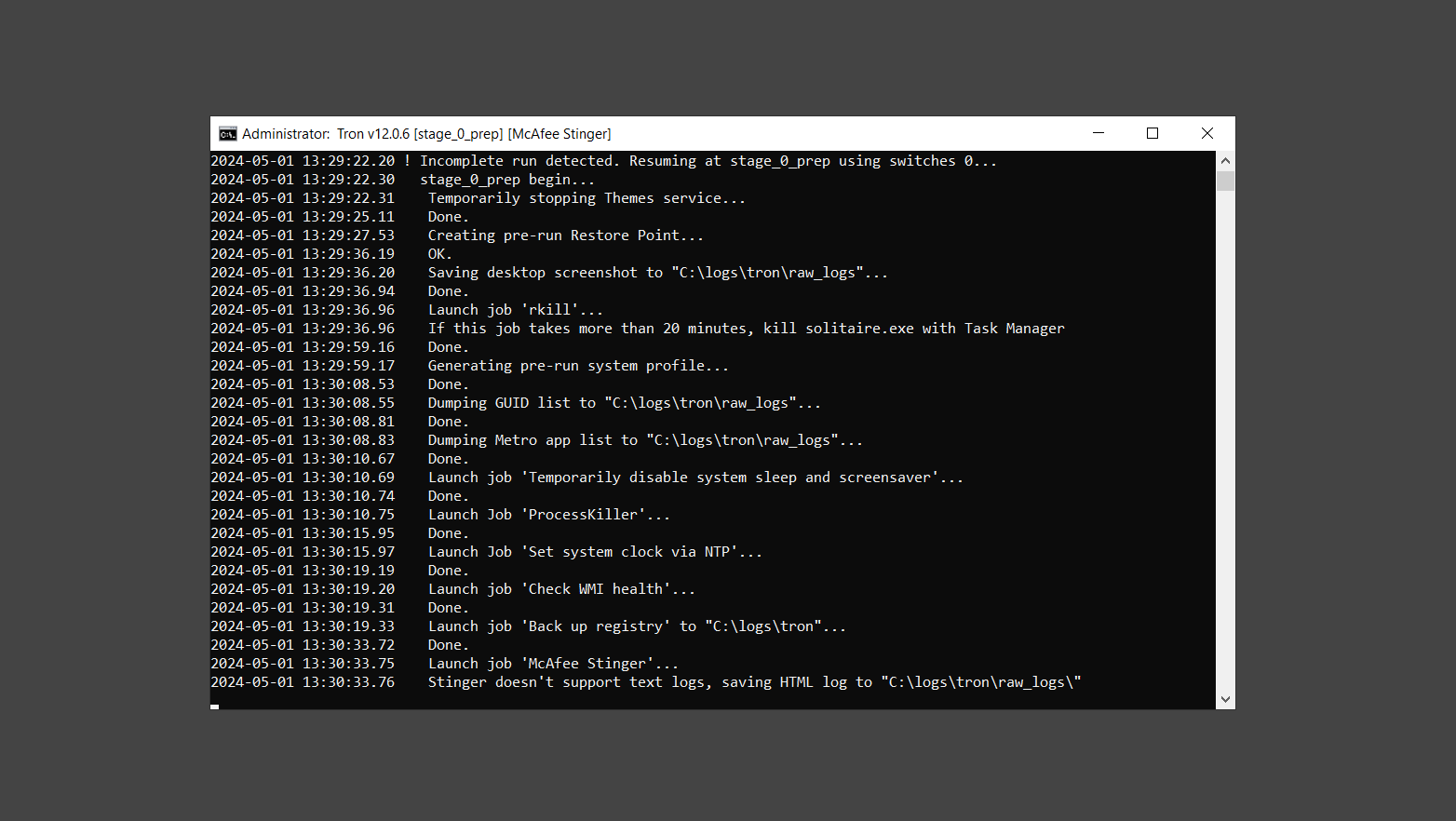
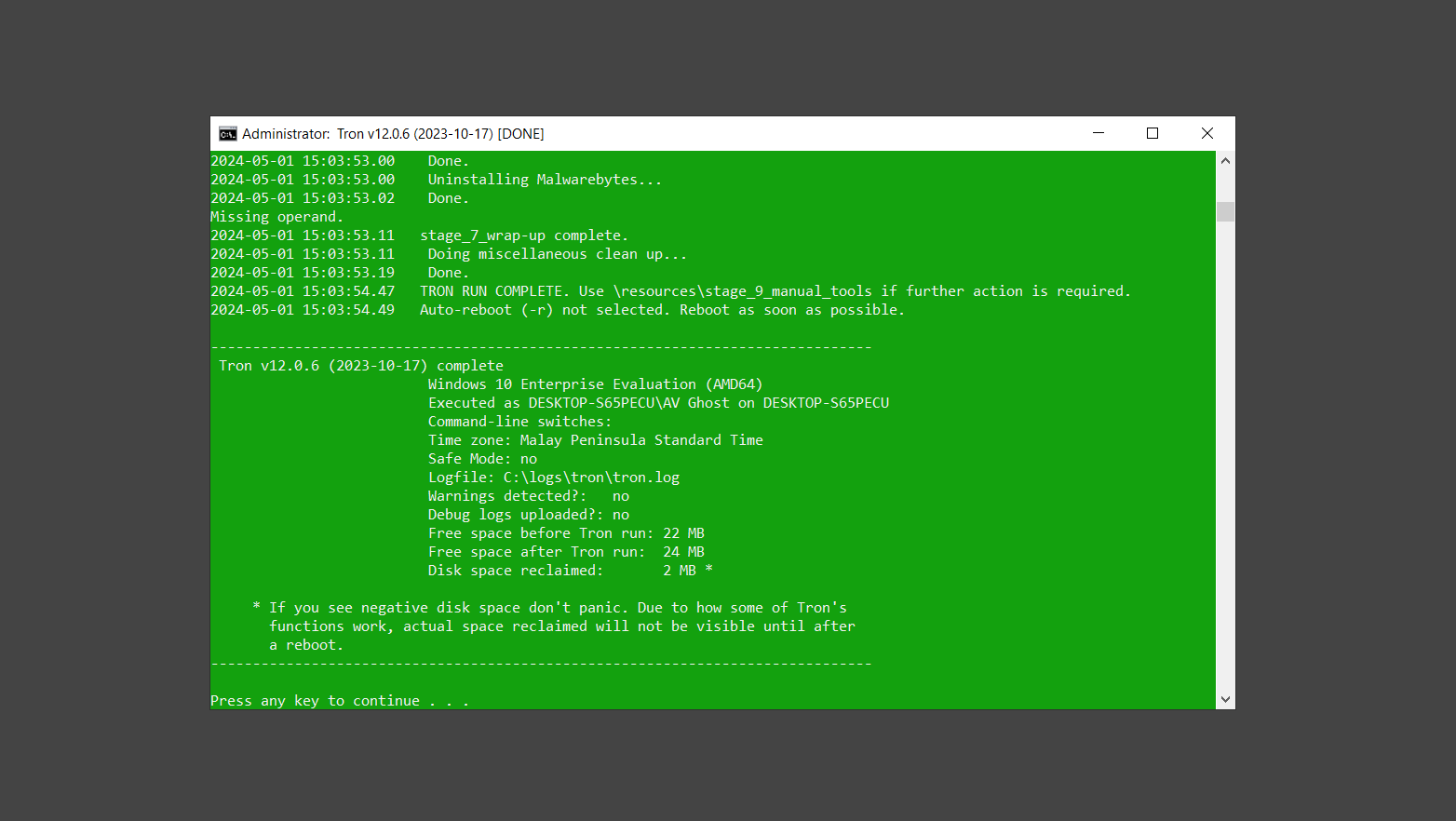
If you are in need of help removing PUADlManager from your computer system, well you came to the right place. This dedicated section will show you how to completely remove the said malware threat from your machine. We considered the technical skills of users on the internet, thus we divided the instruction into Easy Steps and Advanced Steps. One is for tech newbies and the other is for experts. Before that, here’s a quick tip: Before proceeding below, make sure to back up your data to avoid the potential of your files being corrupted or erased accidentally while you follow the instructions. Normally, such scenarios will not occur, but we recommend doing so as a precaution. Some ways you can backup your files: These are only intended to be backups that can be used to restore data in the worst-case situation; otherwise, if no files were damaged, they would be unnecessary. Now, let’s proceed to the guide. For non-tech-savvy individuals who have difficulty using their computer other than basic software and applications. If you are more advanced than this, you can opt for the Advanced steps instead. If you have never heard of Windows safe mode, it is essentially a diagnostic mode in which Windows boots normally but does not load all of the computer’s services and non-critical drivers. This means that safe mode will only launch the services and system processes required to run Windows. In the event of malware infection, this ensures that the computer threat is not running upon boot, allowing us to get rid of it without it interfering with the process. Not only will we put it into safe mode, but we’ll also enable internet connectivity so that we can use the necessary tools and apps in the following steps. Here’s how you can enter safe mode with networking: 1. Open the Run command by clicking the Windows button and the letter R at the same time. 2. Type msconfig on the provided search field. 3. Once the System Configuration program has launched, head over to the Boot tab. 4. Under Boot options, check the Safe boot option as shown below. 5. Under the Safe boot checkbox, you will see other options that have now been unlocked. Click on the Network option to enable networking upon booting up on Safe mode. 6. Select Apply to save your changes upon the next boot. Restart your computer to enter safe mode with networking. 1. Open Windows Settings by pressing the Windows button + I keys together on your keyboard. 2. Go to Update & Security then navigate to the Recovery section. 3. Under Advanced startup, click on Restart now. 4. After the computer has restarted, you will see 3 options, click on Troubleshoot. 5. Select Advanced options then Start-up Settings. 6. The system will boot up and you will be presented with the Start-up Settings. Here, press the number 5 key to finally enter safe mode with networking. 1. Press the Windows key and the letter C to open up the Charms menu. 2. From the right sidebar that opened up, click on Settings. 3. Select Power and then click Restart. You will need to hold the shift button right after the moment you click restart until Advanced Startup presents itself on the screen. 4. After holding the shift button, you will finally be in the Advanced Startup screen. Here, you will see 3 options, click on Troubleshoot. 5. Select Advanced options then Start-up Settings. 6. The system will boot up again and you will be presented with the Start-up Settings. Here, press the number 5 key to finally enter safe mode with networking. 1. Restart your computer and make sure to push the f8 button repeatedly during the boot process. This will boot the computer into the advanced settings rather than the usual startup. 2. Please wait for the system to show the Advanced Boot Options screen. If you started up in standard Windows, restart and try again. 3. Once in the Advanced Boot Options you will be asked to choose an option. Use your arrow keys, mainly up and down to hover into Safe Mode with Networking. Once there, click the Enter button and Windows will now boot into the mode you selected. Check the corners of your computer screen to see if you booted in Safe Mode; the words “Safe Mode” should appear in white text, indicating that you are in the correct boot option. In addition, the background would have turned black, which is entirely normal, and you should not be afraid of it if you believe you did something wrong. We will boot into the normal Windows mode later after we have removed PUADlManager, but for now, let’s focus on the task at hand: getting rid of the malware from the computer. To remove PUADlManager from the system, we must first delete the undesired software or the program to which it is related. This can be done through the Add & Remove Programs section in newer Windows settings, but using the Control Panel’s Programs and Features page is much easier. It will be easier to find the virus because it will include information such as the publisher name, the date from when it was installed, and the version number all in one grid screen. Here’s how to do so: 1. Click on the Windows key to open the Start menu. 2. Type Control Panel in the provided search bar and select the first item from the search results. 3. Click on Programs and inside, select Programs and Features. 4. You will be presented with a list of programs currently installed on your computer. 5. Find PUADlManager and right-click the item then select Uninstall/Change from the dropdown menu. If the software is persistent and will not be removed using standard methods, we will need to use a sophisticated uninstaller to perform the heavy lifting for us. Luckily, such applications exist; Revo Uninstaller is a completely free uninstaller program designed to tackle and erase uninstallable programs in one go. 1. To start, download Revo Uninstaller from the official Revouninstaller.com website. Avoid downloading from third-party sources as they may contain additional bloatware upon installation. 2. On the download page, opt for the free version of Revo Uninstaller as it has all the features we need. Click on Free Download to begin downloading the setup file. 3. The revosetup.exe file would have started downloading. Click on it to start installing the software. 4. Revo Uninstaller setup would now begin and follow the typical setup procedure such as selecting your setup language, accepting the license agreement, and selecting the installation location. Once setup is ready click Install. 5. After the setup is finished, check the Launch Revo Uninstaller option to open the program upon closing the installer. 6. Once Revo Uninstaller has opened, it will show you the list of applications currently installed on the computer. Find PUADlManager, right-click it, and select Uninstall from the drop-down menu. (We will be using PC App Store to demonstrate.) 7. A confirmation message stating if you are sure you want to uninstall the said program, click Continue. 8. Follow the uninstallation instructions and this time, Revo Uninstaller would have forced the program to continue with the uninstallation compared to the previous attempt via Control Panel. 9. You will be notified that the software has been uninstalled, Revo Uninstaller will now conduct a preliminary examination and get rid of additional files and registries related to PUADlManager. 10. On the selection of Scanning modes, select Advanced to make sure everything is scanned without leaving a single directory unnoticed. 11. Wait for the scan to finish as Revo Uninstaller is checking for residual files and registries related to PUADlManager. 12. Revo Uninstaller may have found leftover Registry items, click Select All and proceed to delete them by clicking the Delete button next to it. After that, click Next. 13. It may have also found some leftover files and folders, simply do the same by clicking Select All and deleting them. Now click Finish and the uninstallation of PUADlManager is done. Cybercriminals may believe they can fly under the radar of a malware scan. However, if we scan the computer using several scanners, the malware they developed will never see the light of day. Here’s why it’s necessary… As full-time security professionals, we’ve seen security programs like antivirus and malware removal solutions with their vast and extensive database of threat signatures that they use to find malware. However, newly developing threats may not be recognized in the early days of infection since the threat signatures are not yet researched and added to the detection database. It may eventually get found, but it might be too late for the infected machines. Upon research, newer malware variants often have identical strings and signatures similar to older malware in certain security software’s databases, which is why certain antivirus software can detect such malware while others cannot. Since identifying the infection may be difficult for non-tech-savvy individuals, we will need the help of multiple security software to do the work for us. Please run each security software individually. You may do so in any order. Kaspersky Virus Removal Tool is an excellent tool for scanning and disinfecting malware-infected computers. Please note that this tool is separate from the mainstream Kaspersky security applications, so worry not about the company’s controversies. 1. Download the Kaspersky Virus Removal Tool from the official Kaspersky website. 2. After the executable file (KVRT.exe) has finished downloading. You can run the program right off the bat as it does not require to be installed in the system. 3. Read the End User License Agreement, Privacy Policy, and KSN Statement then tick the checkbox to agree with the terms and conditions. Click Accept to proceed. 4. Wait for the system initialization process to complete as it runs and check if your system is compatible with running the virus removal tool. 5. Click the Change parameters button to set the scope for the scanner. 6. Select all the checkboxes for the objects to scan to find malware within all the directories and drives of the computer. Then click OK to proceed back to the home screen. 7. Now we are ready to scan, click the big Start scan button and the Virus Removal Tool will now get to work. 8. Wait patiently until the scan is complete. A notification with a request for action will be displayed if threats are found within the computer system. 9. From the Please select action drop-down menu of each detected object, choose Delete to fully get rid of the threats found by the tool. 10. Click Continue to proceed with deleting the detected malware threats from your computer. As the name implies, the Emergency Kit software by Emsisoft is a must-use in your malware scanner arsenal. It features the same powerful scanning technology used by their flagship software, Emsisoft Anti-Malware. 1. Go to the official Emsisoft website and download the Emsisoft Emergency Kit portable software. 2. After downloading the executable program (EmsisoftEmergencyKit.exe), you can run it straight from your downloads folder. 3. When presented with the User Account Control window, click Yes to allow the program to begin running on the computer. 4. Agree to the license and maintenance agreement and select your destination folder for the program. Then click Install to proceed. 5. Once the Emergency Kit program has launched, click Malware Scan from the homepage to initiate the scanning process. The program will be scanning the computer and it might take long depending on how many files you have as well as the hardware capabilities of your system. 6. After the scan has finished, Emsisoft Emergency Scanner will show you the list of files detected by the software. Click on Quarantine selected to remove the threats from your computer. 7. Emsisoft Emergency Scanner may also require you to restart your computer to finish the malware removal process, simply click Reboot to restart your PC. ESET Online Scanner is a program that is designed only to remove malware threats from your computer for free. It is simple to use and features an advanced malware detection system. There is no need for registration, free trials, or anything else. Simply download, execute, and remove the malware. 1. To start, go to the official ESET website and download the latest Online Scanner. Scroll down until you find the Download button. 2. The file Esetonlinescanner.exe would have been downloaded on your computer after clicking the download button. Simply run the said file to begin the program. 3. ESET Online Scanner will need to be initialized before proceeding to be used, select your desired language and click on Get started. Follow the on-screen instructions until the homepage shows up. 4. Click on Computer scan, then select Full scan from the three options available. 5. Give the program permission to detect and remove potentially unwanted apps by selecting the Enable option. Then click Start scan to begin the process. 6. Wait for the ESET Online Scanner to finish scanning your system for malware. After the scan, ESET Online Scanner would have automatically deleted the detected threats. Click Continue to finish the malware removal process. Let us perform one last scan of the computer with one of the well-known tools for detecting malware and viruses. Malwarebytes Anti-malware is well-known in the security field; they have helped many people with malware issues through their software, and downloading it will help you as well. Note: We will only use the free version of Malwarebytes because it includes all of the capabilities we require. 1. To begin, head over to the official website of Malwarebytes Anti-malware and click the Free Download button. 2. Malwarebytes will begin downloading the installation file (MBSetup.exe). Run the executable file after it has finished the download. 3. The User Account Control window may pop up, simply click Yes to allow the program to run. 4. The Malwarebytes setup wizard will launch, click on the Install button to proceed. 5. Malwarebytes will ask you to install the Browser Guard extension. You can opt to download it, depending on whether you want it on your browser or not (It is completely free). 6. Please wait as the Malwarebytes Setup installs the antimalware program. Follow the on-screen instructions until you have successfully installed Malwarebytes. 7. Now that Malwarebytes Anti-malware is installed, begin by opening the program for the first time. You will receive a 14-day free trial if this is the first time you install Malwarebytes. 8. You will be taken to the main dashboard of the program, from here, we can begin scanning the computer by clicking the Scanner box at the middle. 9. Once you are on the Scanner page, you will not click Scan just yet. Instead, click on Advanced scans below it. 10. Click on Configure scan inside the Custom scan section. This will allow us to customize how the program scans the computer. Simply hitting scan upon installation won’t show its full potential. 11. On the Configure Custom Scan page, check the box beside Scan for rootkits to find hidden malware. In addition, tick the boxes near all the drives you have on your computer so Malwarebytes can scan them. 12. After configuring the Custom Scan settings, click on the Start Custom Scan button to begin the process. 13. You will see a side window showing the progress of the computer scan. Please wait until Malwarebytes has scanned the whole system for malware. 14. Once the scan is complete, a list of detected threats will show up. Check the boxes near all the malicious files and get rid of them from the computer by clicking Quarantine. Malwarebytes may require a computer restart, please do so if prompted. Since the first three programs mentioned above are all portable, you can always run them straight from your downloads folder whenever you feel the presence of malware in your computer. We recommend that you organize them all into a single folder for future use. After doing all the steps above and making sure that malware is nowhere to be found in the computer, we will now begin to exit safe mode and return to the normal Windows mode where all of your files and programs are operational. Here’s how to exit the Windows safe mode: 1. Click the Windows button and letter R at the same time to open the Run command. 2. Type msconfig on the provided area and hit enter. 3. Once the System Configuration program has launched, head over to the Boot tab. 4. Under Boot options, uncheck the Safe boot option. 5. Select Apply to save your changes upon the next boot. Restart your computer once again and you will be back to the operational Windows mode. Hey, you did it! You have successfully removed PUADlManager on your computer as well as other malicious threats that were hiding alongside it. Now you can use your system with a piece of mind. If the said steps did not work or the malware is still present, you can follow the advanced steps provided below. Although it may be quite difficult for an average computer user, we have made it detailed and easy to understand. For users who know their way around the computer and have the capability to diagnose malware using their skills and understand how to use utility tools available in the system. PUADlManager and malware threats alongside it could have been hiding in the system as Windows services and processes. If the malware is a service, it can have bad effects on the computer system as a whole. They can create or modify existing services, basically tainting them, particularly for persistence, but can also be used for granting further privileges to malware inside an infected system. In order to find unwanted services as well as processes from running in the computer and causing further harm, we will be using Process Explorer, an alternative to the Windows Task Manager and is a part of the Sysinternals suite. Here are some of the features of Process Explorer: Process Explorer is a tool that is frequently used to analyze malware which is why it is the perfect fit to use in this particular case. How to find and remove malware via Process Explorer: 1. Download and run Process Explorer from the official Microsoft download page. 2. Upon opening the tool, you will see a list of processes running on the system. Alongside them have a designated color based on the type and current state of the process. The default color scheme is as follows: 3. Now we will begin hunting for malware using Process Explorer. There are many ways to find malware within the vast number of processes shown. You can narrow down the scope to Services, Packed Images, and Jobs and exclude a few like Suspended Services and Deleted Objects. Here are the ways you can check if a process is malware: 4. We can also verify if an executable file or a DLL has trusted signatures by enabling the Verify Image Signatures from the Options tab in the menu bar. 5. To further dig deep into the suspected process, we can submit it to VirusTotal and check if their antivirus engines have already been flagged as malware. We can do this by clicking Options on the top menu bar and clicking VirusTotal.com. Now you can right-click the processes and the Check Virustotal.com option will be enabled. 6. Once you have determined that a certain process is malware. Whether all suspected conditions are met or VirusTotal has flagged it numerous times. Kill/terminate the said process, open its path, and delete it from the system. (Tip: You can see its file location by hovering your mouse over the process.) You may be able to find two or more malicious items therefore you should carefully look for suspicious processes before exiting the Process Explorer. Autoruns is another tool that is a part of the Sysinternals suite. It is a piece of software that is used to find processes that are configured to run upon system boot-up or whenever a user logs in to the computer. We will use Autoruns to find threats inside a compromised system. Any installed malware will have the capability to survive a computer reboot. 1. First off, download the Autoruns tool from the official Microsoft website. Extract the zip folder and begin running the tool. 2. If this is the first time you have used Autoruns, then you may be probably overwhelmed at first. It consists of multiple tabs that each contain autostart mechanisms. Here are what to expect in each tab: There are more tabs within Autoruns but the ones mentioned above are where you will want to check for malware. 3. In order to make the search for malware easier, we can exclude verified processes and entries from displaying. To do this, click Options, from the menu bar then tick Hide Microsoft Entries. 4. Now, check the tabs for malicious entries. We can do so by checking whether the entry has a verified publisher and a description. The Image Path also indicates where the file is located, so a suspicious directory such as the Temp folder will be a red flag. 5. After investigating the files, we can right-click the file/s of suspicion and click Check VirusTotal to scan the entry for malware. This will scan the entry using multiple antivirus engines. (The scan results will be displayed on the right corner of the entry next to the Timestamp.) 6. Once VirusTotal has displayed how many antivirus vendors have flagged the file as malicious. Right-click the entry and select Delete to stop it from running. Confirm the deletion by selecting Yes when prompted if you are sure you want to do so. Norton Power Eraser can be described in a single word: false positives. The tool is notorious for not leaving any trace of malware unnoticed on the computer, therefore it always detects normal processes and programs as well. The reason this is in the advanced steps is because it requires the skill to be able to discern between legitimate and harmful programs. In this instance, the Norton Power Eraser is an extremely effective tool to utilize. It effectively narrows your search for malware. 1. To begin with, download Norton Power Eraser from the official website. 2. NPE.exe would have begun downloading on the computer. Wait for it to finish then run it afterwards. 3. If the User Account Control window pops up, click Yes. 4. Read the program’s license agreement and click Agree. You will only be prompted upon the first launch. 5. Once the Norton Power Eraser home menu has opened, select Settings, toggle the Include Rootkit Scan option, and click Apply. This will allow the program to scan for hidden malware on the computer. Do note that this will require a computer restart. 6. After the system has restarted, open Norton Power Eraser, select Full System Scan, and click Run Now to start the process. 7. Wait for the scanning process to finish. This will depend on how many files you have on your computer, as well as the hardware capabilities of your system. 8. Once the scan is complete, Norton Power Eraser will show all the detected threats onscreen. Take action by clicking Delete/Fix on the right side of each item. After that, click Close to finish the process. On the other hand, if no threats are found, click Done. Norton Power Eraser is a portable tool that does not need to be installed to work. Therefore you can always run it at your disposal whenever you believe your computer is infected with malware you cannot find. The Tron script fights for the user, therefore it is one of our all-time favorites; it uses practically every removal and optimization method known to man, all with the touch of a single button. It automates functions and programs for removing malware and bloatware, as well as cleaning up the computer, so the user behind the screen doesn’t have to do any work at all. With that being said, let us proceed and use the Tron script to clean the system: 1. Go to the official download page of the Tron script and begin downloading an executable (.exe) file copy. 2. Extract the downloaded Tron file, with the use of an archiver like 7-Zip. Please keep in mind that you will not run the Tron script exactly as it is downloaded. You’ll need to extract the.exe first. 3. After extracting the compressed file, open the Tron folder, right-click the Tron script, and run it as administrator. 4. The Tron script would have opened up and initialized by updating the database and checking the repo. 5. Once the initialization is finished, the disclaimer will be shown on the screen. Read it and type I AGREE in all caps to continue. 6. After agreeing to the disclaimer, it will show your current settings, as well as the Runtime estimate on how long the script may run. Press any key to begin running the Tron script on the system. 7. It will create a system restore point before beginning the process so if you run into any issues after running the script, you can always restore to the point it created before it started. 8. Please wait for the whole process to finish. You may see Tron script download and run multiple programs on the computer but it will uninstall them after finishing the process. This might take a long time as shown on the Runtime estimate. 9. Once everything has finished, the CMD window will have turned green which indicates that the process is a success. Press any key on your keyboard to close the Tron script. 10. To finalize the Tron script process, we recommend that you restart your computer. After restarting your computer, you should no longer see the presence of PUADlManager or other malware threats. You can always use the Tron script as a last option if you believe your machine is infected and there is no chance of detecting the malware. As the saying goes: “The biggest vulnerability is the person behind the screen“ So, here are some tips and what you need to know in order to keep your device safe and malware-free in the long run. Make sure that all of the programs in your computer is up-to-date with the latest version released by the developer. The reason behind this is that these updates frequently tackle bugs and issues that malware actors often exploit. The same goes for your computer’s operating system, make sure Windows is up-to-date with the latest software update to prevent malware from exploiting a hidden vulnerability. One of the biggest sources of malware infection in a computer system is third-party installations. This happens when a user downloads a certain program from sources that are not the official download links. Some of the common types of sources where malware is present are torrent files, cracked software, and games. Malware often disguises itself as resumes and quotations and threat actors often send thousands of these infected emails to company employees around the world in order to infiltrate their network. Always check where your emails are coming from as there may be a chance that the project attachment you received via email did not actually come from a co-worker. Avoid visiting websites that contain unfiltered advertisements such as illegal streaming websites, cracked software platforms, and links sent out to you by somebody you do not trust. These sites are often linked to redirect chains that load once you click on an ad element on the page. Following this chain often leads to drive-by malware and phishing pages that an average user may eventually fail to notice.How to remove PUADlManager
Easy steps
Step 1: Boot into safe mode with networking
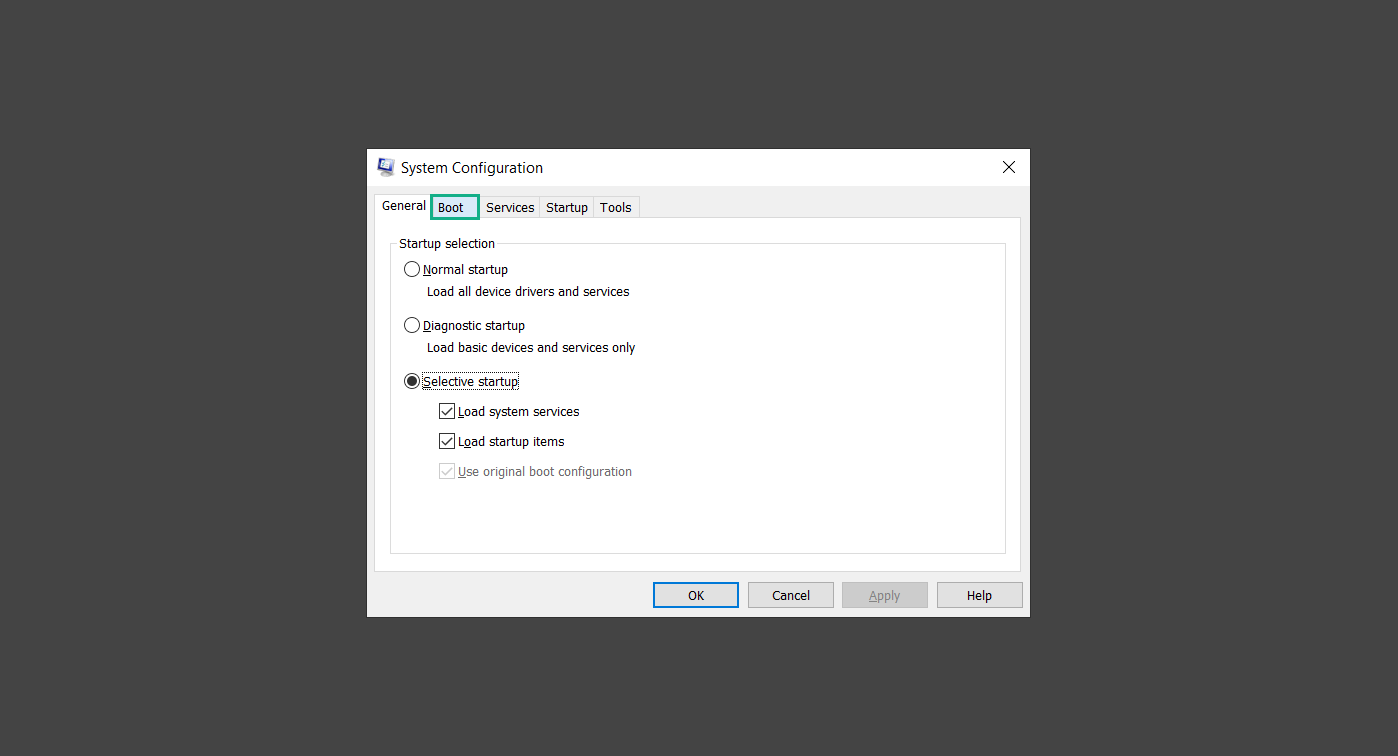
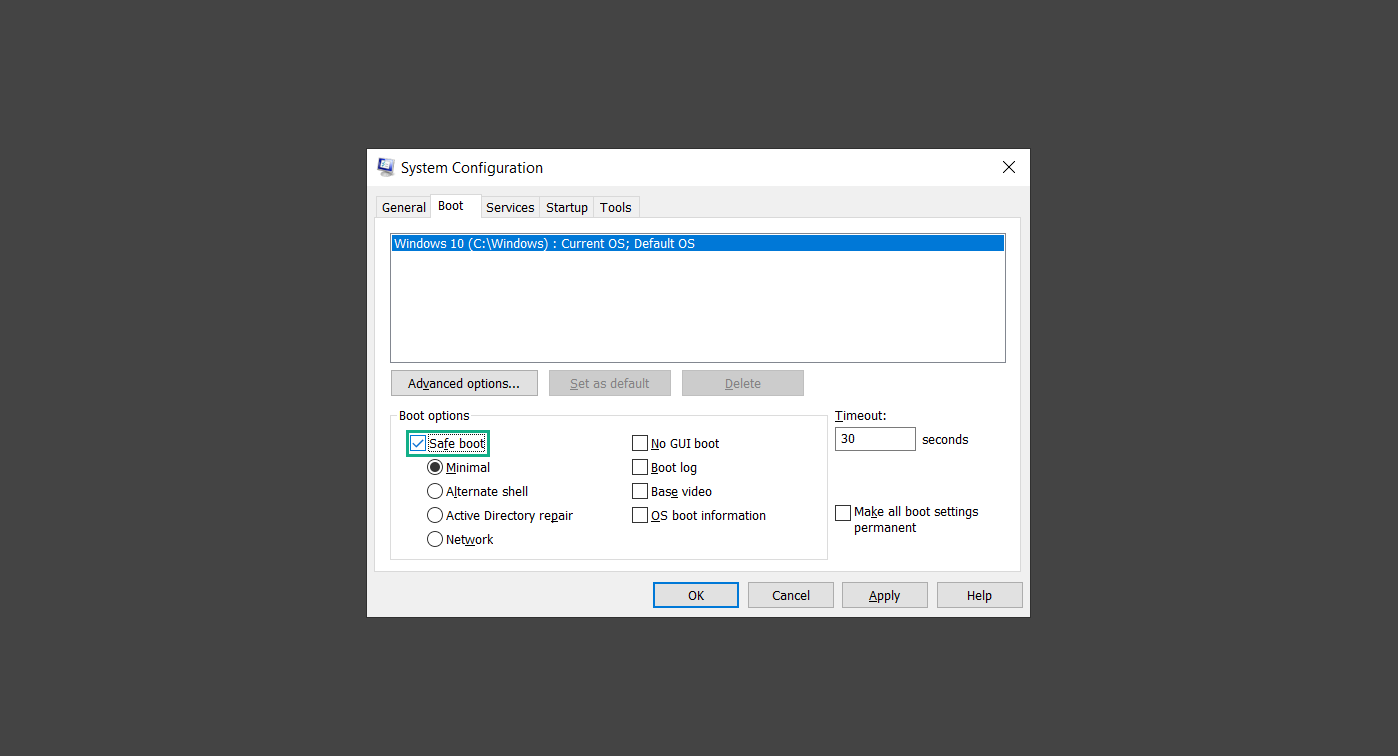
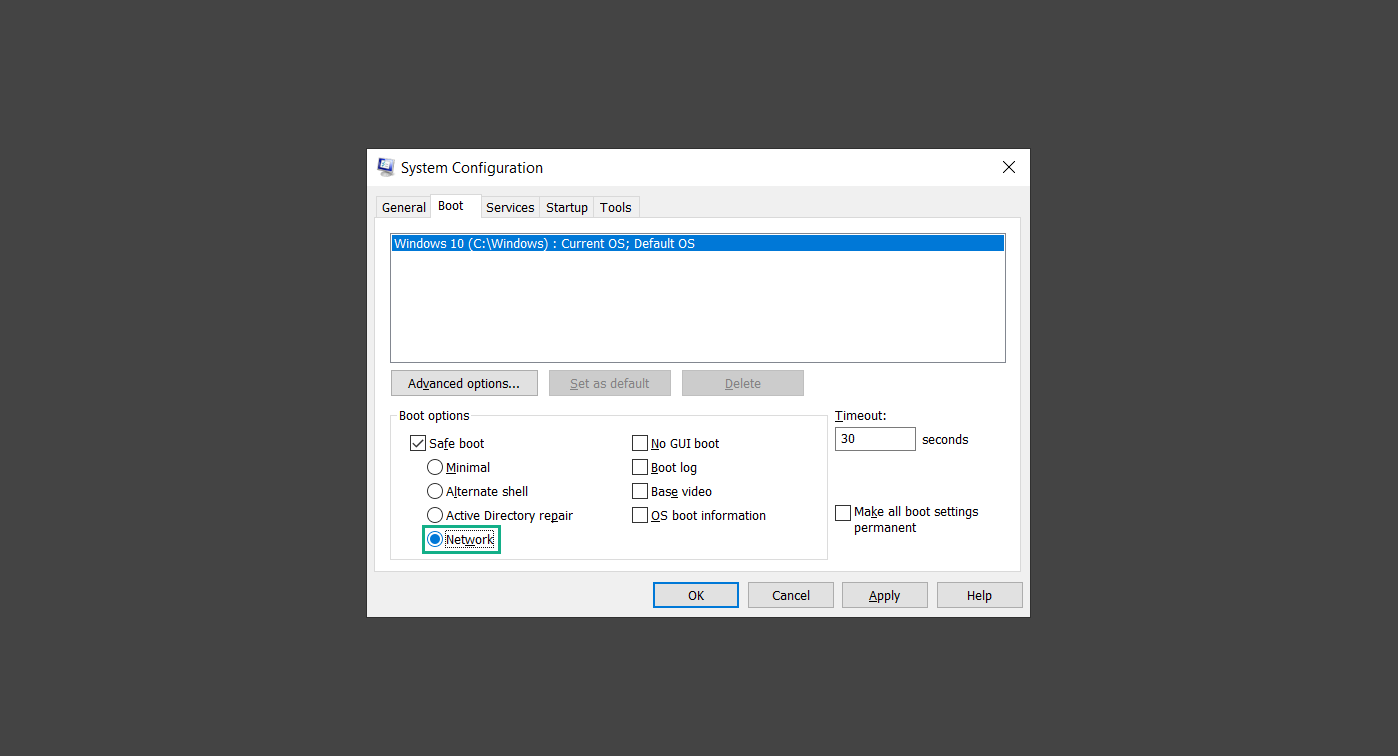
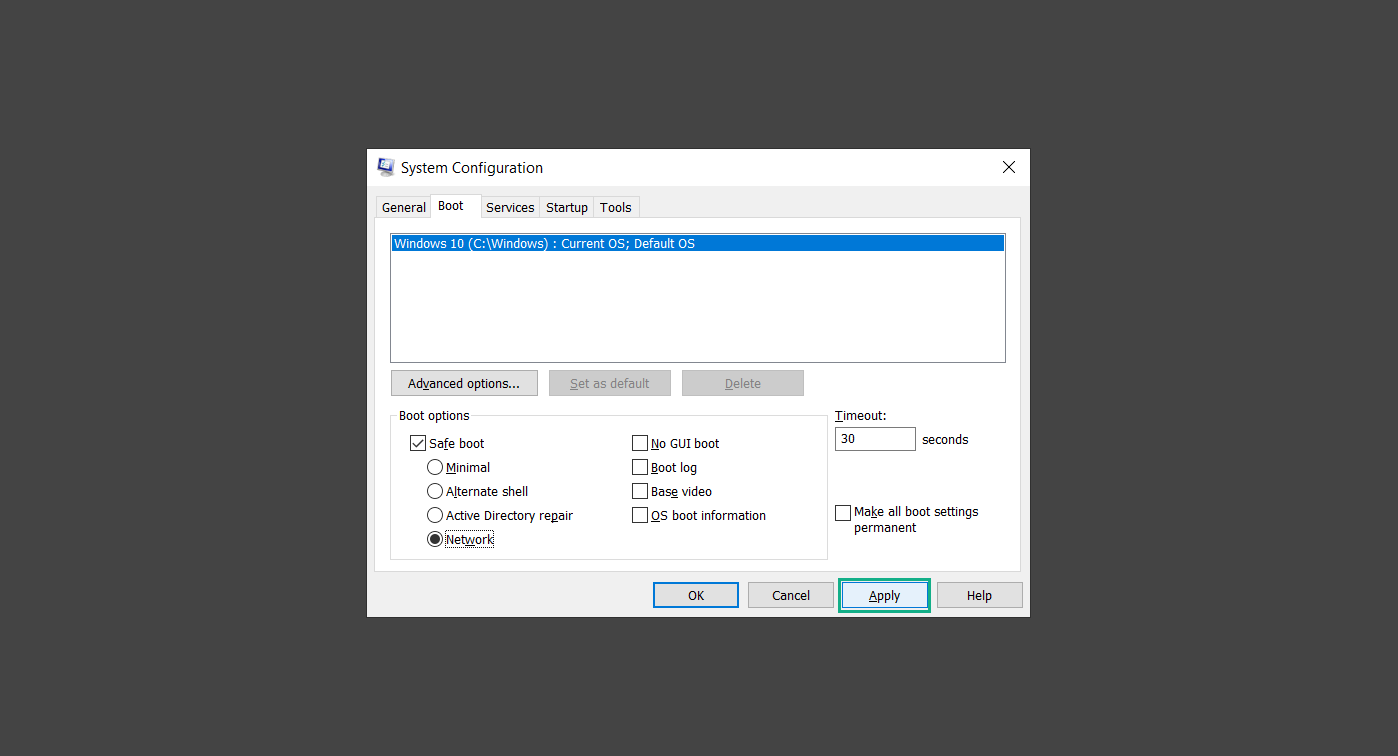
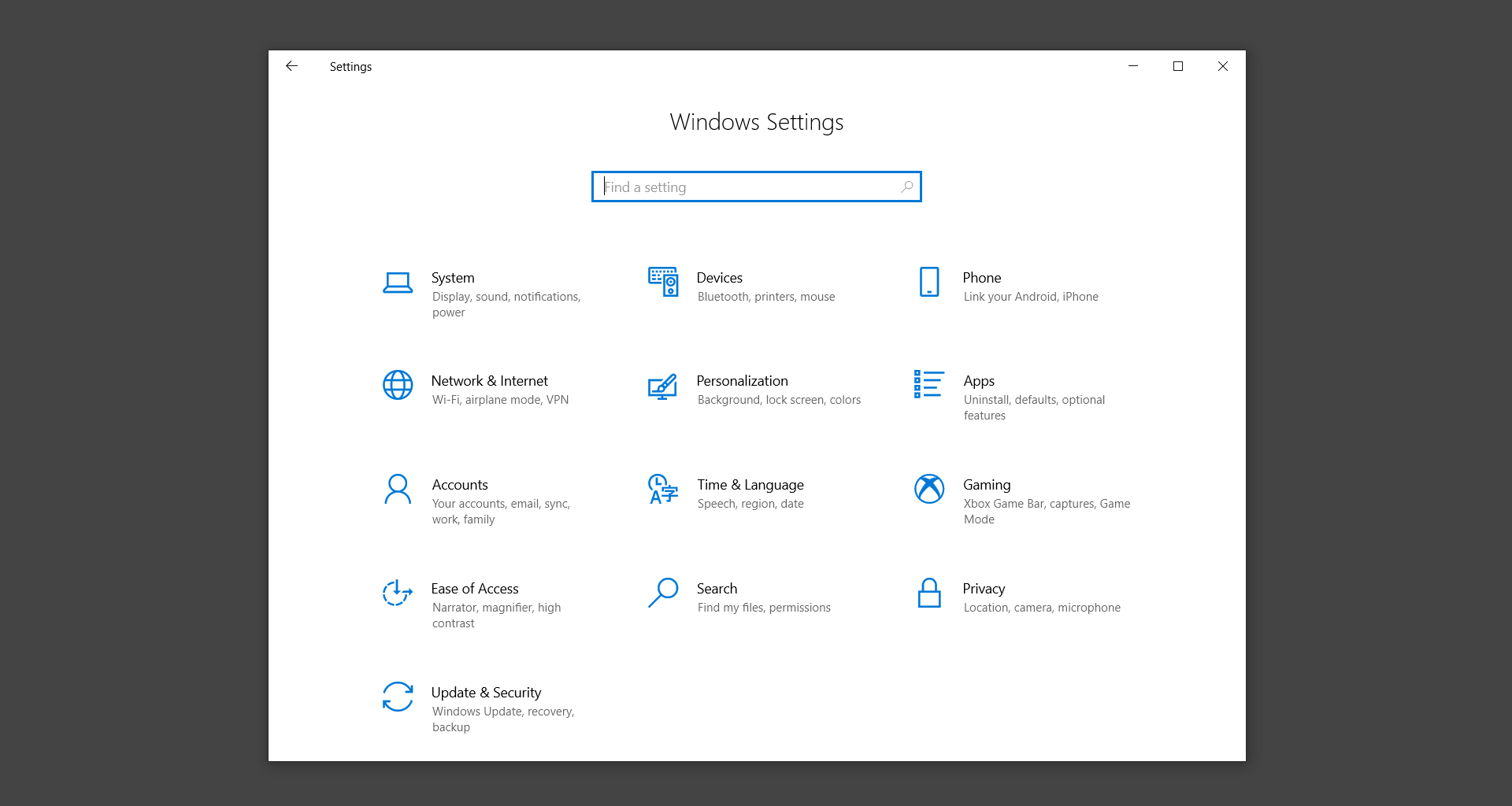
Step 2: Delete PUADlManager from the computer
![]() Uninstall PUADlManager using Revo Uninstaller
Uninstall PUADlManager using Revo Uninstaller
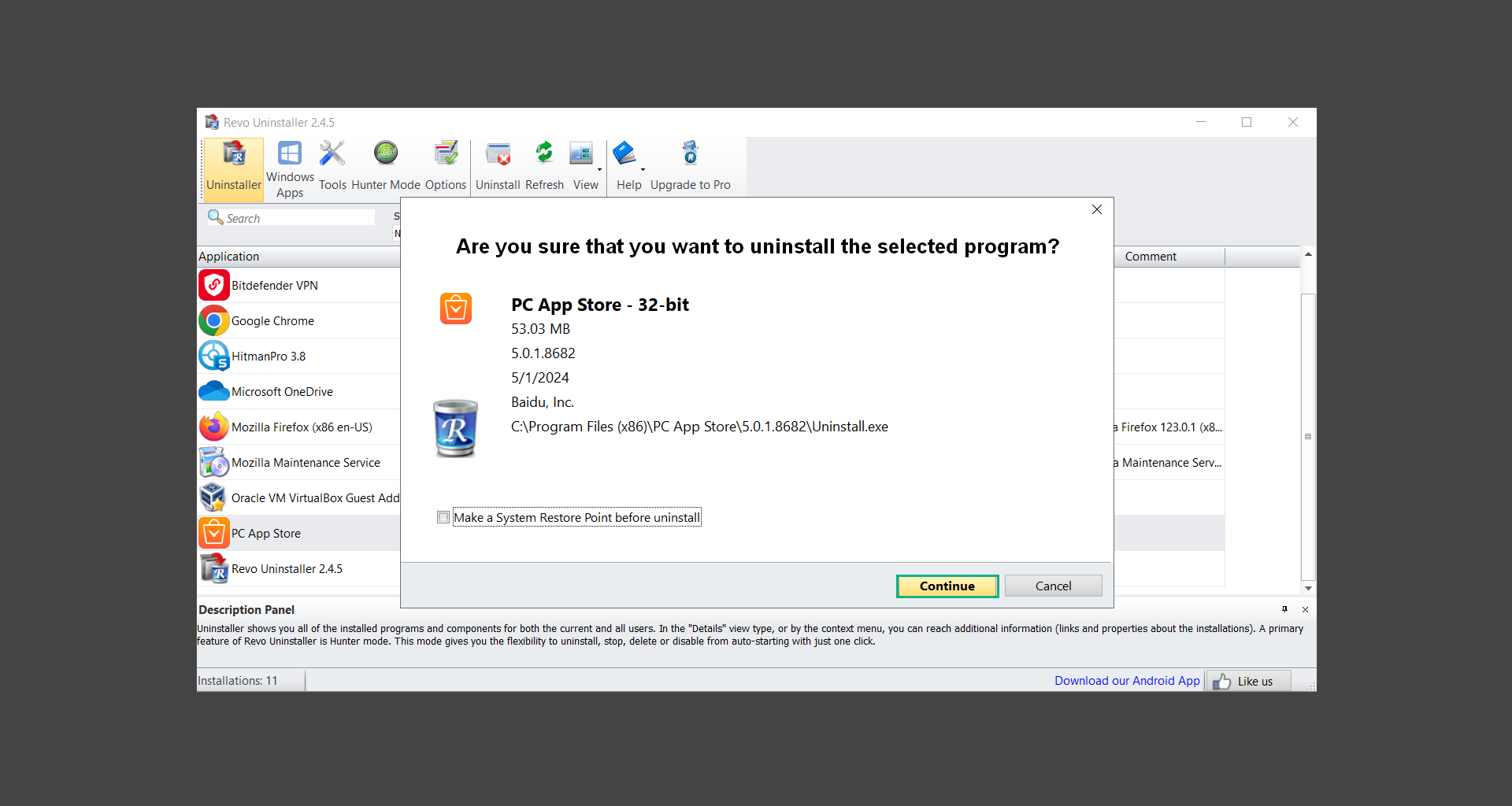
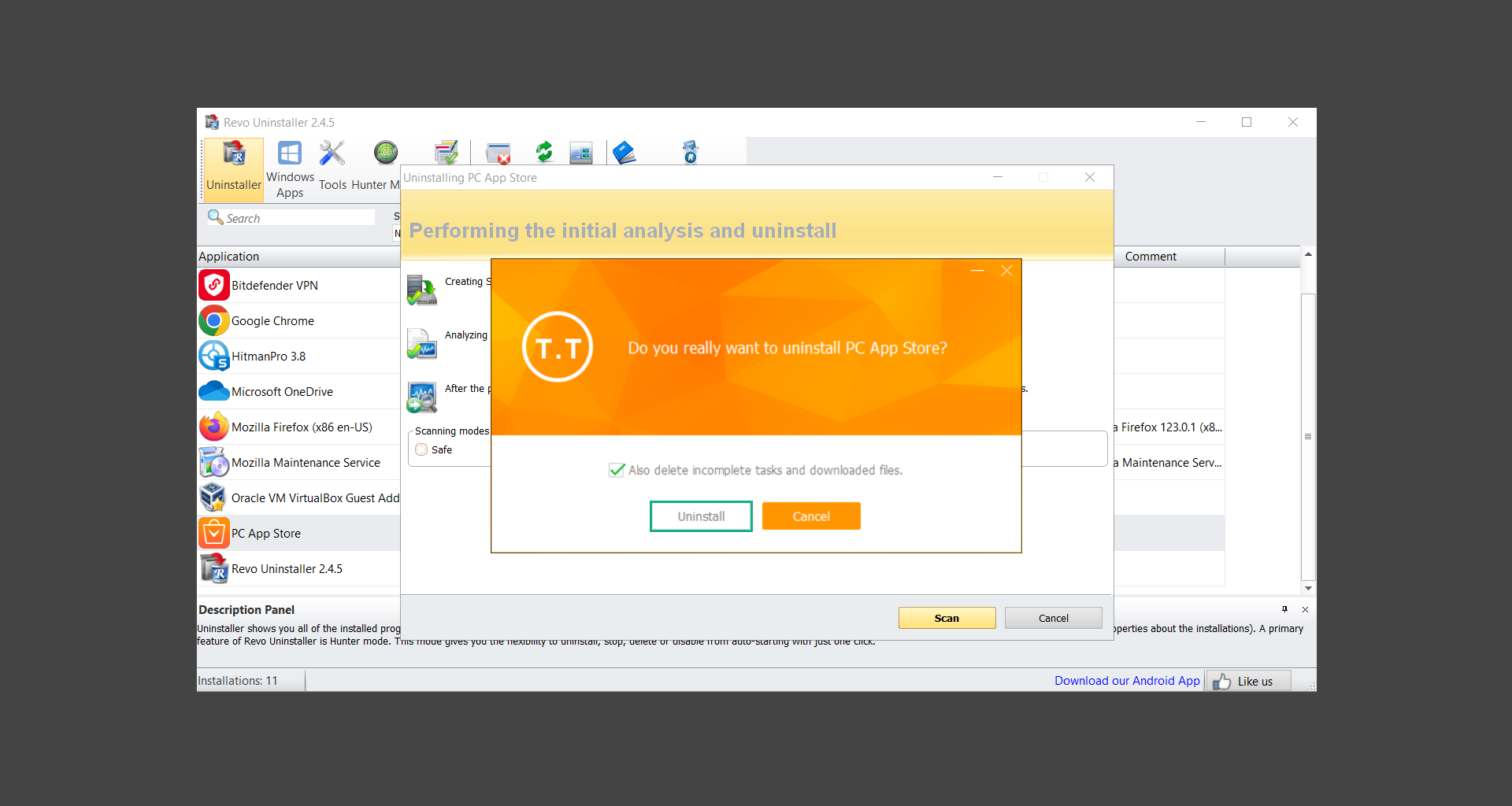
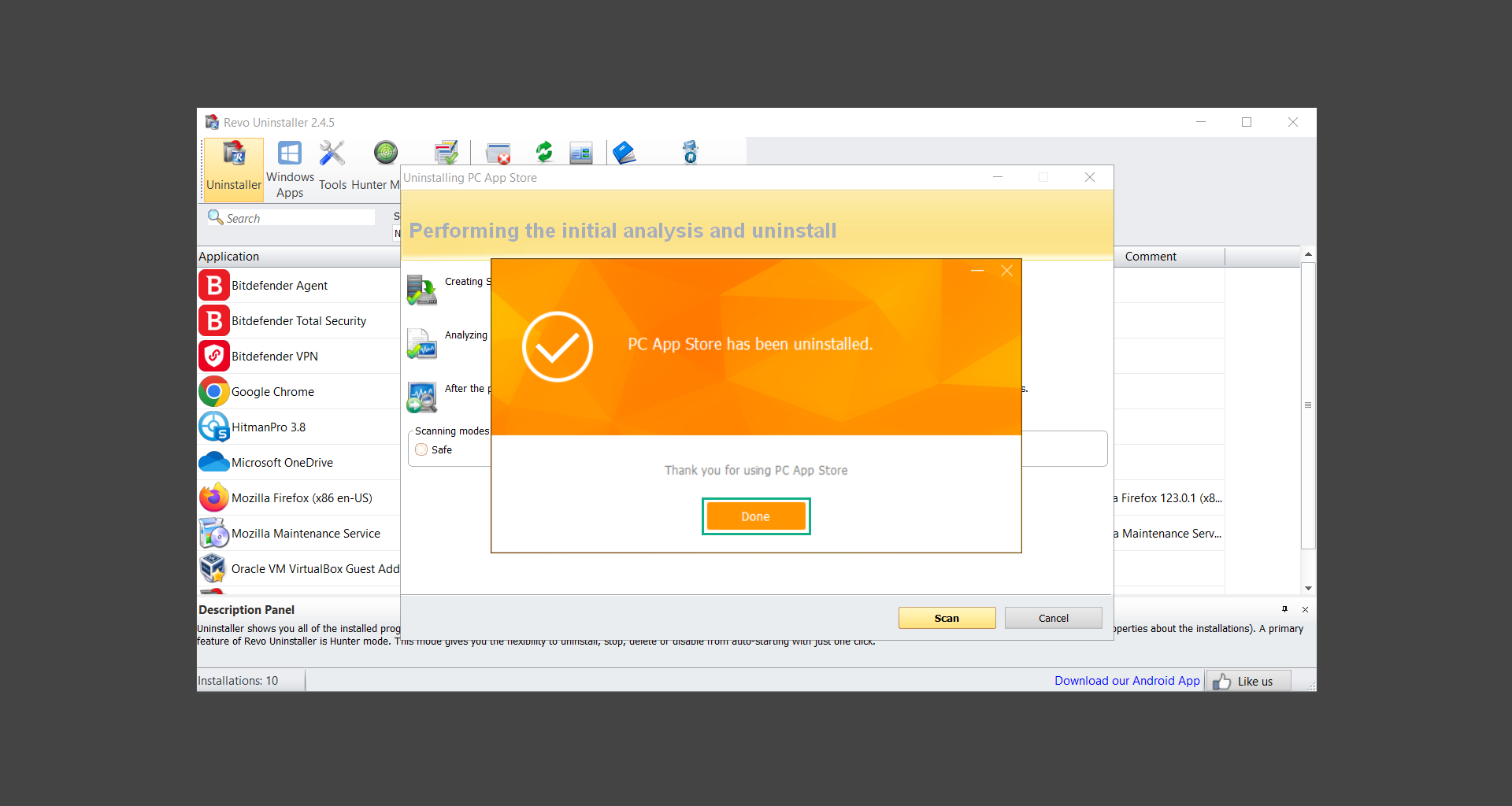
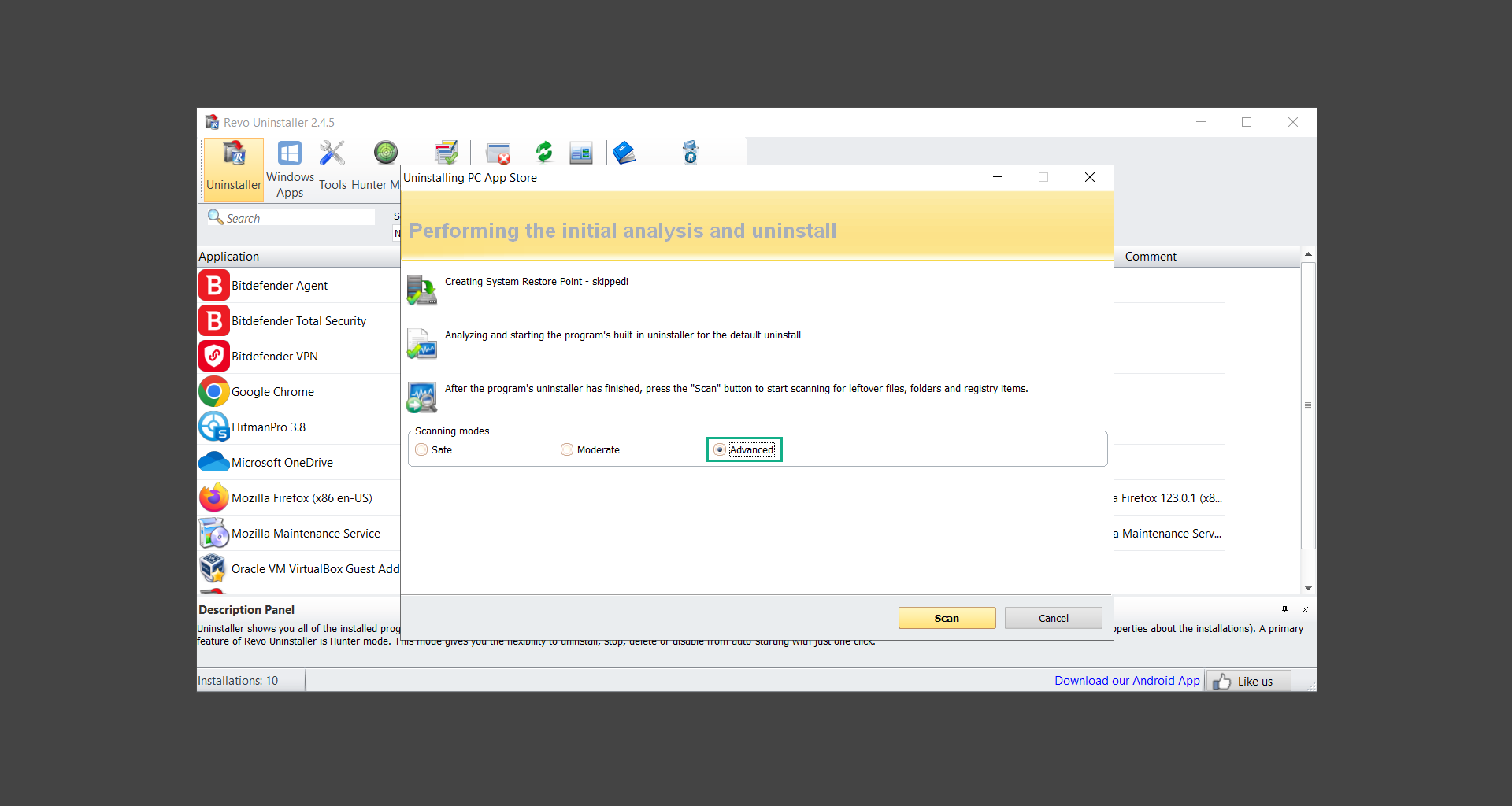
Step 3: Run several malware & virus scans
Now let’s exit safe mode and we’re done


Advanced steps
Step 1: Use Process Explorer to detect and remove malware
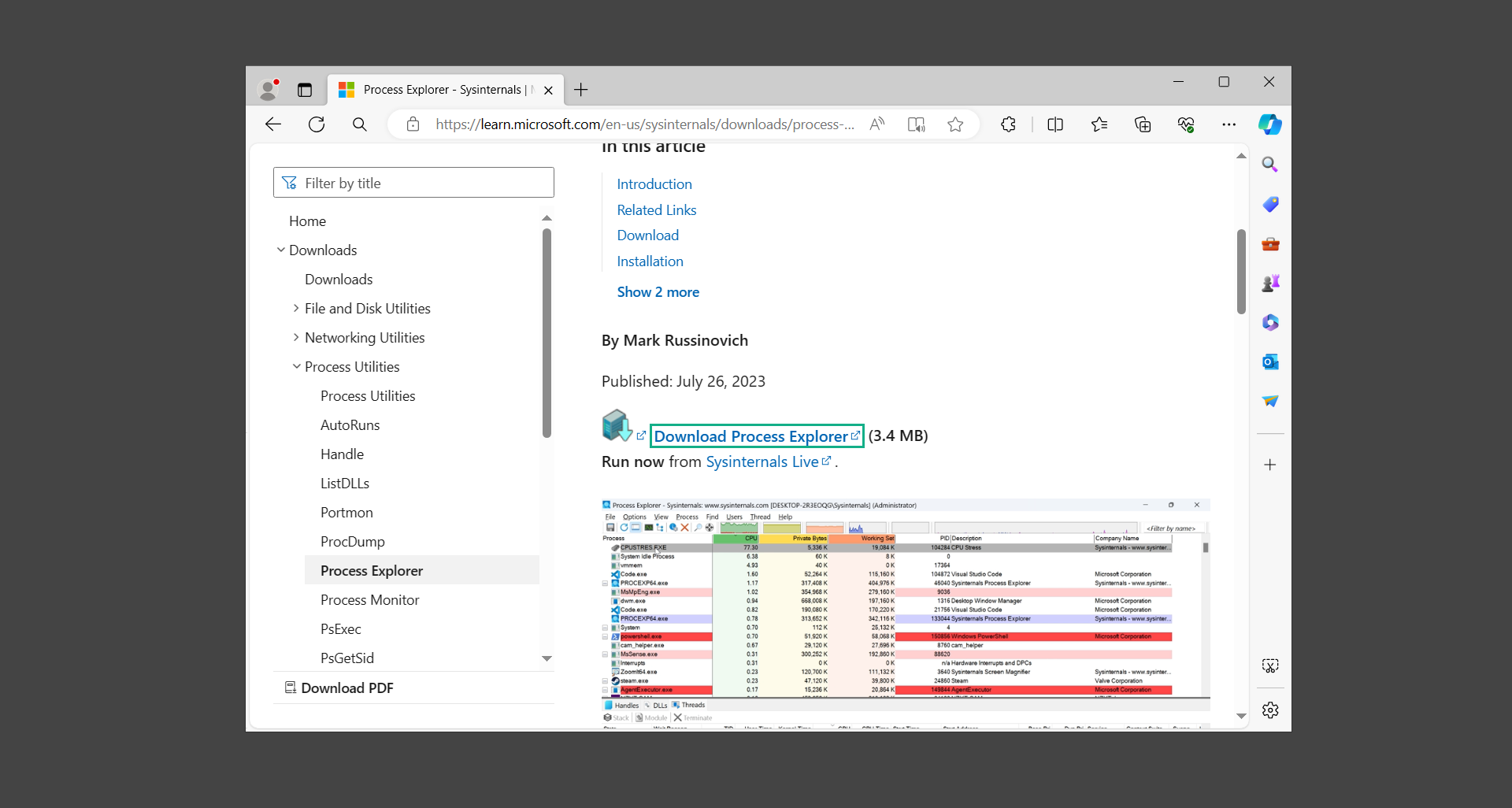
New ObjectsDeleted ObjectsOwn ProcessesServicesSuspended ServicesPacked ImagesRelocated DLLsJobs.NET ProcessesImmersive Processes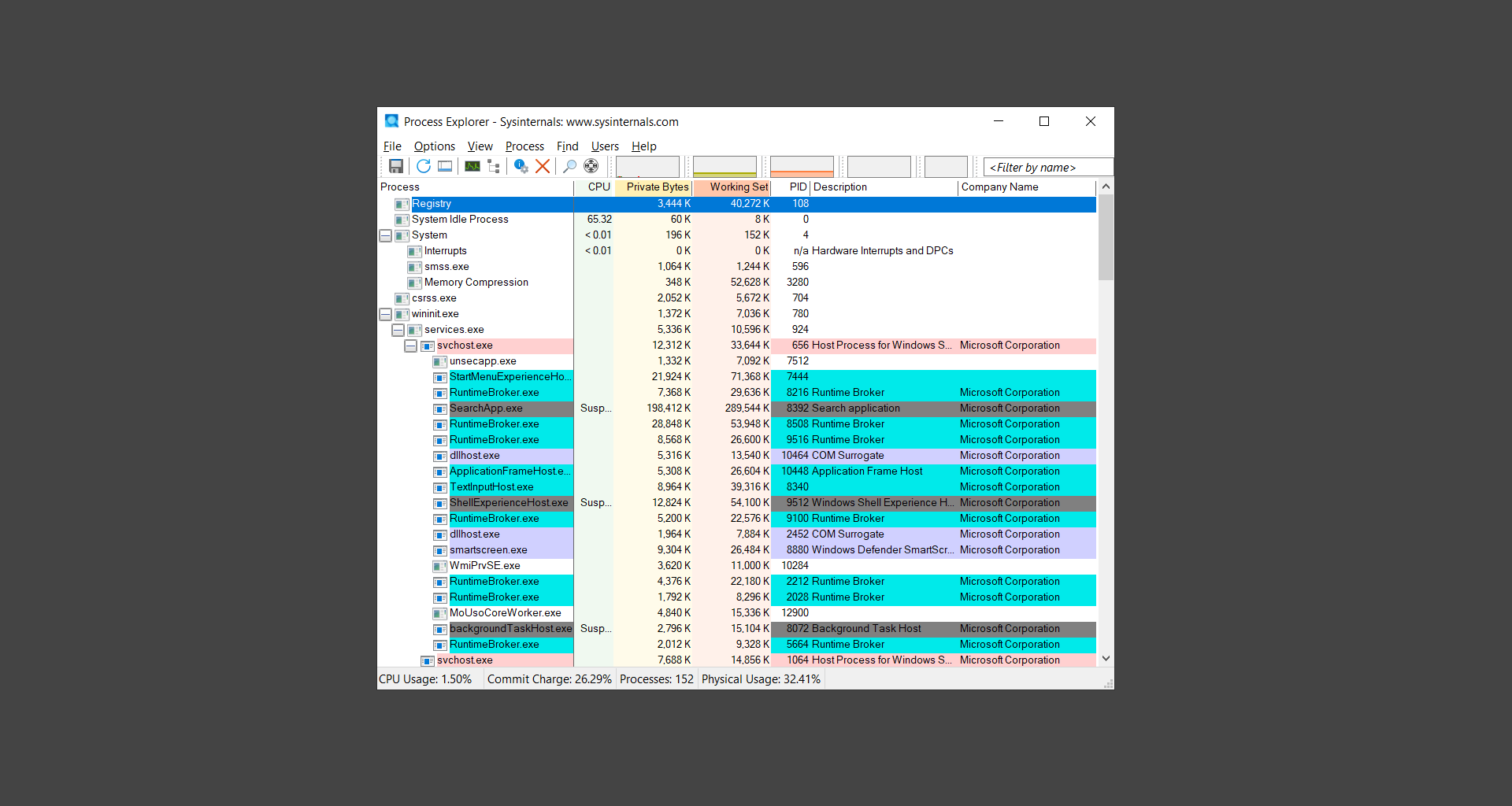
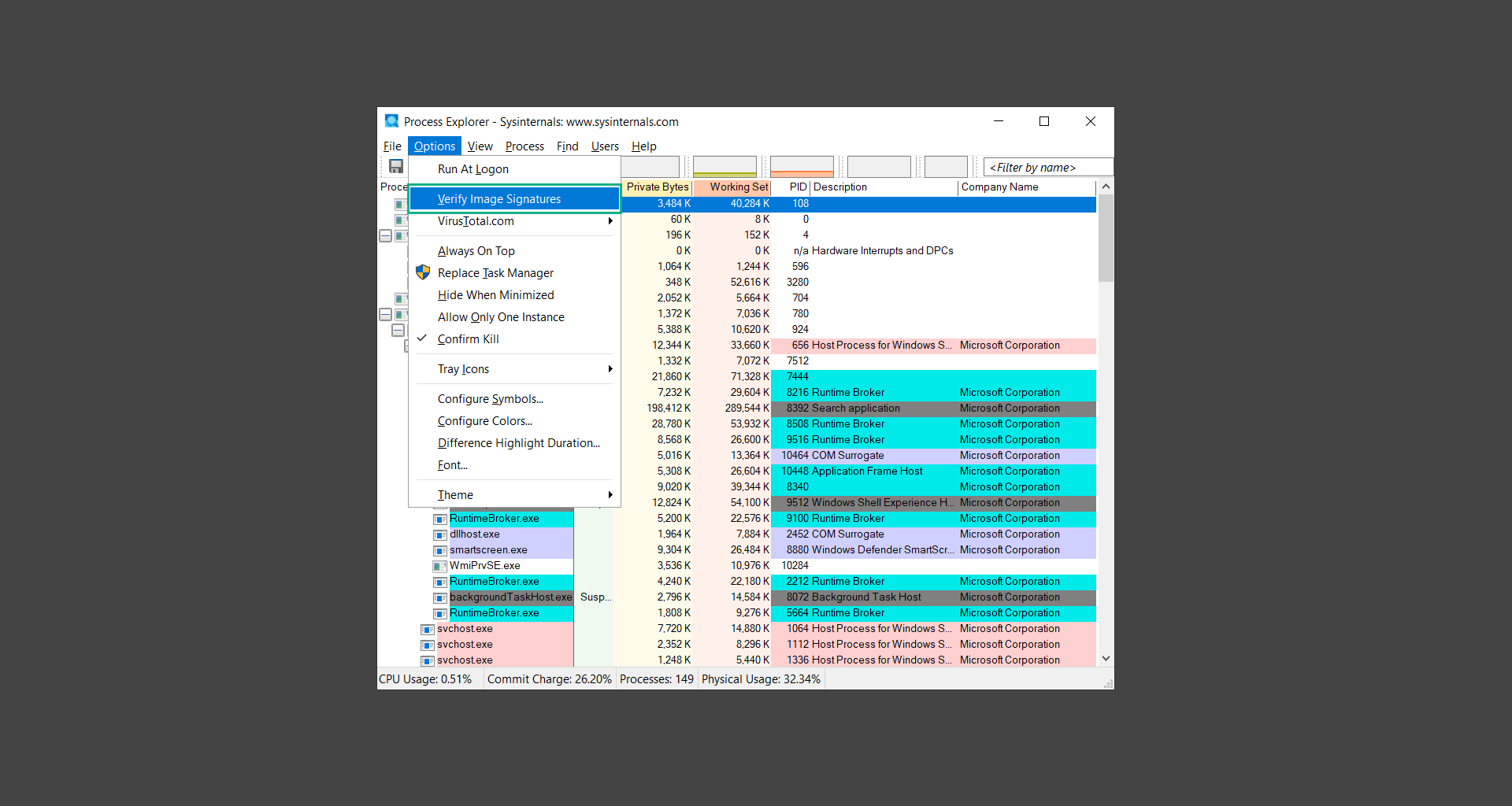
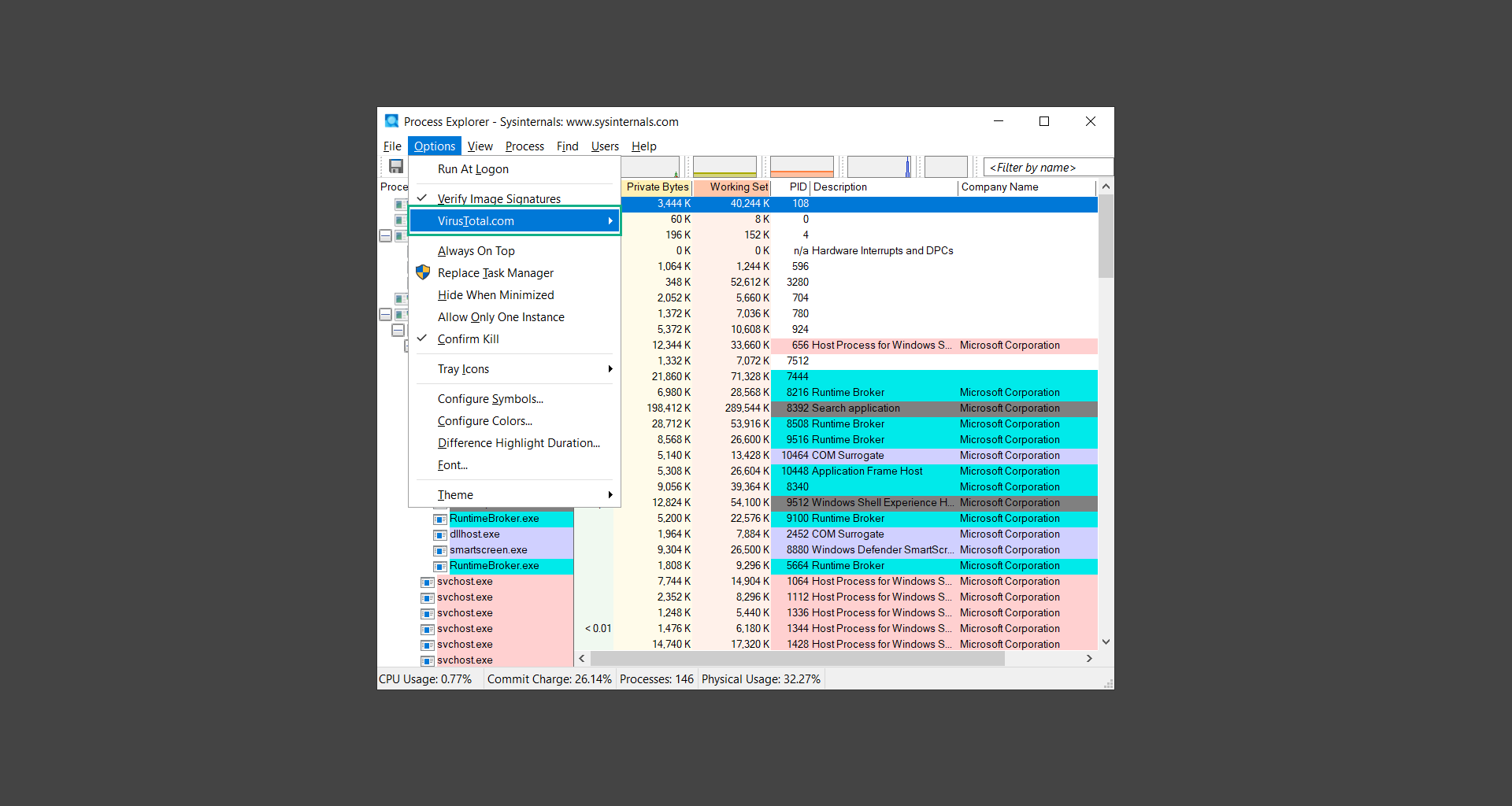
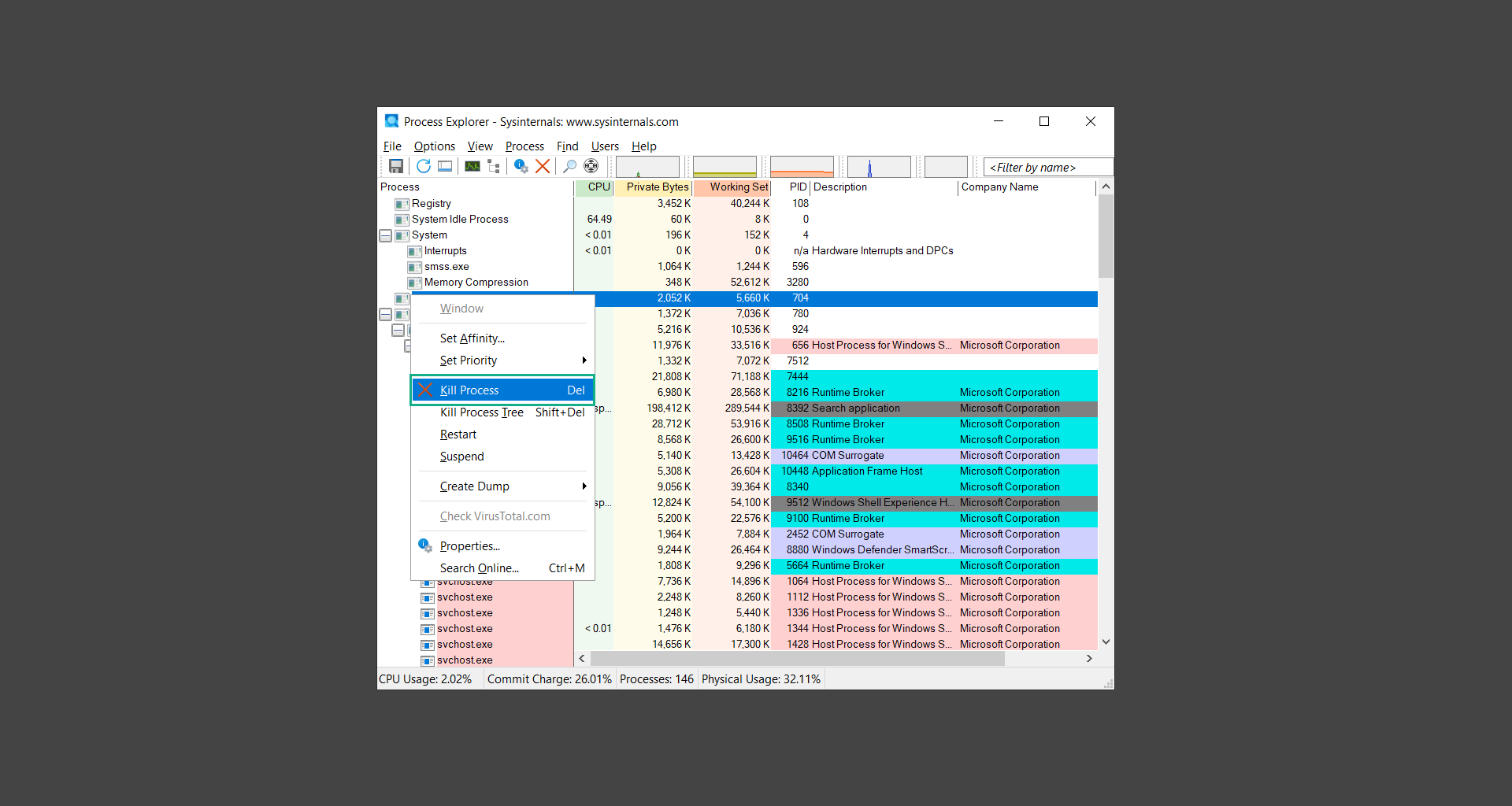
Step 2: Find and remove startup malware with Autoruns
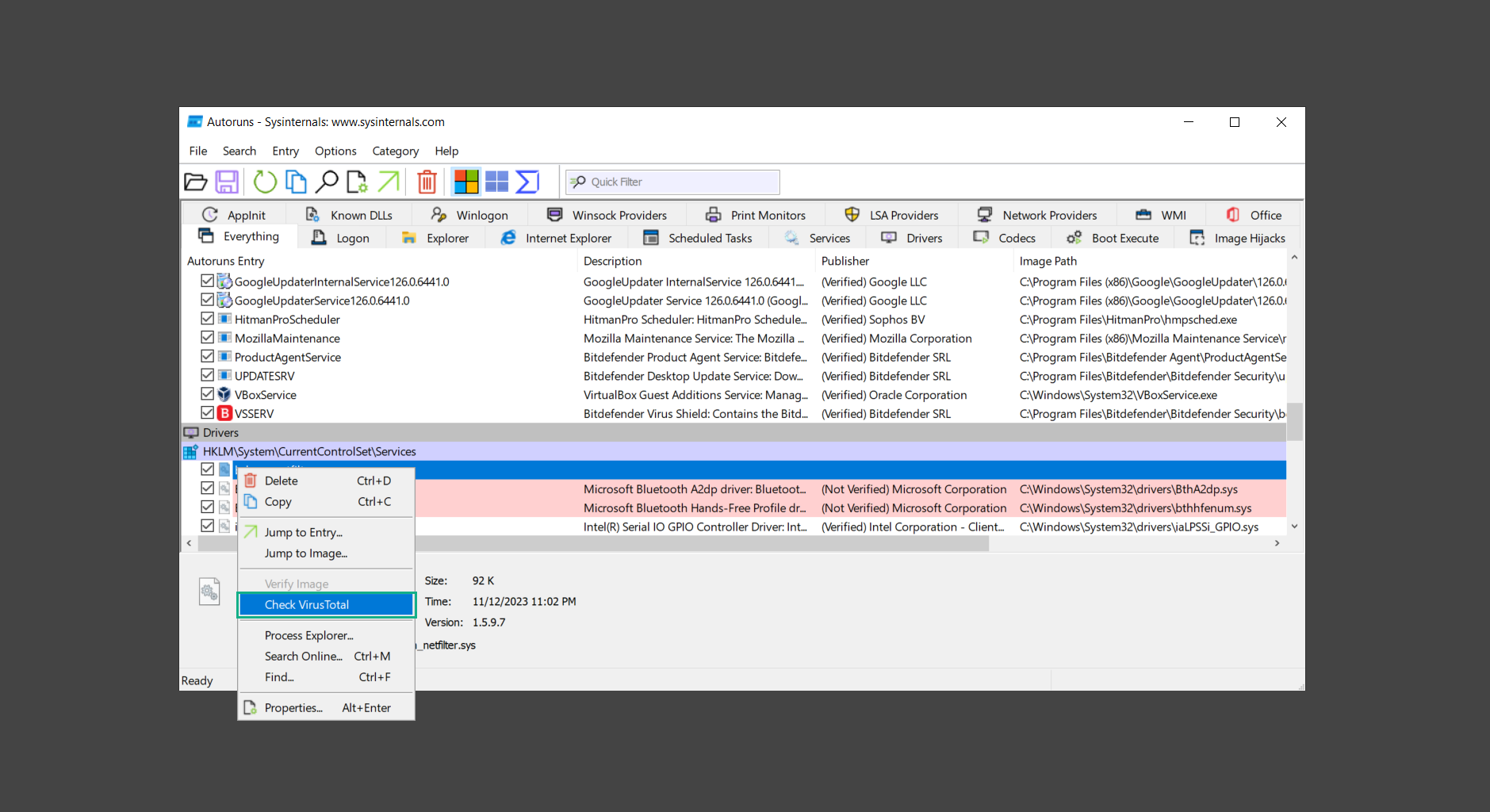
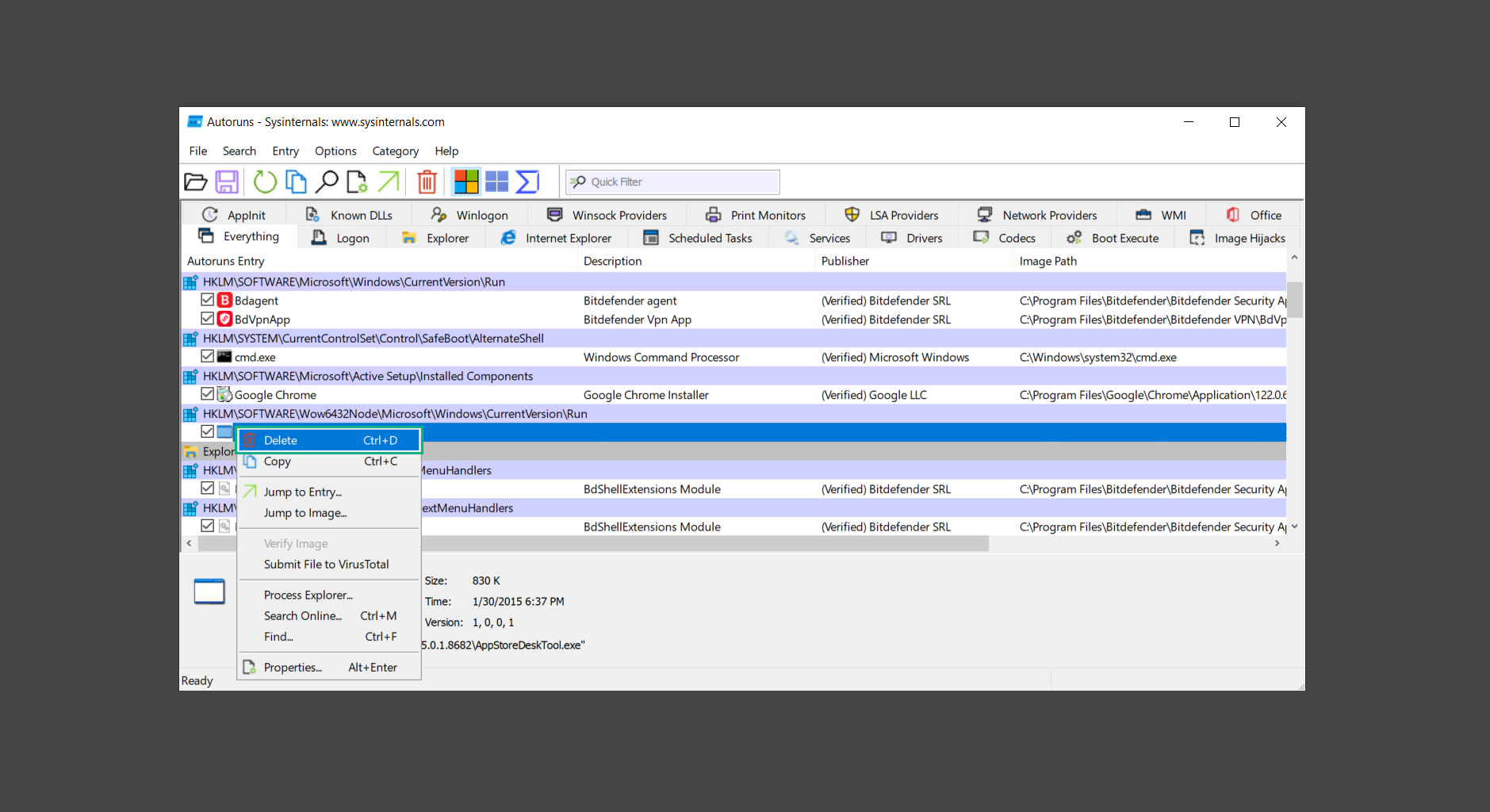
Step 3: Utilize Norton Power Eraser
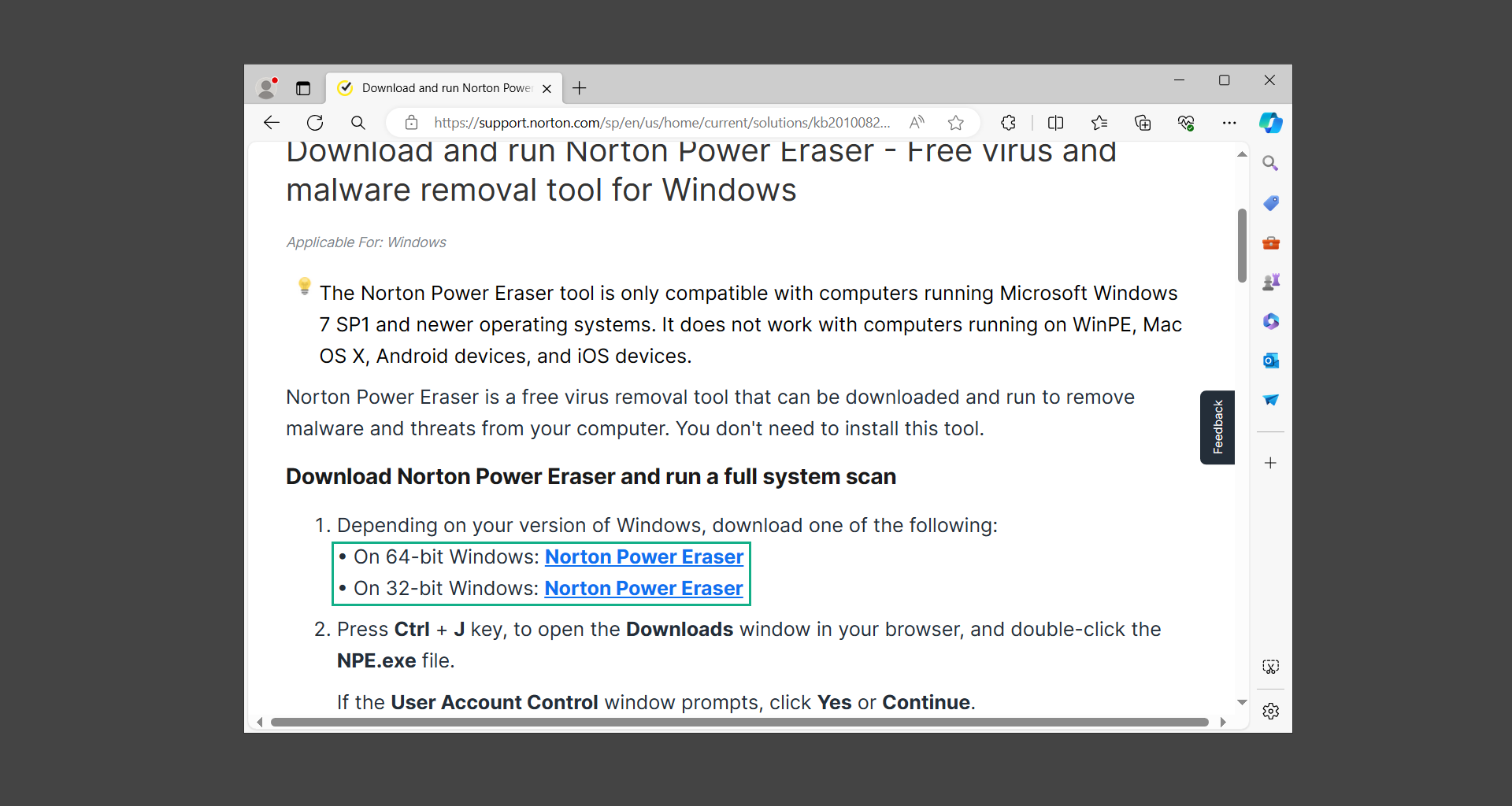
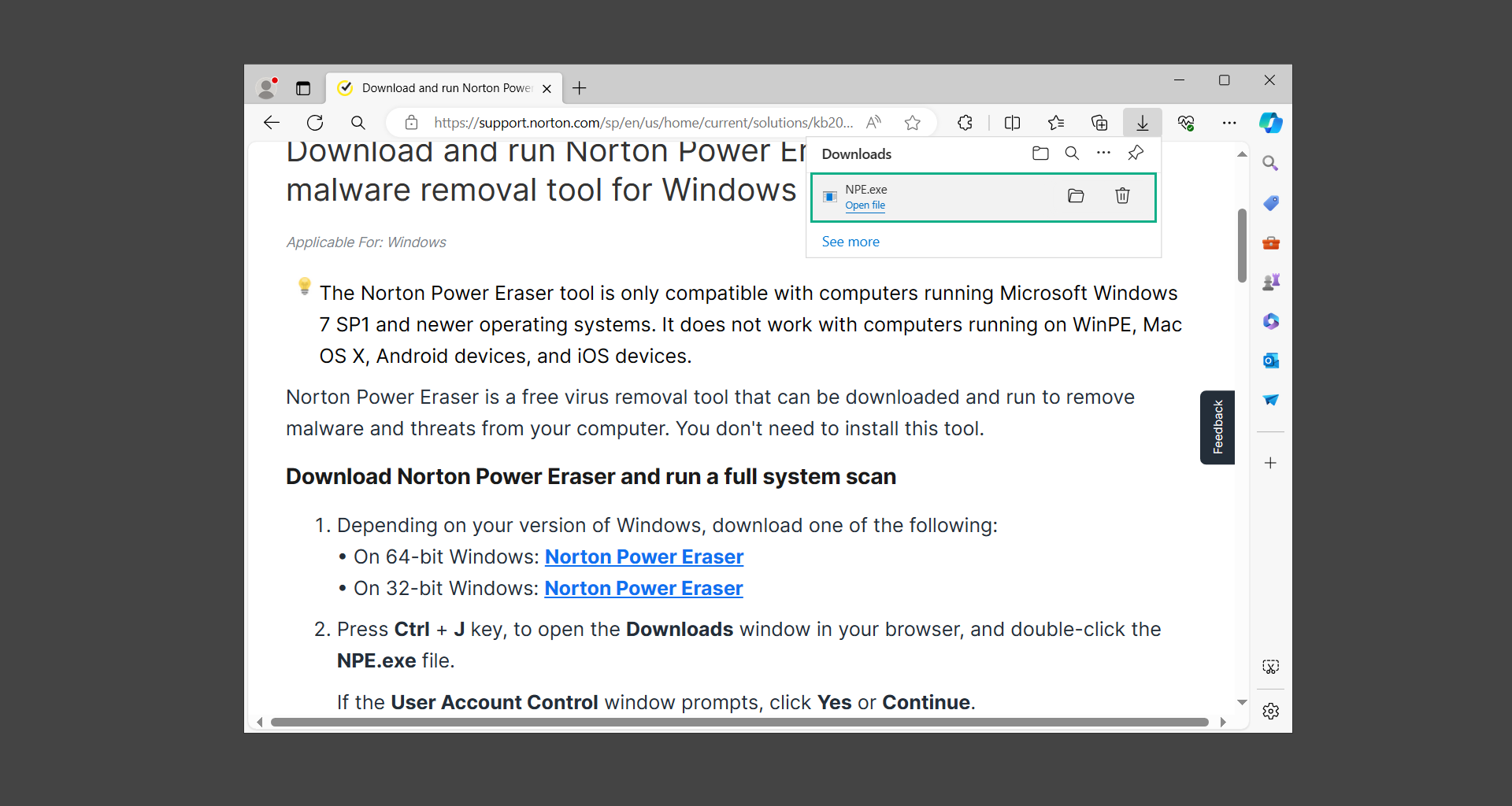
Step 4: Run the Tron script

Malware protection tips
Keep every software installed up to date
Avoid downloading files from unknown sources
Be careful with opening email attachments
Do not visit unreputable websites
